Phishing kits that bypass MFA protection are growing in popularity
The increased use of multi-factor authentication (MFA) has pushed developers of phishing kits to come up with ways to bypass that added account protection measure.
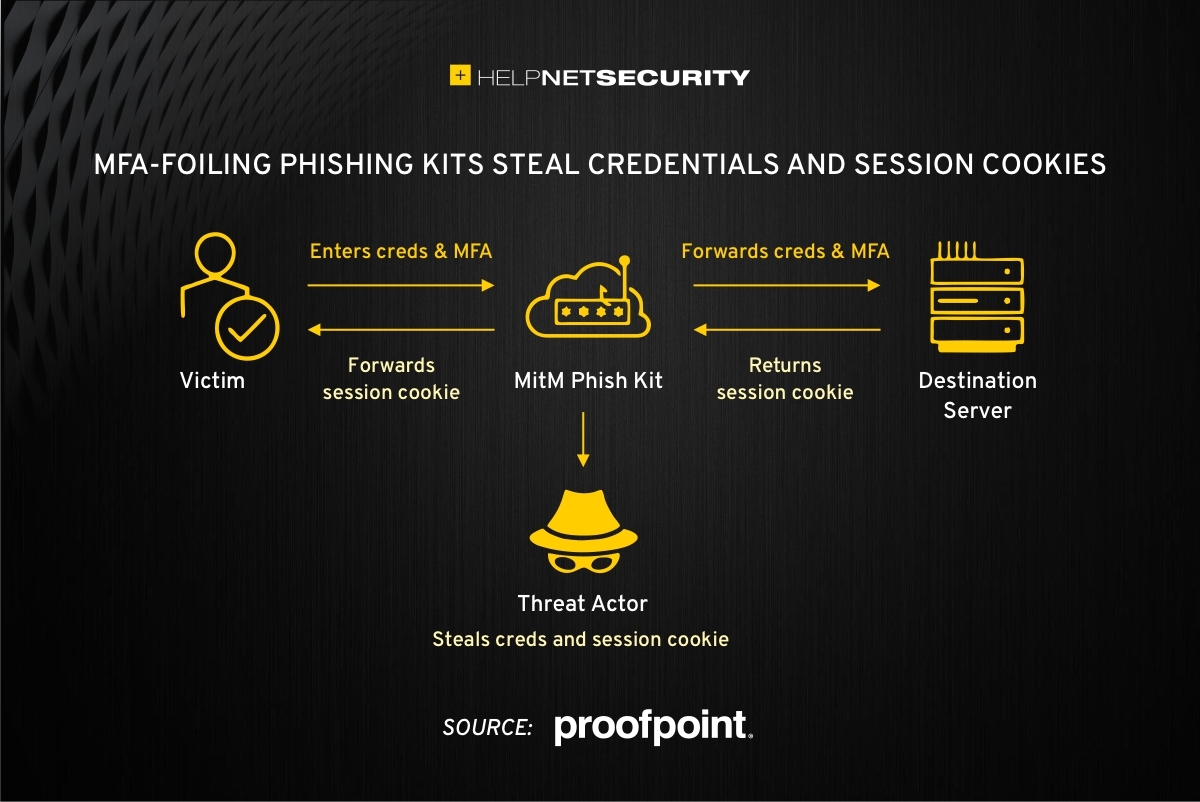
A current popular solution? Phishing kits that use a transparent reverse proxy to present the actual target website to the victim and allow attackers to capture the username and password entered by the victims AND the session cookie.
Phishing kits to bypass MFA protection
Proofpoint researchers have flagged three such phishing kits: Modlishka, Muraena/Necrobrowser, and Evilginx2.
Using them couldn’t be simpler: They are installed on a server controlled by the attacker, and the reverse proxy – an application that “sits” in front of the server and forwards browser requests to it and vice versa – fetches and delivers the legitimate login page to the victim. Simultaneously, the attacker sniffs the traffic passing through the proxy to extract the login credentials and the session cookie from the captured session.
“The session cookie can then be used by the threat actor to gain access to the targeted account without the need for a username, password, or MFA token,” the researchers explained.
Each of the those phishing kits has its specificities.
Muraena/Necrobrowser, for example, is a combination of a proxy (Muraena) and a headless browser (Necrobrowser) that can immediately use the captured session cookies to log into the target site wreak havoc: change the account password, dump emails, disable Google Workspace notifications, change SSH session keys in GitHub, and download all code repositories. (Phishers are, generally, after more than just email accounts – they also target online banking accounts, GitHub accounts, social media accounts, and so on).
The researchers predict that these and other similar phishing kits will become more popular as the time passes, spurred by the increasing adoption of MFA and the fact that phishing pages using a transparent reverse proxy to MitM credentials are more likely to remain unblocked for a longer time than “regular” phishing pages.
Citing recent research results by researchers from Stony Brook University and Palo Alto Networks, Proofpoint pointed out that standard phishing sites had a lifespan of just under 24 hours while MitM phishing sites last longer, and that a non-negligible percentage (15%) of the latter have been found to last more that 20 days.