Modernizing data security with a zero trust approach to data access
In a world where we can no longer trust anyone, zero trust security has picked up momentum, especially since 2018 when NIST published Implementing a Zero Trust Architecture. With breaches at all time high and ever-increasing sophistication in cyberattacks, it is no wonder that Gartner estimates that by the end of 2022 spending on zero trust will hit $891.9 million, and projects that by 2026 it will reach $2 billion.

There is a practical zero trust model for data security every company can follow with such a model heeding data access at the start.
Zero trust architecture revisited
For those who may need a refresher, zero trust is a security framework calling for all users, regardless of where they are located – inside or outside the organization’s network – to be authenticated, authorized, and continuously validated before they can access applications and data. With the rise of the new hybrid and distributed workforce logging on from home and office locations around the world, users are commonly not accessing data or applications from a specific network segment. And, as more applications and data are SaaS-based or otherwise not part of a specific network perimeter, a different security model is needed.
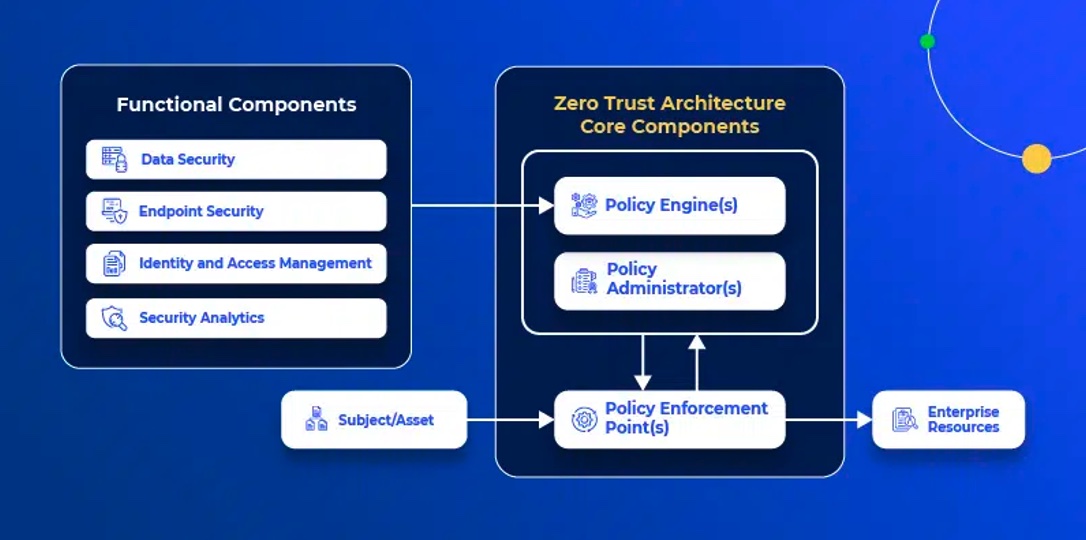
Zero trust architectures have the following components:
There is no single strategy for designing and implementing zero-trust security policies, as different companies have different goals, priorities, and are at different maturity levels in their data accessibility journey. For example, some organizations’ strategies are to enforce “need to know” policies, while others are moving to a “need to share” security posture.
Why take a unified zero trust approach for data access
There are many reasons why companies need to consider a unified, zero trust approach to their data access as part of their data protection strategy – both in terms of value and risk.
On the unified front, one of the functional components of the NIST zero trust architecture is data security, specifically defined as “all the data access policies and rules that an enterprise develops to secure its information, and the means to protect data at rest and in transit.”
Since most companies have sensitive data residing within their databases, data warehouses, or data lakes, it is imperative that every company looks to control and secure access to all such sensitive data across their distributed environments. In many instances, organizations are facing increasing numbers of data users (a trend commonly referred to as data democratization), which in turn presents a big opportunity – to generate more business value, for example, and an additional security risk due to the lessening of controls over who accesses the sensitive data, and when. Therefore, every enterprise needs to have clear and deterministic data security and data access policies to ensure data is stored, processed, accessed, used and shared in a secure way.
How to apply a unified and continuous zero-trust model to data access
Regardless of the organization’s approach to zero trust, to follow the zero trust principle, every organization must continuously validate users who need access to data – i.e., continuously authenticate, authorize and validate users across all data sources.
Let’s explore these three dimensions in more detail:
- Continuous authentication entails verifying the identity of every user every time they access data. Authentication can be done in many ways, using database credentials, using key-pair authentication, or through Single Sign-On (SSO) with an Identity Provider (IdP) such as Okta or MSFT Active Directory. Here’s a common reality: All organizations need to enable data analysts to access data in production. The typical path most organizations follow is to either a) provide constant access to the data, or b) have one user sign-in, which in turn is shared by many within the given department to access the production data. The practical zero-trust approach in this case is to provide temporary access to the data on an as-needed basis.
- Continuous authorization involves verifying, once a user is authenticated, what data a user can access. Authorization is a major challenge, especially at scale. On one hand, the more data you authorize, the more security risk you assume. On the other, you want users to have access to all the data they need. The practical approach to zero-trust authorization is to consolidate authentication across platforms and implement real-time authorization based on the varying needs of your data consumers. This requires getting a firm handle on the different datasets every user can access, real- or near-time access request and granting; alongside managing temporary access or access no longer needed by revoking it across datastores.
- Continuous validation needs to ensure that no excess risk is assumed, and that data is used in the way it’s intended. Examples of this type of validation are applying anonymization policies such as data masking policies and data localization, among others. From there, organizations need to look for ways to apply the organization’s data security policies continuously across all data access, and across all data platforms. Having a unified approach to data access policies will not only ensure their consistent enforcement, but it will also enable seamless monitoring and auditing for any hidden or new risks and adequate response to privacy and compliance regulations.