StackHawk empowers security teams to expand their API testing coverage
StackHawk releaseed LLM-Driven OpenAPI Specifications, a powerful new capability that creates API documentation directly from source code, empowering security teams to expand their API testing coverage without relying on developers. This automation delivers faster, more accurate vulnerability scanning while enabling security teams to take ownership of their testing initiatives.
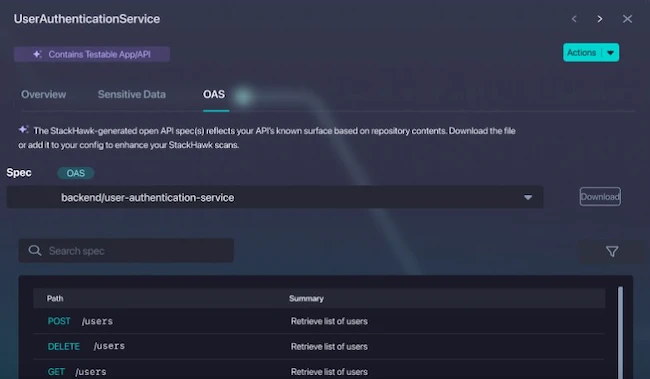
With this new capability, StackHawk analyzes source code repositories, extracts API details using homegrown LLMs, and produces accurate OpenAPI specifications automatically. These specs, which are critical text files that describe available API endpoints and functionality, can then be leveraged by AppSec teams to intelligently scan APIs for vulnerabilities.
“AppSec teams need OpenAPI specs to begin testing their APIs, but traditionally depend on developers to manually write and maintain them, which can be a huge bottleneck,” said Scott Gerlach, Co-Founder & CSO at StackHawk. “By auto-generating these specs directly from source code, we’re putting security teams in the driver’s seat, giving them the ability to identify and test APIs immediately, while simultaneously taking the manual work off the plates of developers.”
APIs are now the dominant attack surface in modern applications, and dynamic testing is one of the most effective ways to find real, exploitable vulnerabilities. Unlike static scanning or perimeter defenses, modern DAST tools like StackHawk simulate real-world attacks against running services to uncover issues such as broken authentication, excessive data exposure, and improper error handling.
But without accurate documentation these tests can’t begin, leaving critical parts of the application stack unprotected. A recent StackHawk customer survey revealed that 85% of users cited lack of OpenAPI specs as a major barrier to testing APIs. Legacy systems, acquired codebases, and undocumented shadow APIs all contribute to significant blind spots in application security. Creating the necessary specs manually is time-consuming and often deprioritized, leaving AppSec teams stuck waiting for engineering resources that are often stretched thin.
Unlike legacy tools that rely on production network traffic to infer API behavior, which miss endpoints that lack activity or are deployed in non-standard ways, StackHawk’s new feature pulls directly from code and continuously updates as the codebase changes. This enables faster setup and onboarding, more comprehensive test coverage, and protection for low-traffic or dormant APIs that often go unmonitored or unpatched.
Key benefits of StackHawk’s auto spec generation:
- Enables testing: Unblocks security scans for undocumented APIs
- Finds more surface: Captures shadow APIs and hidden endpoints
- Reduces engineering burden: No need for developers to manually write specs
- Scales AppSec: Expands security coverage without slowing down teams
“It’s working phenomenally – better than expected,” said Lake Sester, InfoSec Lead at Community America Credit Union. “We’re getting more accurate results than our current specs, with zero false positives and faster scans.”