Zscaler, Palo Alto Networks, SpyCloud among the affected by Salesloft Drift breach
In the wake of last week’s revelation of a breach at Salesloft by a group tracked by Google as UNC6395, several companies – including Zscaler, Palo Alto Networks, PagerDuty, Tanium, and SpyCloud – have confirmed their Salesforce instances were accessed.
The companies noted that attackers had only limited access to Salesforce databases, not to other systems or resources. They warned, however, that the stolen customer data could be used for convincing phishing and social engineering attacks.
The Salesloft breach
Salesloft is the company behind a popular sales engagement platform of the same name.
The company’s Drift application – an AI chat agent – can be integrated with many third-party platforms and tools, including Salesforce.
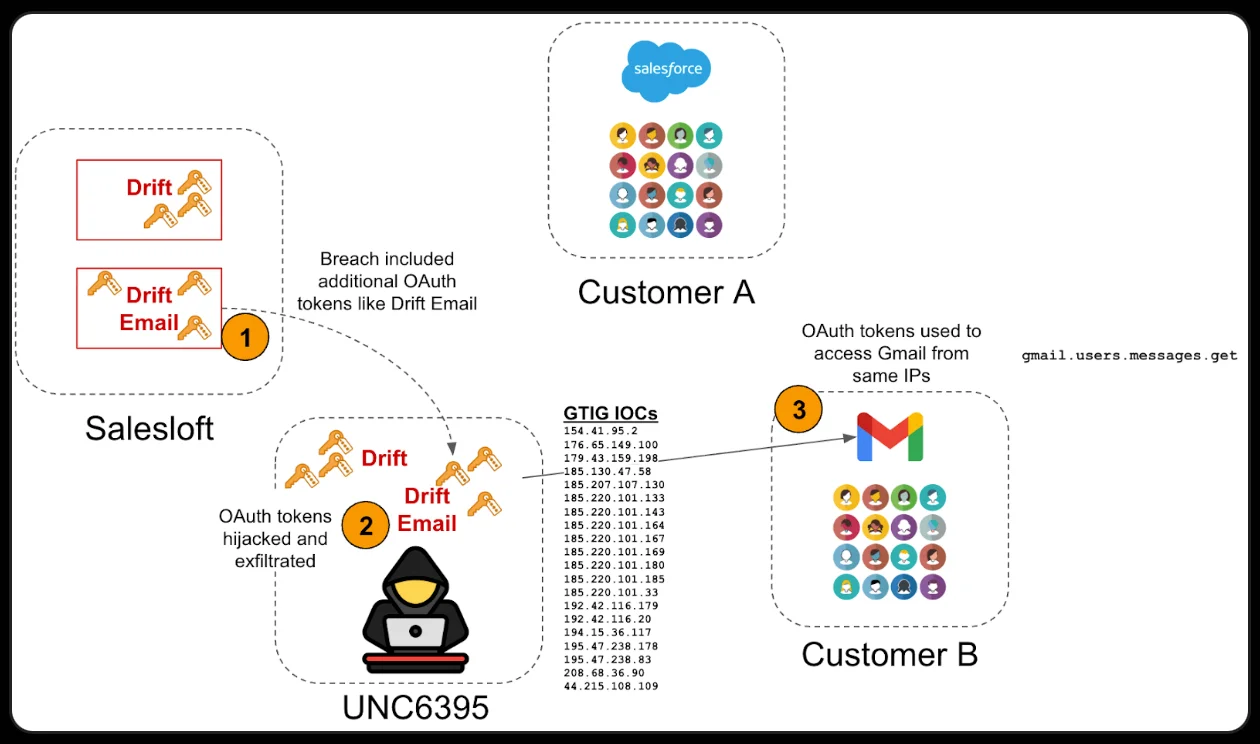
On August 26, Salesloft stated that from August 8 to August 18, 2025, attackers used compromised OAuth credentials to exfiltrate data from the Salesforce instances of customers that have set up the Drift-Saleforce integration.
Several days later, the Google Threat Intelligence Group (GTIG) confirmed that the compromise impacted other integrations, as well.
“On August 28, 2025, our investigation confirmed that the actor also compromised OAuth tokens for the ‘Drift Email’ integration. On August 9, 2025, a threat actor used these tokens to access email from a very small number of Google Workspace accounts,” GTIG analysts shared.
Astrix Security researchers have confirmed that the attackers used the Drift Email OAuth application for Google Workspace to exfiltrate emails and that – at least in one case – they tried to access S3 buckets whose names have been likely extracted from compromised Salesforce environments.
Similarly, WideField threat researchers have observed suspicious log event activity across multiple customers using its security platform, pointing to attackers rifling through Salesforce databases and Gmail accounts.
How UNC6395 accessed emails (Source: WideField)
Zscaler, Palo Alto Networks and the other companies mentioned above are just some of the 700+ companies impacted by this breach.
While the stolen customer information can be valuable, GTIG analysts say that the attackers were focused on searching for AWS access keys, passwords, and Snowflake-related access tokens, which can (and likely have been) further misused by the attackers.
What to do if your organization is on the victims list?
Salesloft has yet to reveal how the attackers managed to get their hands on the OAuth tokens they used, but the company has engaged cybersecurity experts from (Google’s) Mandiant and Coalition to help them investigate and remediate the compromise.
“We are recommending that all Drift customers who manage their own Drift connections to third-party applications via API key, proactively revoke the existing key and reconnect using a new API key for these applications. This only relates to API key-based Drift integrations. OAuth applications are being handled directly by Salesloft,” the company said on August 27, and outlined the process for updating the API keys.
Salesforce has, for the moment, disabled all integrations between Salesforce and Salesloft technologies, including the Drift app.
“Disabling the connection is a precautionary measure to help safeguard customer environments while we continue to assess and address the situation. We recognize this change may cause disruption and will provide further updates as more information becomes available,” the company noted.
Likewise, Google has disabled the integration functionality between Google Workspace and Salesloft Drift pending further investigation, and has advised organizations to “review all third-party integrations connected to their Drift instance, revoke and rotate credentials for those applications, and investigate all connected systems for signs of unauthorized access.”
Google Mandiant incident responders have provided extensive advice on how organizations can investigate for compromise and scan for exposed secrets and hardcoded credentials.
Astrix researchers have shared additional indicators of compromise and described AWS-specific activity to look out for. WideField threat analysts have provided guidance useful to both their customers and other affected organizations.
UPDATE (September 4, 2025, 05:40 a.m. ET):
Cloudflare, Tenable, Proofpoint and Rubrik have also been affected. Cloudflare has released a detailed post-mortem on what the attackers did when they accessed their Salesforce instance, as well as indicators of compromise.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!