Nosey Parker: Open-source tool finds sensitive information in textual data and Git history
Nosey Parker is an open-source command-line tool that helps find secrets and sensitive information hidden in text files. It works like a specialized version of grep, focused on spotting things like passwords, API keys, and other confidential data.
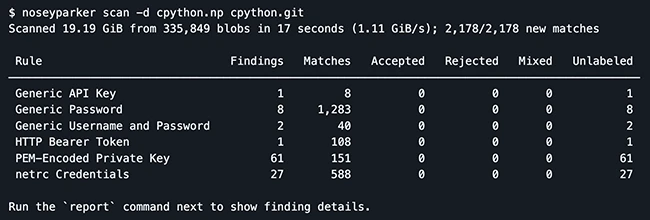
The tool was built with offensive security in mind, such as helping red teams move through systems during tests. It’s also useful for defensive teams checking their own systems. Offensive cybersecurity company Praetorian has used it in hundreds of security engagements to uncover hidden secrets.
Key features:
- Flexible scanning: Works on files, folders, GitHub repositories, and Git history. It also supports custom input sources.
- Proven detection rules: Uses 188 tested regular expression rules, built from feedback by security engineers, to cut down on false positives.
- Less noise: Groups duplicate matches of the same secret, making reviews 10 to 1,000 times faster.
- High performance: Can scan gigabytes per second on multicore machines and handle datasets as large as 20TB.
Typical workflow:
1. Scan – Run the scan command to check files or repositories.
2. Report – Generate a summary of the results with the report command.
3. Review – Go through the findings to confirm which ones need action.
Nosey Parker is available for free on GitHub.

Must read:
- 35 open-source security tools to power your red team, SOC, and cloud security
- GitHub CISO on security strategy and collaborating with the open-source community

Subscribe to the Help Net Security ad-free monthly newsletter to stay informed on the essential open-source cybersecurity tools. Subscribe here!
