Can your earbuds recognize you? Researchers are working on it
Biometric authentication has moved from fingerprints to voices to facial scans, but a team of researchers believes the next step could be inside the ear. New research explores how the ear canal’s unique acoustic properties can be used to verify identity through wireless earbuds. Their system, called EarID, shows that ear canal scanning could one day become a practical security method for mobile devices.
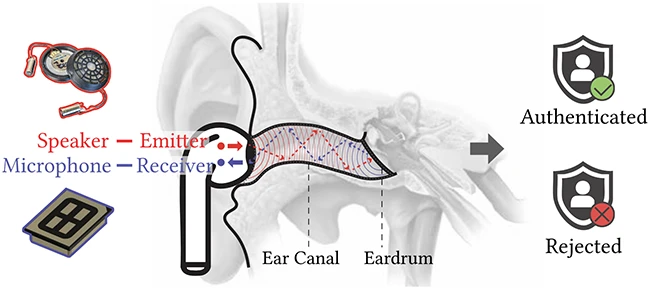
Illustration of ear canal scanning/sensing. The user inserts the earbuds to run ear canal scanning, acoustic sensing the unique ear canal structure, for biometric user authentication.
Turning the ear canal into a security key
Each person’s ear canal produces a distinct acoustic signature, so the researchers behind EarID designed a method that allows earbuds to identify their wearer by using sound. The earbuds emit acoustic signals into the user’s ear canal, and the reflections from that sound reveal patterns shaped by the ear’s structure.
What makes this study stand out is that the authentication process happens entirely on the earbuds themselves. The device extracts a unique binary key based on the user’s ear canal shape and then verifies that key on the paired mobile device. By working with binary keys instead of raw biometric data, the system avoids sending sensitive information over Bluetooth. This helps prevent interception or replay attacks that could expose biometric data.
A simpler alternative to machine learning
Previous studies on ear canal biometrics relied on machine learning models trained on ear scan data to tell users apart. While accurate, those approaches are demanding for earbuds, which have limited computing power and battery life. EarID takes a different route. Instead of training a classifier, it uses a learning-free key extraction process.
The earbuds analyze the sound reflections, convert them into frequency and cepstral features, and then transform these features into a short binary key. This key represents the wearer’s unique ear pattern. Verification on the mobile device is handled with a privacy-preserving technique called fuzzy commitment. In this setup, the earbuds send a coded message to the mobile device, and the phone checks whether it matches the stored user key. The raw data never leaves the earbuds.
This lightweight design reduces the computing load while keeping accuracy high. In testing, EarID achieved an authentication accuracy of about 98.7 percent.
Real-world testing and performance
To validate the system, the researchers built a custom testbed since commercial earbuds do not yet allow access to in-ear microphone data. They embedded miniature microphones into regular earbuds to collect ear canal reflections and then evaluated how well EarID could tell users apart.
The experiments involved 44 participants from a university campus. The system maintained a false acceptance rate under 1 percent, meaning that impostors were almost never granted access. The processing times were short: about 160 milliseconds for mobile enrollment and 226 milliseconds for earbuds authentication. The study also tested the method’s resilience against different attack scenarios, including synthetic ear models and key guessing, and all resulted in very low success rates for attackers.
Built for small devices
A key part of the research is showing that earbuds can handle biometric processing without large hardware or cloud support. EarID runs on a small microcontroller comparable to those found in commercial earbuds. The researchers measured performance on an Arduino platform with an 80 MHz chip and found that it could perform the key extraction in under a third of a second.
For comparison, traditional machine learning classifiers took three to ninety times longer to train and process data. This difference could make a real impact if ear canal authentication ever reaches consumer devices, since users expect quick and seamless authentication.
Addressing privacy and usability
EarID’s design aims to protect biometric privacy. Since the earbuds never send raw ear canal data, intercepted Bluetooth traffic would not reveal identifiable information. This approach also reduces the risk of biometric data being reused for unauthorized access.
Chenpei Huang, Ph.D., a co-author of the paper, told Help Net Security that protecting users will depend on how much access developers are given once earbuds expose in-ear microphones. “Once in-ear microphones are opened to developers, anyone could potentially access the acoustic response of the ear canal, which might reveal personal information,” he said. “To protect users, smart devices would need strict access control, similar to what is already used for front-facing cameras. Only trusted apps that truly need in-ear data should be allowed to access it.”
He added that raw biometric data should never be exposed to third-party apps. “Protection must also come from other layers, such as liveness detection, to ensure that only real, present human users can be authenticated,” he said. “As for the keys generated by EarID, they should be stored securely in hardware-protected areas such as Apple’s secure enclave.”
The study also examined the user experience. The team measured how noticeable the authentication sound was, using psychoacoustic models and participant surveys. The signals, which last about one second, were rated as mildly noticeable but not irritating. While the researchers tested audible signals, they noted that the method could also operate with inaudible frequencies, which might be useful for continuous authentication.
Adapting to the noise of daily life
In controlled tests, EarID worked well, but real-world environments bring new challenges. Huang acknowledged that movement, speech, and background noise can influence the acoustic signal. “In-ear sound can indeed change when the user is talking or moving around because your own voice and body sounds get amplified by the sealed earbud,” he said. “In practice, authentication only takes about one to two seconds, so users could simply pause their music or stop talking briefly during login.”
He added that the system could adjust dynamically in future designs. “The system can also help with that automatically by dimming the sound and playing a short notification when it is time to authenticate,” Huang explained. “Since users often wear earbuds continuously, the system could also give partial access when the environment is noisy and grant full access once conditions become stable.”
Where this could lead
EarID is still a research prototype, but the concept points to new directions for wearable security. The team notes that collecting more ear canal data from diverse users will be important for improving accuracy. They also suggest future improvements such as testing alternative error-correction codes and expanding the approach to other in-ear sensing applications.
This research highlights how biometric innovation is moving toward more personalized and less intrusive methods. The combination of privacy preservation, low power use, and near-instant processing could make ear-based authentication attractive in environments where convenience and security must coexist.
If commercial earbuds eventually expose their in-ear microphones to developers, systems like EarID could add a new biometric layer for mobile authentication. Instead of typing a password or scanning a fingerprint, users could simply put in their earbuds, and the device would know who they are by the sound of their own ear canal. As someone who wears Apple AirPods Pro all the time, it would be great to have this type of tech inside.