Italian-made spyware Dante linked to Chrome zero-day exploitation campaign
CVE-2025-2783, a Chrome zero-day vulnerability that was detected being exploited in March 2025 and was subsequently fixed by Google, was used by unknown attackers to deliver LeetAgent, suspected commercial spyware.
An analysis of the malware’s code and the campaign’s infrastructure led Kaspersky researchers to uncover additional attacks by the same threat actor against organizations and individuals in Russia and Belarus. The researchers also uncovered another spyware tool used in some of these intrusions: Dante, commercial surveillance software developed by the Italian company Memento Labs (formerly Hacking Team).
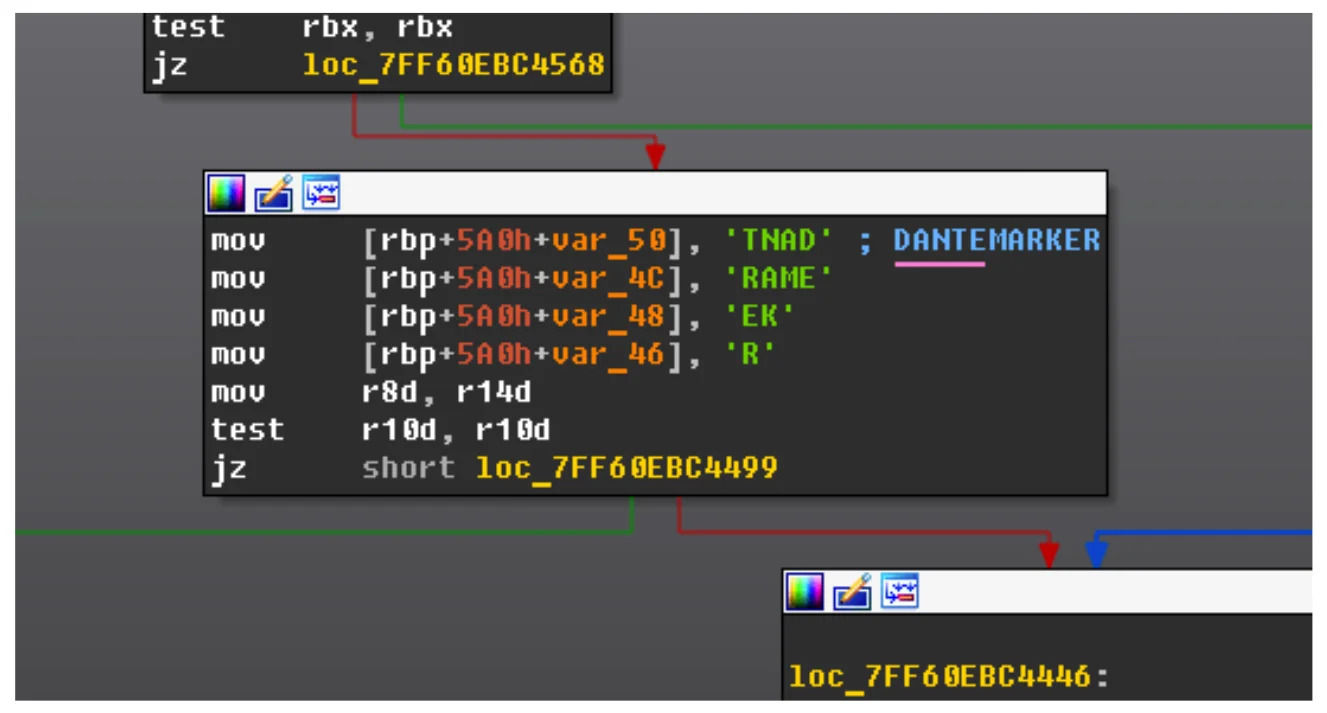
Dante’s code contains the name (Source: Kaspersky)
Operation ForumTroll
The March campaign, dubbed Operation ForumTroll for its use of fake invitations to the Primakov Readings forum, targeted Russian media outlets, universities, research institutions, government bodies, financial organizations, and other entities.
The invitations contained a link to a malicious website, with a validator script that would check whether it should continue the attack, i.e., serve a RCE and a sandbox escape exploit. The exploit would trigger the download of a persistent malware loader, which decrypts and executes the LeetAgent spyware.
While the researchers were unable to identify the remote code execution exploit for Google Chrome, they did manage to analyze the sandbox escape one, which leveraged CVE-2025-2783.
“This exploit genuinely puzzled us because it allowed attackers to bypass Google Chrome’s sandbox protection without performing any obviously malicious or prohibited actions. This was due to a powerful logical vulnerability caused by an obscure quirk in the Windows OS,” the researchers shared.
In effect, the attackers tricked Chrome’s inter-process communication (IPC) system into turning a pseudo-handle (a special Windows constant interpreted by the kernel as a handle to the current thread or process) into a real, usable handle inside the browser process, then used that handle to run code with the browser’s privileges.
The identity of the group behind the ForumTroll campaign is still unclear at this time. The phishing emails sent by the attackers are written in stylistically correct Russian, though some mistakes made in emails used in this and other campaigns attributed to the group suggest that the attackers are not native Russian speakers.
LeetAgent and Dante spyware
LeetAgent can receive commands from one of its C2 servers that make it run commands, execute processes, stop tasks, inject shellcode, read and write files, run keylogging and file-stealing tasks in the background, and more.
The C2 servers are specified in the configuration, and the number of traffic obfuscation settings points to LeetAgent being a commercial tool.
The researchers have analyzed past attacks that showed similarities and overlaps in indicators of compromise and techniques used, and have pinpointed another, more sophisticated spyware: Dante. (In some attacks, LeetAgeent was used to launch Dante.)
Dante uses VMProtect to hide its code, encrypt strings, and block debugging, and can detects sandboxes, virtual machines, and debuggers.
It calls Windows APIs indirectly to avoid detection by security tools, disguises its main controller (“orchestrator”) as a font file, loads (encrypted) plug-in modules from disk or memory, ties encryption keys to each infected machine, and deletes itself if it doesn’t receive commands after a set time.
“Until now, little was known about this malware’s capabilities, and its use in attacks had not been discovered,” Kaspersky researchers noted.
But the spyware sample analyzed by them not only contained the name, but also code similarities with Hacking Team’s RCS spyware (aka Da Vinci), making them pretty confident in attributing the malware to Memento Labs.
“Although we didn’t see the ForumTroll APT group using Dante in the Operation ForumTroll campaign, we have observed its use in other attacks linked to this group. Notably, we saw several minor similarities between this attack and others involving Dante, such as similar file system paths, the same persistence mechanism, data hidden in font files, and other minor details,” the researchers added.
“Most importantly, we found similar code shared by the exploit, loader, and Dante. Taken together, these findings allow us to conclude that the Operation ForumTroll campaign was also carried out using the same toolset that comes with the Dante spyware.”
Kaspersky has shared indicators of compromise that can be used to detect the presence of LeetAgent and Dante.
UPDATE (October 29, 2025, 08:20 a.m. ET):
Paolo Lezzi, Memento Labs’ chief executive, told Tech Crunch that the Windows spyware detected by Kaspersky researchers belongs to the company, but that they will stop supporting it by the end of this year and they will ask customers to stop using it.
At the moment, they are only developing mobile spyware, he added, and said that the Chrome zero-day exploit used in the attacks was not developed by the company.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!
