Chain of security weaknesses found in smart air compressor model
Contractors and workshops often rely on air compressors to power their tools and keep projects running. But when those compressors are connected to the internet, convenience can introduce new risks. Researchers at George Mason University found that the California Air Tools CAT-10020SMHAD smart air compressor contains a chain of security vulnerabilities that could allow an attacker to disrupt operations or tamper with usage data.
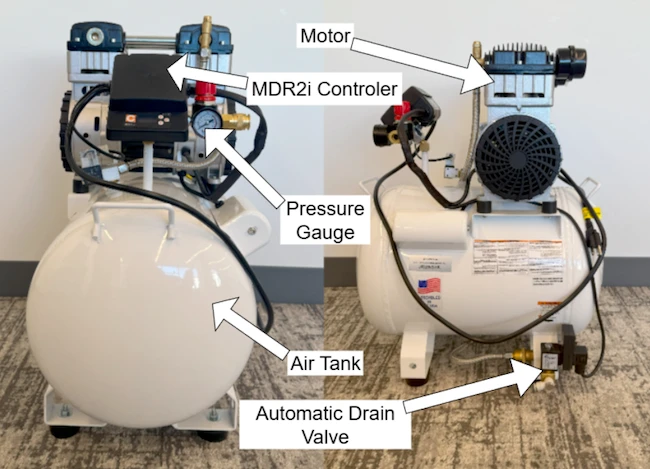
California Air Tools CAT-10020SMHAD smart air compressor with MDR2i wireless controller
From utility to attack surface
Compressed air is often called the fourth utility in manufacturing, alongside electricity, water, and natural gas. It powers refrigeration, pneumatic transport, and power generation. Because compressed air supports safety-sensitive operations, any disruption or tampering can cause line stoppages, pneumatic brake failures, or loss of pressure control that can damage equipment and endanger workers.
The California Air Tools CAT-10020SMHAD model includes a wireless controller called the MDR2i, which lets operators monitor pressure and control the compressor over Wi-Fi and install firmware updates through a web interface.
Researchers used this model to represent a class of connected industrial devices that combine mechanical reliability with digital control. Its analysis focused on how the controller handled authentication and remote access. To evaluate this, the researchers built a small test cell with a conveyor and pneumatic actuators that sorted packages. The compressor supplied air to this setup so the team could see how attacks affected production.
Building the threat model
Before launching attacks, the team built a threat model following ISA/IEC 62443 and NIST SP 800-82 standards. These frameworks guide how to analyze industrial control systems.
They assumed an attacker with limited resources but local network access, someone on the same Wi-Fi or LAN segment as the compressor. Physical access was not required. The analysis focused on preserving air supply availability, data integrity, and the confidentiality and authenticity of control commands.
This formal structure let the researchers map how each part of the device could be misused, from its wireless network to its firmware update mechanism.
Testing the device
The team tested the compressor in a lab network that mimicked an industrial environment using a Kali Linux laptop with a Wi-Fi adapter for wireless monitoring and packet injection.
They used Kismet and Wireshark for network discovery, traffic analysis, and packet capture. Burp Suite Professional intercepted and modified HTTP requests to the controller API, while custom Python scripts automated brute force and denial of service tests.
Initial testing revealed a weakness. The MDR2i controller’s Wi-Fi access point mode used a hardcoded password, “CATMDR2i,” printed in the user manual and unchangeable. Once connected, an attacker could reach the web interface without authentication.
In station mode the controller could be discovered with a basic network scan. The web console used plain HTTP so credentials and commands were sent in plaintext. Any device on the same network could intercept or alter that traffic.
Breaking the control plane
Beyond the unprotected network channel, the web interface itself had weak access control. The system included three roles: Operator, Manufacturer, and CPC, but all relied on shared, hardcoded four-digit PINs. There was no option to change them. The researchers confirmed they could brute-force these PINs in seconds since the login page lacked any limit on failed attempts.
More concerning, the web API allowed direct commands without authentication. Attackers could send HTTP requests to start or stop the compressor, change pressure thresholds, or trigger reboots. These actions did not need valid credentials and gave an attacker complete operational control of the compressor.
What happens when air stops
The team measured what happened when attackers used those unauthenticated endpoints. One test repeatedly sent reset commands, forcing the compressor into an endless reboot cycle. Another modified the pressure thresholds so that the compressor never turned on. Both attacks caused the pneumatic actuators in the test cell to stop working, halting the simulated production process.
Other attacks focused on data integrity. By manipulating calibration and zero-point settings, the researchers made the compressor report false pressure readings. On the monitoring screen, the digital twin showed stable pressure, while the analog gauge told a different story. That mismatch could cause automated systems to misjudge the process state, potentially damaging equipment or producing defects.
Fixing what went wrong
After demonstrating the attacks, the team proposed ways to prevent them. The recommendations follow well-known industrial cybersecurity principles but are often skipped in lower-cost IIoT devices.
Each compressor should ship with unique credentials, and users should be forced to change them on first use. The web interface should use HTTPS to protect traffic. All API calls that modify device state must require authentication and enforce user permissions. Firmware updates should include cryptographic signature checks and, ideally, hardware-based trust elements to prevent tampering.
They also suggested separating control functions, such as start and stop, from maintenance functions like sensor calibration. These should not share the same network channel. Such separation would prevent simple network attackers from reaching sensitive configuration areas.
The supply chain problem
The researchers traced the vulnerabilities back to how the device was built. The CAT-10020SMHAD was assembled from parts made by several companies. One focused on the compressor hardware, another on the controller electronics, and another on distribution. Each handled its own area, but none took ownership of cybersecurity.
Reporting the flaws exposed how fragmented the supply chain was. Emails and calls bounced between companies, and no dedicated security contact existed. The delay showed how weak coordination can slow down vulnerability response.
They noted five main gaps that explain why such weaknesses appear:
- Procurement documents rarely define cybersecurity requirements.
- Expertise is spread across organizations with different priorities.
- Responsibility for security is unclear.
- Communication channels for disclosures are poor.
- Market pressure to release new connected products often compresses testing timelines.
The study also linked these issues to emerging regulations. The European Union’s Cyber Resilience Act, set to take effect in 2027, will require the types of controls the paper recommends. Until then, the responsibility rests with manufacturers to adopt secure-by-design principles voluntarily.