Russia-linked hackers intensify attacks as global APT activity shifts
State-aligned hacking groups have spent the past six months ramping up espionage, sabotage, and cybercrime campaigns across multiple regions, according to ESET’s APT Activity Report covering April through September 2025. The research highlights how operations linked to Russia, China, Iran, and North Korea have evolved in scope and technique, showing that nation-state activity remains a constant source of disruption.
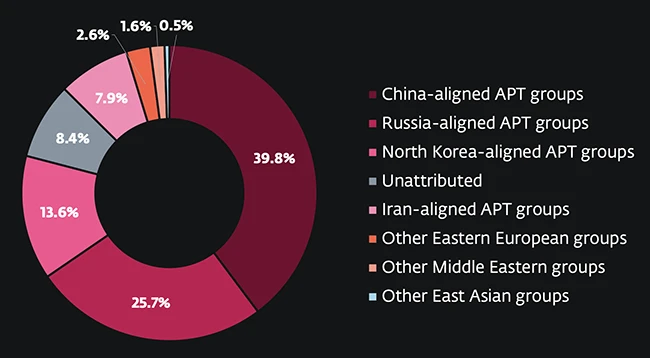
Attack sources (Source: ESET)
Russia’s focus on Ukraine and its allies
Russia-linked actors remained among the most aggressive. Their main focus continued to be Ukraine, along with European Union countries that support Kyiv. Roughly 40 percent of all APT activity tracked during this period came from groups tied to Moscow.
RomCom, one of the most active Russia-aligned groups, exploited a zero-day vulnerability in WinRAR in mid-2025. The flaw, now patched, let attackers execute malicious code simply by convincing victims to open a crafted archive file. ESET says the campaign targeted financial, manufacturing, defense, and logistics firms across Europe and Canada.
Gamaredon also expanded operations in Ukraine with a noticeable rise in both frequency and sophistication. The group experimented with new tools, using cloud storage and tunneling services to move stolen data. In a rare collaboration between Russian cyber units, Gamaredon deployed one of Turla’s backdoors, suggesting selective cooperation on high-value targets.
Meanwhile, Sandworm continued destructive attacks inside Ukraine. Using data-wiping malware such as ZEROLOT and Sting, it struck government, energy, logistics, and grain-sector organizations, likely aiming to weaken Ukraine’s wartime economy. Another actor, InedibleOchotense, impersonated ESET itself in phishing campaigns that delivered a trojanized installer carrying the Kalambur backdoor.
China expands its reach to Latin America
China-aligned groups stayed active across Asia, Europe, and the Americas, accounting for about 26 percent of the observed activity. Their operations reflected Beijing’s strategic goals, with a new emphasis on Latin America.
The group FamousSparrow launched an extensive campaign against government entities in Argentina, Guatemala, Honduras, Panama, and Ecuador. ESET researchers believe this regional focus ties to growing U.S.–China competition, as Washington works to curb Beijing’s financial and political influence near the Panama Canal and elsewhere.
Other China-linked actors relied on more advanced techniques. SinisterEye and PlushDaemon both used adversary-in-the-middle methods to hijack software updates and move laterally inside networks. These tactics gave attackers control over legitimate update processes, allowing them to implant malware without raising alarms.
Jean-Ian Boutin, Director of Threat Research at ESET, told Help Net Security that AiTM has become one of the more effective tools in China-aligned campaigns. “We have identified multiple groups employing adversary-in-the-middle (AiTM) techniques, many of which have been successfully using this method for several years,” Boutin explained. “AiTM is particularly effective when the threat actor can control a device that intercepts network traffic, whether targeting a domestic individual under surveillance or an international visitor of strategic interest.”
Boutin added that China-aligned groups continue to diversify their approaches beyond AiTM. “China-aligned threat actors continue to leverage a diverse set of initial access techniques. These include propagation via removable media, exploitation of public-facing applications—so-called edge devices—and spearphishing campaigns,” he said.
Speccom targeted the energy sector in Central Asia with spearphishing emails sent from compromised government addresses. Analysts suggest these operations may help China gain visibility into its own overseas projects and energy imports. Meanwhile, Silver Fox blurred the line between espionage and profit-seeking by using tax-themed phishing lures to infect organizations in Hong Kong, Malaysia, and India with remote access tools.
Iran adopts internal phishing tactics
Iran-aligned activity remained steady, making up nearly 8 percent of observed campaigns. MuddyWater stood out for an unusual method: internal spearphishing. After compromising a mailbox within a target organization, the group sent phishing messages from that trusted account to coworkers, increasing the odds of success.
This technique allowed attackers to bypass perimeter defenses and trick employees into installing remote management tools or droppers. MuddyWater targeted victims in regions as diverse as Nigeria, Greece, Israel, and the United States. Other Iranian groups, such as GalaxyGato, improved their existing toolsets and used PowerShell-based scripts to collect information and steal credentials during attacks in Greece and Israel.
North Korea mixes espionage with profit
North Korean groups remained active in espionage and financially motivated operations, with roughly 14 percent of global activity attributed to them. Lazarus, Kimsuky, Konni, and DeceptiveDevelopment ran multiple campaigns, often overlapping in tooling and techniques.
DeceptiveDevelopment continued to lure cryptocurrency developers with fake job offers and trojanized codebases, a tactic the group has refined for years. Lazarus maintained a pattern of exploiting supply-chain weaknesses, including compromised software installers from legitimate South Korean vendors.
A new wrinkle appeared when Konni launched attacks against macOS devices in September, using social engineering to steal user credentials and deploy a variant of the EggShell backdoor. ESET also noted North Korean actors extending operations into Uzbekistan, suggesting a widening scope beyond traditional targets.
Other campaigns and emerging tactics
Outside the major powers, ESET tracked smaller groups exploiting the same vulnerabilities. Several actors abused a Roundcube webmail flaw (CVE-2024-42009) to deliver JavaScript downloaders and credential stealers, while an Android spyware operation named Wibag appeared in Iraq. Wibag disguised itself as the YouTube app, collected messages, call logs, and location data, and displayed a login screen branded with the Iraqi National Security Service logo.