cnspec: Open-source, cloud-native security and policy project
cnspec is an open source tool that helps when you are trying to keep a sprawling setup of clouds, containers, APIs and endpoints under control. It checks security and compliance across all of it, which makes it easier to see what needs attention.
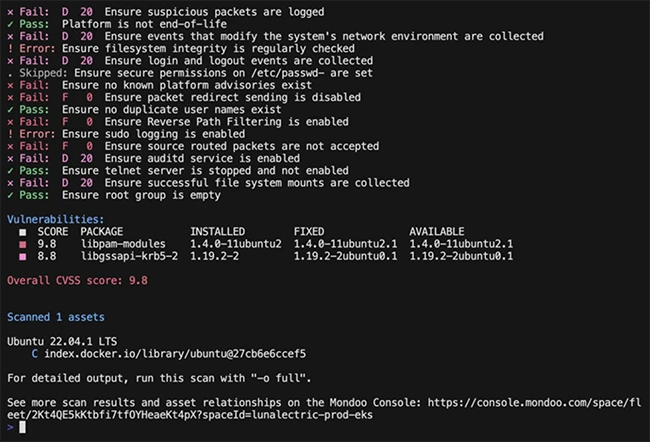
At its core, cnspec looks for vulnerabilities and misconfigurations across public and private cloud environments, Kubernetes clusters, containers, container registries, servers, endpoints, SaaS products, infrastructure as code and APIs. It uses a policy-as-code engine built on a security data fabric, which allows you to codify checks and run them at scale.
What sets cnspec apart is its breadth of targets. Its supported scan targets include everything from cloud accounts such as AWS, Google Cloud and Azure, to Kubernetes clusters and manifests, container images and registries, server endpoints on Linux, macOS and Windows, SaaS platforms like Microsoft 365, Atlassian or Okta, infrastructure-as-code artifacts (Terraform HCL, plan or state files), network hosts or DNS records, version control systems (GitHub, GitLab), IoT or OPC-UA devices, VMware platforms and many others. This means security professionals can apply a consistent set of policies across an environment that spans cloud build pipelines through to runtime operations.
Once you install cnspec you can run scans and policy checks or use the interactive shell for ad-hoc queries. The default policies ship out of the box so you don’t have to start from zero, though you can extend or customize them to suit your environment.
There are real advantages in working with a tool that spans from infrastructure as code through to runtime. You can enforce policy earlier in the pipeline and continuously monitor across the environment. For a CISO or security architect the ability to apply consistent checks across clouds, platforms and services means fewer gaps and better alignment of compliance, security operations and DevSecOps.
Of course a tool like this does not replace all the other pieces of your security stack. Effective use means integrating cnspec into your processes: hooking up to source control, CI/CD, registry scanning, runtime monitoring and asset inventory. You’ll still need alerting, dashboards, context-aware prioritisation of findings and remediation workflows. But by reducing fragmentation in scanning you lighten that burden.
cnspec is available for free on GitHub.

Must read:
- 35 open-source security tools to power your red team, SOC, and cloud security
- GitHub CISO on security strategy and collaborating with the open-source community

Subscribe to the Help Net Security ad-free monthly newsletter to stay informed on the essential open-source cybersecurity tools. Subscribe here!
