Fake “Windows Update” screen fuels new wave of ClickFix attacks
A convincing (but fake) “Windows Update” screen can be the perfect lure for tricking users into infecting their computers with malware.
Add a multi-stage delivery chain with some offbeat techniques, and infostealer operators have everything they need to slip past defenses.
The malware delivery campaigns
“Since the beginning of October, Huntress has identified multiple ClickFix lure sites that trick victims into running a malicious command, following a consistent format and leading to a unique execution chain across multiple incidents,” Huntress reseachers Ben Folland and Anna Pham shared.
Initially, the lure page would show the typical “Human Verification” window, asking users to press Win+R to open the Windows Run box, the CTRL+V to paste a command that was automatically copied to the keyboard, and finally Enter to run the command.
A more recent version of the campaign shows another lure: when potential target land on the page, the browser enters full-screen mode and shows a very convincing Windows Update screen that asks the user to perform the above listed actions “to complete the update”:
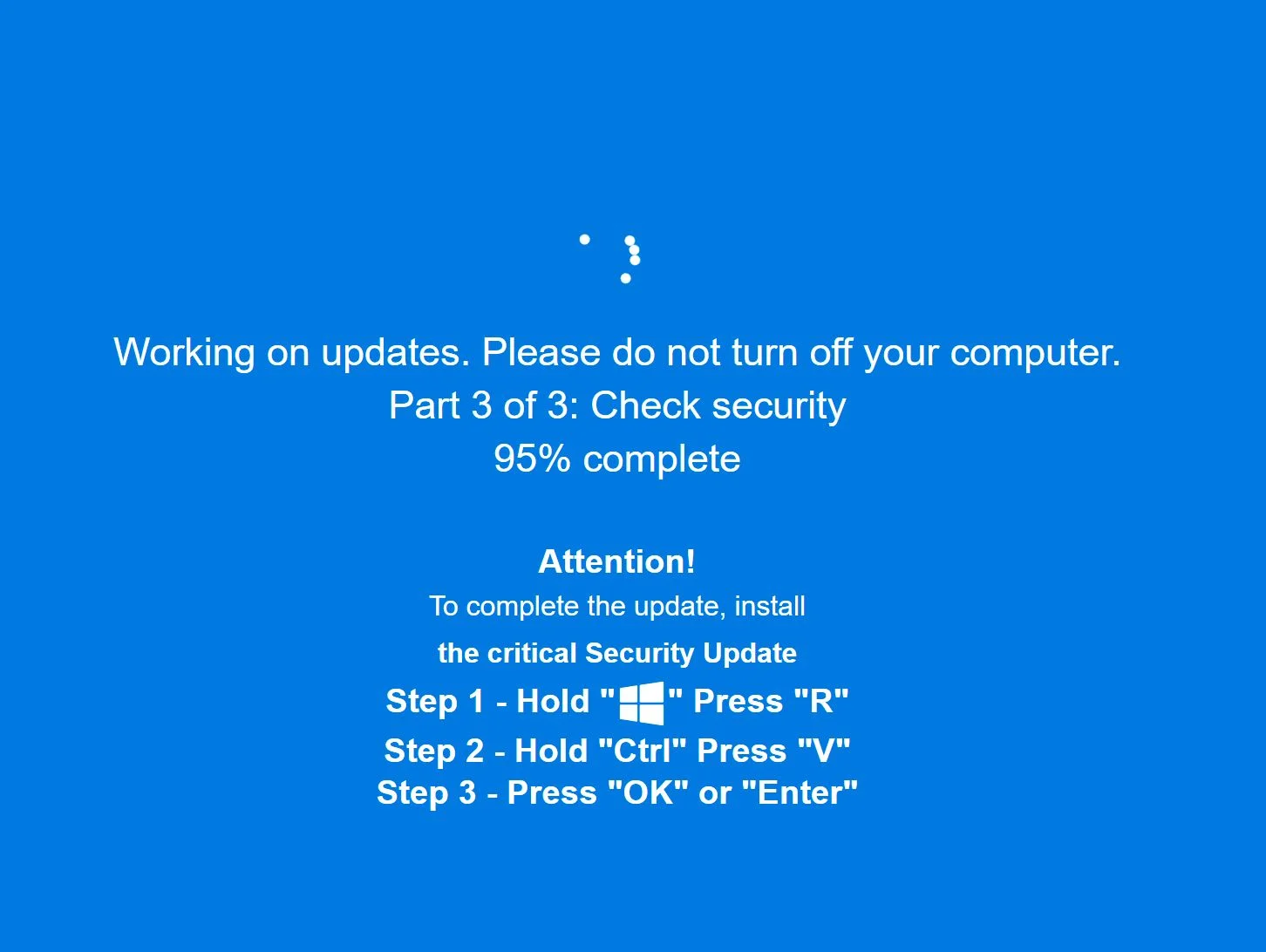
The fake Windows Update screen (Source: Huntress)
If the instructions are followed, the infection chain is triggered, and the user may end up with malware: Lumma or the Rhadamanthys infostealer, respectively.
“Despite the different visual themes, both campaigns begin with an mshta.exe command that contains a URL with an IP address, where the second octet is always hex-encoded. This eventually leads to the deployment of the .NET steganographic loader, which extracts Donut-packed shellcode [encoded] inside the pixel data of PNG images,” the researchers explained.
The whole process and the installation and running of the malware happens in-memory.
To avoid detection by endpoint security solutions, the attackers use obfuscated and dynamically-loaded scripts and code, hidden payloads, and living-off-the-land binaries and legitimate processes.
ClickFix attack prevention
ClickFix is currently one of the most used and most effective tricks used by malware peddlers and initial access brokers. There’s even ClickFix-themed phishing kits aimed at less technically skilled attackers.
The instructions vary depending on whether the targeted users use Windows, macOS or Linux, and the lures themselves are continually being updated and refined.
The researchers advise admins to disable the Windows Run box on regular users’ machines. “Implement the registry modifications above or deploy GPO policies to block interaction with the Windows Run Box,” they counsel.
Users should also be trained to spot the ClickFix methodology and possible variants.
“Use EDR telemetry to monitor for explorer.exe spawning mshta.exe, powershell.exe, or other living-off-the-land binaries with unexpected command lines,” they also advised.
On macOS, users will be instructed to open the system’s Terminal and paste commands into it. Admins can restrict Terminal access for non-admin users and block execution of unsigned scripts via MDM policies.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!
