Manufacturing is becoming a test bed for ransomware shifts
Manufacturing leaders may feel that ransomware risk has settled, but new data shows the threat is shifting in ways that require attention, according to a Sophos report. A global survey of 332 IT and security leaders outlines how attackers are adjusting tactics and how organizations are absorbing the impact of those changes.
The entry point
Exploited vulnerabilities were the most common source of compromise. Malicious email also played a major role, reflecting attackers’ continued use of straightforward techniques that provide access to industrial systems. Although credential based attacks declined, the study indicates that attackers still take advantage of weaknesses that are simple to avoid.
Respondents also tied incidents to internal conditions. They cited a lack of security expertise, unknown gaps in defenses, and limited protective controls. Few identified a single root cause. Most described a mix of shortcomings that created openings for intrusion. The findings show how technical and operational risks can reinforce each other.
Less encryption, rising pressure through data theft
The share of attacks that resulted in data encryption fell to its lowest point in five years. At the same time, respondents reported cases in which attackers stole data and used the threat of disclosure for leverage. Some organizations faced extortion even when no encryption occurred. This pattern reflects the value of intellectual property in manufacturing and the high cost of downtime.
“Manufacturing depends on interconnected systems where even brief downtime can stop production and ripple across supply chains,” said Alexandra Rose, Director of Threat Research, Sophos Counter Threat Unit.
“Attackers exploit this pressure: despite encryption rates falling to 40%, the median ransom paid still reached $1 million. While half of manufacturers stopped attacks before encryption, recovery costs average $1.3 million and leadership stress remains high. Layered defenses, continuous visibility, and well-rehearsed response plans are essential to reduce both operational impact and financial risk,” Rose continued.
Teams were able to stop attacks before encryption in a larger share of cases, which likely contributed to the decline. Early detection helped reduce disruption, although strong detection did not guarantee a smooth recovery.
Respondents often restored systems from backups, while a smaller portion paid the ransom. Payment rates fell from the previous year, which suggests growing confidence in recovery planning and reduced willingness to meet attacker demands.
Demands and payments settle at lower levels as high end cases rise
Typical ransom demands decreased from the previous year, and payments followed the same direction. The middle of the range shrank, while cases at the top end increased. A limited number of victims faced multimillion dollar demands, which renewed concern about the potential for severe financial impact.
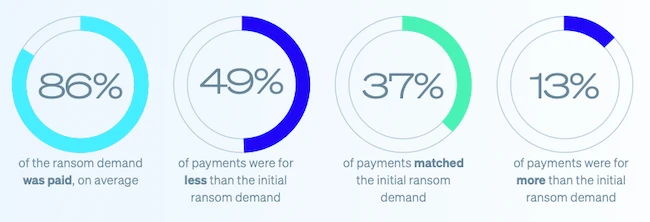
Victims who paid tended to settle at amounts close to the original demand. A smaller share paid less, and a few paid above the initial figure. These differences highlight how negotiations can shift based on operational pressure or the sensitivity of stolen data.
Recovery speeds improve while strain on teams grows
Recovery costs fell from the prior year. Organizations also reported faster restoration of systems and quicker return to steady operations. A significant share recovered within a week, and only a small group needed several months. The findings suggest that teams have strengthened recovery playbooks and adapted them after recent incidents.
Despite these gains, the human impact increased. Every respondent that experienced encryption reported effects on their IT or cybersecurity team. Stress about future attacks was common. Others reported heavier workloads, pressure from senior leaders, or reorganizations following the incident. Some teams experienced leadership turnover, and some staff took time away due to stress or related health issues. The data indicates that teams in manufacturing feel the consequences long after systems return to normal.
Manufacturing environments shape attacker behavior
The study shows how ransomware strategies reflect the realities of industrial operations. Manufacturing depends on systems that cannot withstand extended outages. Production delays affect supply chains. Intellectual property carries significant value. Attackers understand these conditions and adjust their approach accordingly.
Exploited vulnerabilities remain effective because patching industrial equipment can be difficult. Data theft creates leverage because designs and production data are sensitive. Extortion without encryption appeals to attackers because it reduces the risk of interfering with systems in ways that could lower the chance of payment.
Areas for improvement
IT and security leaders in manufacturing see progress in some areas but ongoing gaps in others. Detection appears to be improving. Recovery is becoming steadier. Payment rates are declining. But operational weaknesses persist. Skills shortages, aging protections, and limited visibility into vulnerabilities continue to contribute to compromises. These factors shape outcomes as much as attacker capability.
The findings also show a need for stronger internal support. Security teams are absorbing organizational and emotional strain that can affect long term performance. Manufacturing operations depend on stable systems, and teams cannot maintain stability without workloads they can manage.
A sector in transition
Organizations that invest in basic controls, structured detection, tested backups, and formal incident response plans recover more effectively. Those that rely on informal processes or limited staffing struggle with both technical and human consequences.
Attackers are refining their methods. Teams must adjust theirs as well. The sector is moving forward, but significant work remains to close gaps that continue to place production systems and personnel at risk.