A fake romance turns into an Android spyware infection
ESET researchers have identified an Android spyware campaign that uses romance scam tactics to target individuals in Pakistan. The operation relies on a malicious app disguised as a chat service that routes conversations through WhatsApp. Behind the romance lure, the app’s primary function is to steal data from infected devices. ESET tracks the malware as GhostChat.
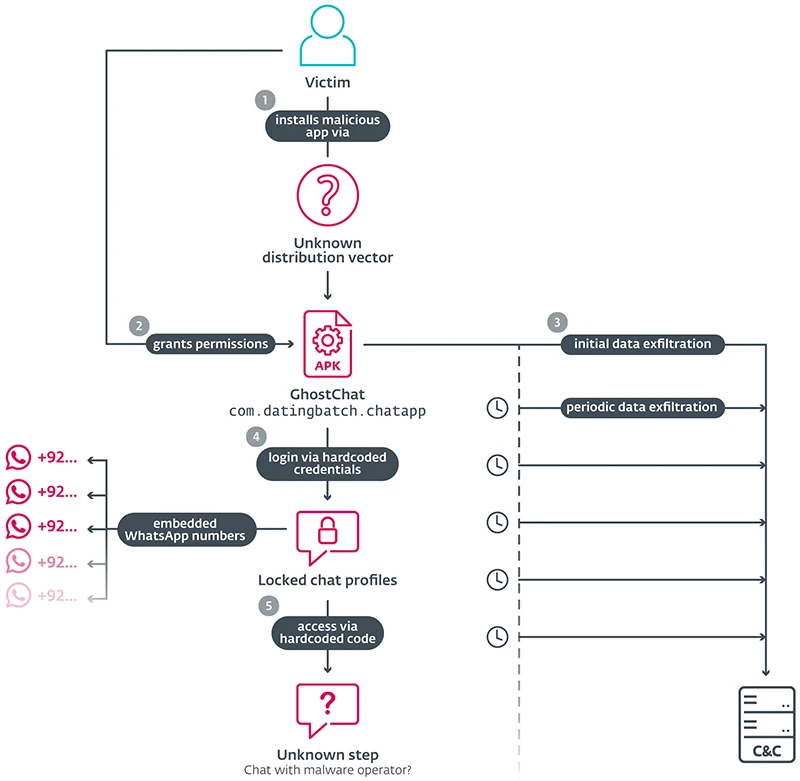
GhostChat attack flow (Source: ESET)
The same threat actor appears to be running a wider surveillance effort. This includes a ClickFix attack that compromises victims’ computers and a WhatsApp device-linking attack that provides access to victims’ WhatsApp accounts.
These related activities relied on websites impersonating Pakistani government organizations as lures. Victims downloaded GhostChat from unofficial sources and installed it manually. The app was never available on Google Play, and Google Play Protect, which is enabled by default, blocks it.
“This campaign employs a method of deception that we have not previously seen in similar schemes – fake female profiles in GhostChat are presented to potential victims as locked, with passcodes required to access them. However, as the codes are hardcoded in the app, this is just a social engineering tactic likely aimed to create the impression of exclusive access for the potential victims,” says ESET researcher Lukáš Štefanko.
The app uses the icon of a legitimate dating service but does not provide the same functionality. Instead, it acts as a lure and a surveillance tool on mobile devices. After logging in, victims see a list of 14 female profiles. Each profile is tied to a specific WhatsApp number with a Pakistani country code. Using local numbers helps make the profiles appear to belong to people based in Pakistan, which adds credibility to the scam. When users enter the required code, the app redirects them to WhatsApp to start a chat with the assigned number, which is likely controlled by the threat actor.
While the victim interacts with the app, and even before login, the GhostChat spyware runs in the background. It monitors device activity and sends sensitive data to a command-and-control server. GhostChat also supports ongoing surveillance. It sets up a content observer to track newly created images and uploads them as they appear. In addition, it runs a scheduled task that checks for new documents every five minutes, allowing continuous data collection.
The campaign is linked to a wider infrastructure that includes ClickFix-based malware delivery and WhatsApp account compromise. These operations rely on fake websites, impersonation of government authorities, and QR code–based device-linking schemes to target both desktop and mobile users. ClickFix is a social engineering technique that convinces victims to manually run malicious code by following instructions that appear legitimate.
Beyond desktop attacks using ClickFix, the same infrastructure supported a mobile-focused operation aimed at WhatsApp users. Victims were encouraged to join a supposed community channel that claimed to be associated with the Pakistan Ministry of Defence. They were prompted to scan a QR code to link their Android device or iPhone to WhatsApp Web or Desktop. This method, known as GhostPairing, gives attackers access to chat history and contacts. It grants the same visibility and control over the account as the legitimate user, exposing private communications.