Notepad++ supply chain attack: Researchers reveal details, IoCs, targets
Rapid7 researchers have attributed the recent hijacking of the Notepad++ update mechanism to Lotus Blossom (aka Billbug), a Chinese state-sponsored group known for targeting organizations in Southeast Asia for espionage purposes.

On Wednesday, Kaspersky researchers shared the insights they’ve gleaned from their own telemetry: the attackers targeted individuals located in Vietnam, El Salvador and Australia; a government organization located in the Philippines; a financial organization located in El Salvador; and a Vietnamese IT service provider.
Attack details
Rapid7’s thorough (and very technical) report describes one of the execution chains identified by Kaspersky: the malicious payload (update.exe) downloaded by the targeted users was a NSIS installer, which sideloaded a DLL (log.dll) that launched the encrypted BluetoothService shellcode into the BluetoothService.exe process.
BluetoothService.exe was found to be a renamed legitimate Bitdefender Submission Wizard, abused for DLL sideloading.
“The shellcode, once decrypted by log.dll, is a custom, feature-rich backdoor we’ve named ‘Chrysalis’. Its wide array of capabilities indicates it is a sophisticated and permanent tool, not a simple throwaway utility,” Rapid7 researchers noted.
“It uses legitimate binaries to sideload a crafted DLL with a generic name, which makes simple filename-based detection unreliable. It relies on custom API hashing in both the loader and the main module, each with its own resolution logic. This is paired with layered obfuscation and a fairly structured approach to C2 communication. Overall, the sample looks like something that has been actively developed over time, and we’ll be keeping an eye on this family and any future variants that show up.”
Kaspersky researchers witnessed another execution chain that also downloaded an NSIS installer, which sent a heartbeat containing system information to the attackers, then dropped a vulnerable version of the legitimate ProShow software.
ProShow was used to launch an exploit payload (also dropped by the installer). The exploit decrypted a Metasploit downloader payload, which retrieved a Cobalt Strike Beacon that established command and control communication.
In yet another, the attackers used a Lua script to launch a Metasploit downloader to download a Cobalt Strike Beacon payload.
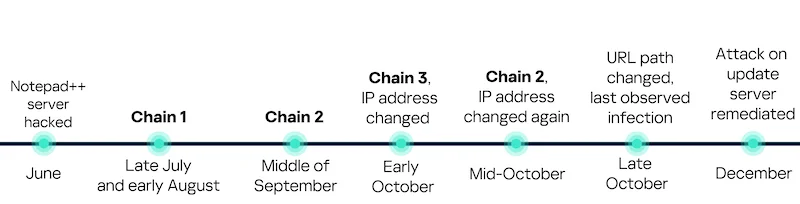
The timeline of the infection chains (Source: Kaspersky)
“We have been amazed to find out how different and unique were the execution chains used in this supply chain attack,” Kaspersky researchers noted.
“We identified that over the course of four months, from July to October 2025, attackers who have compromised Notepad++ have been constantly rotating C2 server addresses used for distributing malicious updates, the downloaders used for implant delivery, as well as the final payloads.”
What to do?
The general consensus is that most Notepad++ users were unaffected by this supply chain attack, as the attackers targeted only a small and highly specific group of targets.
Nevertheless, both Rapid7 and Kaspersky shared indicators of compromise that organizations can use to check whether they’ve been affected.
Orca Security researchers also provided remediation advice and detection guidance.
Notepad++’s maintainer has hardened the software’s custom WinGUP updater to verify both the certificate and the signature of the downloaded installer, as well as to prevent similar hijacks in the future.
He also said that he migrated the Notepad++ website to a new hosting provider “with significantly stronger security practices.”
UPDATE (February 12, 2026, 06:35 a.m. ET):
Palo Alto Networks researchers have identified additional unreported infrastructure linked to this attack campaign and say that the target pool is geographically wider than previously thought.
Previous reports said that the targets were individuals and organizations in the government, finance, telecommunications and critical infrastructure sectors in Southeast Asia and South America, but Palo Alto researchers found that the campaign also affected organizations located in the US and Europe.
Among the targeted organizations were those in the energy, financial, government, and the manufacturing sectors, but also cloud hosting and software development firms.
“In enterprise environments, Notepad++ often serves as a foundational instrument for system administrators, network engineers and DevOps personnel. This specific user demographic makes Notepad++ a strategically critical target for threat actors,” the researchers pointed out.
“Compromising this single tool allows attackers to effectively bypass perimeter defenses and piggyback into the sessions of the most privileged users in the organization, gaining implicit administrative access to the network’s core infrastructure.”

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!
