ScreenConnect admins targeted with spoofed login alerts
ScreenConnect cloud administrators across all region and industries are being targeted with fake email alerts warning about a potentially suspicious login event.
The goal of the attackers is to grab the login credentials and MFA tokens of Super Admins: users who have full control over their organization’s ScreenConnect deployment.
The campaign
ScreenConnect, by US company ConnectWise, is a popular remote support and access solution tailored for IT departments and managed service providers (MSPs).
The platform can be hosted by ConnectWise (in their cloud) or self-hosted by organizations (on-prem or in their own private cloud).
The attack campaign spotted by Mimecast is a low-volume spear-phishing operation. The emails are sent from Amazon Simple Email Service accounts to senior IT professionals with elevated privileges in ScreenConnect environments.
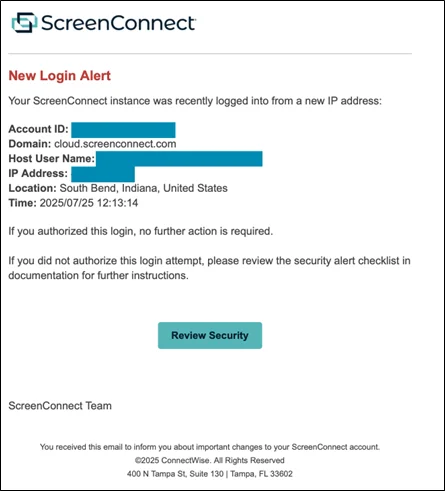
The spoofed ScreenConnect alert (Source: Mimecast)
If the recipient falls for the ruse, they are taken to a legitimate-looking login portal using ConnectWise / ScreenConnect branding.
The attackers are using the open source EvilGinx framework to provision these phishing pages and to act as as a reverse proxy between the victim and the real site (in this case, the organization’s ScreenConnect portal).
The framework can capture both login credentials and session cookies. The latter are necessary if the attackers want to skirt the protection provided by multi-factor authentication (MFA).
Advice for potential targets
“What makes this campaign particularly concerning is its apparent connection to ransomware operations. [Previous] research from Sophos indicates similar ScreenConnect targeting by Qilin ransomware affiliates, suggesting these credential harvesting activities serve as initial access vectors for subsequent ransomware deployment,” Mimecast researchers warn.
“The harvested super admin credentials enable attackers to push malicious ScreenConnect clients or instances to multiple endpoints simultaneously, facilitating rapid lateral movement and ransomware distribution.”
Managed service providers are likely a coveted target, as they offer support to many other businesses. Attackers can use the gained access to “reach” into those organizations and deploy ransomware to many organizations without having to work on compromising each of them separately.
Organizations should conduct targeted training for IT staff on ScreenConnect-themed phishing campaigns, Mimecast advises, and:
- Deploy conditional access policies restricting ScreenConnect admin access to organization-managed devices
- Implement phishing-resistant MFA methods for ScreenConnect accounts
- Enable comprehensive logging for ScreenConnect authentication events and admin activities
- Monitor for unusual admin activities, including new client deployments or configuration changes.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!
