Attackers don’t linger, they strike and move on
Cyber attacks are happening faster than ever. Intrusions that once took weeks or months now unfold in minutes, leaving little time to react. Attackers move quickly once they gain access, aiming to run their payloads and get results before defenders can respond, according to Elastic.
Execution takes the lead
Global telemetry shows that on Windows systems, the “Execution” tactic now accounts for 32% of malicious activity, surpassing “Defense Evasion,” which led for three consecutive years. The shift suggests that many attackers now prioritize payload deployment over stealth. Instead of hiding to extend dwell time, they aim to act quickly, using automation and prebuilt code to achieve their goals before defenders can intervene.
More than 60% of malicious activity observed across major cloud providers, Azure, AWS, and Google Cloud, relates to three objectives: gaining initial access, maintaining persistence, and stealing credentials. These categories dominate across environments and reveal a consistent strategy built around identity compromise. Analysts note that most of these events originate in Microsoft’s ecosystem, reflecting both its popularity and the way attackers exploit familiar authentication flows rather than platform-specific flaws.
AI expands the threat pool
The report notes a rise in “Generic” malware and ties it to attackers using LLMs to build or tweak their tools. The resulting loaders and scripts are often crude, but their sheer volume creates a noise problem for defenders. What was once limited by skill and time can now be automated and customized at scale. This flood of low-complexity threats weakens the value of signature-based detection and favors behavior-driven analytics.
Analysis of more than 150,000 malware samples shows that many are designed to steal browser data. The stolen credentials feed a steady market where access brokers sell ready-made entry points to other attackers. By collecting passwords and cookies from browsers, intruders can slip into corporate cloud accounts with little resistance. The browser has become an entry door rather than a side channel.
The lasting impact of code leaks
The report also shows how source code exposure creates enduring risk. When developers accidentally upload keys, credentials, or sensitive images to public repositories, that data becomes part of an unchangeable history. Even deletions cannot remove copies stored across mirrors and forks. The permanence of such leaks shows how software supply chains now hold some of the most difficult security challenges.
Dominance of Windows
Most attacks still focus on Windows systems. Linux and macOS see far less activity, which matches their smaller footprint across businesses. Trojans remain the most common type of malware, followed by generic threats, rootkits, and cryptominers. The pattern shows that attackers keep going after familiar platforms and proven techniques instead of chasing rare or experimental exploits.
Most malicious files over the past year arrived as executables or installation packages, often disguised as routine software updates or compressed attachments. Script-based files such as JavaScript and Visual Basic continue to circulate because they blend easily with legitimate workflows. The persistence of these simple file types shows how attackers keep using what users already trust rather than inventing new delivery methods.
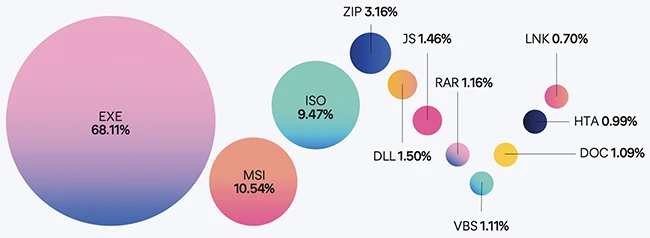
Top file types for malware (Source: Elastic)
Identity at the center
Identity stands out as the common thread across nearly every layer of attack. In Azure environments, unusual activity often begins in authentication logs, revealing how frequently attackers rely on stolen or misused accounts to get inside. In Microsoft 365, compromised email accounts often serve as the next step, giving intruders access to messages, shared files, and other connected services. Once they have valid credentials, they move through cloud systems using legitimate tools and permissions, making their actions hard to distinguish from normal user behavior.
“Attackers are shifting from stealth to speed, launching waves of opportunistic attacks with minimal effort,” said Devon Kerr, head of Elastic Security Labs and director of Threat Research. “This evolution shows how urgent it is for defenders to harden identity protections and to adapt their detection strategies for this new era of speed attacks.”