Wi-Fi signals may hold the key to touchless access control
Imagine walking into a secure building where the door unlocks the moment your hand hovers near it. No keycards, no PINs, no fingerprints. Instead, the system identifies you by the way your palm distorts the surrounding Wi-Fi signal. That is the idea behind a new study from researchers at the Aeronautics Institute of Technology (ITA) in Brazil.
Turning Wi-Fi signals into identity data
The study explores how Wi-Fi Channel State Information, or CSI, can capture the tiny physical differences that make each person’s hand unique. CSI is data that shows how a wireless signal behaves as it moves through the air, bouncing off objects and people. Those variations can be recorded and analyzed to find repeatable patterns linked to a specific person.
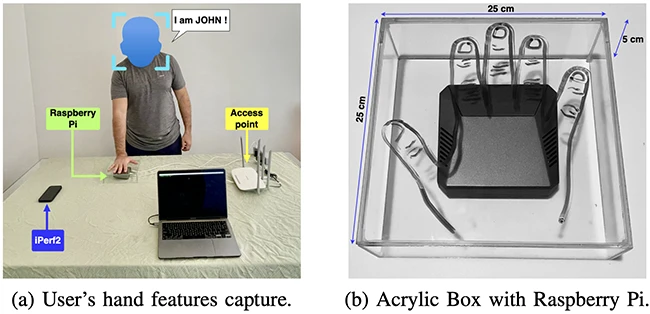
In this research, the team focused on the shape and structure of the palm. They looked at hand size, finger length, and how far apart the fingers are. These details slightly change the Wi-Fi signal when the hand is near the transmitter and receiver. The researchers built a small test setup using a Raspberry Pi computer placed in a custom acrylic box. The device’s antenna power was reduced to 1 dBm to limit outside interference and capture small signal differences.
Each participant placed a hand over the box while Wi-Fi signals were sent and received. The system recorded the resulting CSI data and used machine learning algorithms to decide whose hand it was.
How the experiments worked
The researchers tested their idea with 20 volunteers, half men and half women. Each person placed their right hand above a small acrylic box that held a Raspberry Pi device. The box sent and received Wi-Fi signals while the system watched how the person’s hand affected them.
Each hand was scanned a few times for several seconds. This created thousands of data points for the team to study. The signals showed changes in strength and timing, both of which helped reveal the unique shape and size of each person’s hand.
Once the data was collected, the researchers used machine learning to teach the system how to tell one person’s palm from another. They tried several common algorithms before finding one that worked best.
Experiments (Source: Research paper)
Why consistency might be a bigger challenge
While the study reached high accuracy in a controlled environment, maintaining that performance in real-world settings could be more complicated. Christina Hulka, Executive Director of the Secure Technology Alliance, told Help Net Security that CSI data is sensitive to small environmental changes that can disrupt the signal.
“CSI features are tightly linked to multipath reflections off walls, floors, glass and metal. Thick concrete and metal objects can interfere with signal strength and block signals,” she explains. “Something as simple as shifting a rolling cart or adding a privacy screen can change the channel enough to move the model off its ‘sweet spot.’ Human bodies are also excellent RF absorbers and reflectors. People moving around or in crowded areas can block the signal or cause false rejections.”
She adds that many environments already contain overlapping wireless activity that can make stable authentication difficult. “We’re also living in a world where ‘RF-business’ is a real challenge,” Hulka says. “Cellphone Bluetooth connections, Wi-Fi networks, Zigbee traffic and most connected devices can introduce artifacts into CSI streams which will impact its stability and classifier confidence. There isn’t really a foolproof workaround for this problem at the moment.”
The problem, she notes, extends to differences in hardware. “Even minute differences in commodity radios or cable strain can shift phase or amplitude in ways the model interprets as identity drift,” she says. “Suffice to say, there’s a lot to consider here.”
Building a non-contact access system
The goal of the research was to create an access control method that is contactless, easy to use, and low cost. Using Wi-Fi for this purpose means that the same infrastructure already found in most buildings could be adapted for authentication. The Raspberry Pi setup used in the study cost far less than traditional biometric hardware and required little power to operate.
To keep the data consistent, users removed jewelry, watches, and other items that could distort the signal. The acrylic box also helped by minimizing interference and maintaining a steady 3-centimeter distance between the hand and the receiver. Each capture included a short delay before recording began to ensure stable readings.
The experiment used only the right-hand data for analysis, though the full dataset includes both hands. The researchers plan to expand future tests to larger groups, longer time periods, and different physical conditions.
Testing under real pressure
Hulka cautions that before this kind of Wi-Fi authentication can be trusted, it needs to be tested under stricter and more transparent conditions.
“‘Near-perfect’ results don’t mean much outside of a lab without being validated through a formal biometric certification or validation program,” she says. “You should report ISO/IEC 19795-1 metrics under cross-day and cross-site conditions rather than a single controlled setting. So, test different rooms, outdoor environments and hardware.”
She also emphasizes the need for standards-based evaluation. “Ask an independent lab to run a presentation-attack detection evaluation aligned to ISO/IEC 30107-3 that includes both targeted checks of the PAD component and full end-to-end system trials,” Hulka explains. “The lab should use realistic instruments and publish the key error rates right alongside the core accuracy numbers. Pair this with the standard performance metrics so practitioners can judge both usability and resilience in one view.”
What this could mean for CISOs
The authors see potential for Wi-Fi-based biometrics in settings where traditional sensors are hard to maintain or could raise privacy concerns. Since the system uses existing wireless hardware, it could fit into IoT environments or physical access systems that already rely on Wi-Fi networks.
For security leaders, this kind of research hints at a different layer of identity management that blends physical and network signals. It may not replace fingerprints or badges anytime soon, but it shows how authentication could evolve using the wireless systems already in place.

eBook: Defending Identity Security the Moment It’s Threatened