The 2026 State of Pentesting: Why delivery and follow-through matter more than ever
Penetration testing has evolved significantly over the past several years. While uncovering exploitable vulnerabilities remains the core goal, the real differentiator today is how findings are handled after the testing concludes. The method of reporting, delivery, and remediation tracking play a critical role in determining how effective a pentest is at actually reducing risk.
Security leaders increasingly expect penetration testing to integrate seamlessly into their broader security operations. Static reports no longer meet the needs of organizations managing complex, fast-changing environments. Results must be timely, actionable, and directly connected to remediation and validation processes. This shift has exposed operational gaps in many pentest programs and resulted in bottlenecks as more organizations shift towards continuous testing.
Why legacy pentest reporting no longer scales
Traditional pentest delivery models rely heavily on static documents that exist outside day-to-day security workflows, which means the data becomes siloed from other security data. Findings are often disconnected from vulnerability scanners, ticketing platforms, and remediation tools, creating fragmented processes and inconsistent handling across teams.
These silos introduce several challenges, including inconsistent formatting, unclear ownership once reports are delivered, and limited visibility tracking into whether fixes are validated or ready to retest. With expanding attack surfaces that continue to grow each year, these manual handoffs become a significant bottleneck.
The problem scales as teams move toward more frequent or continuous testing. Without scalable delivery and validation workflows, the operational burden increases and the value of testing declines due to operational scalability issues.
Continuous pentesting requires continuous delivery operations
To keep pace with modern environments, many organizations have transitioned from point-in-time testing to continuous pentesting models. In this approach, findings are treated as ongoing operational inputs rather than isolated snapshots captured in a report.
This change is not simply about increasing testing frequency. It requires consistent findings, faster turnaround, and tight integration with remediation and validation workflows. Without these elements, continuous testing quickly becomes unmanageable.
What mature pentest programs look like in 2026
Organizations with advanced pentest programs tend to share common operational traits:
- Centralized visibility across pentest and scanner findings: Ensures findings are managed consistently, regardless of origination
- Standardized, reusable findings for consistency: Reduces duplication, improves quality, and speeds up reporting
- Real-time collaboration across operators and reviewers: Eliminates handoffs and rework by enabling faster feedback and alignment
- Continuous testing rather than point-in-time engagements: Keeps risk visibility current as environments and attack surfaces change
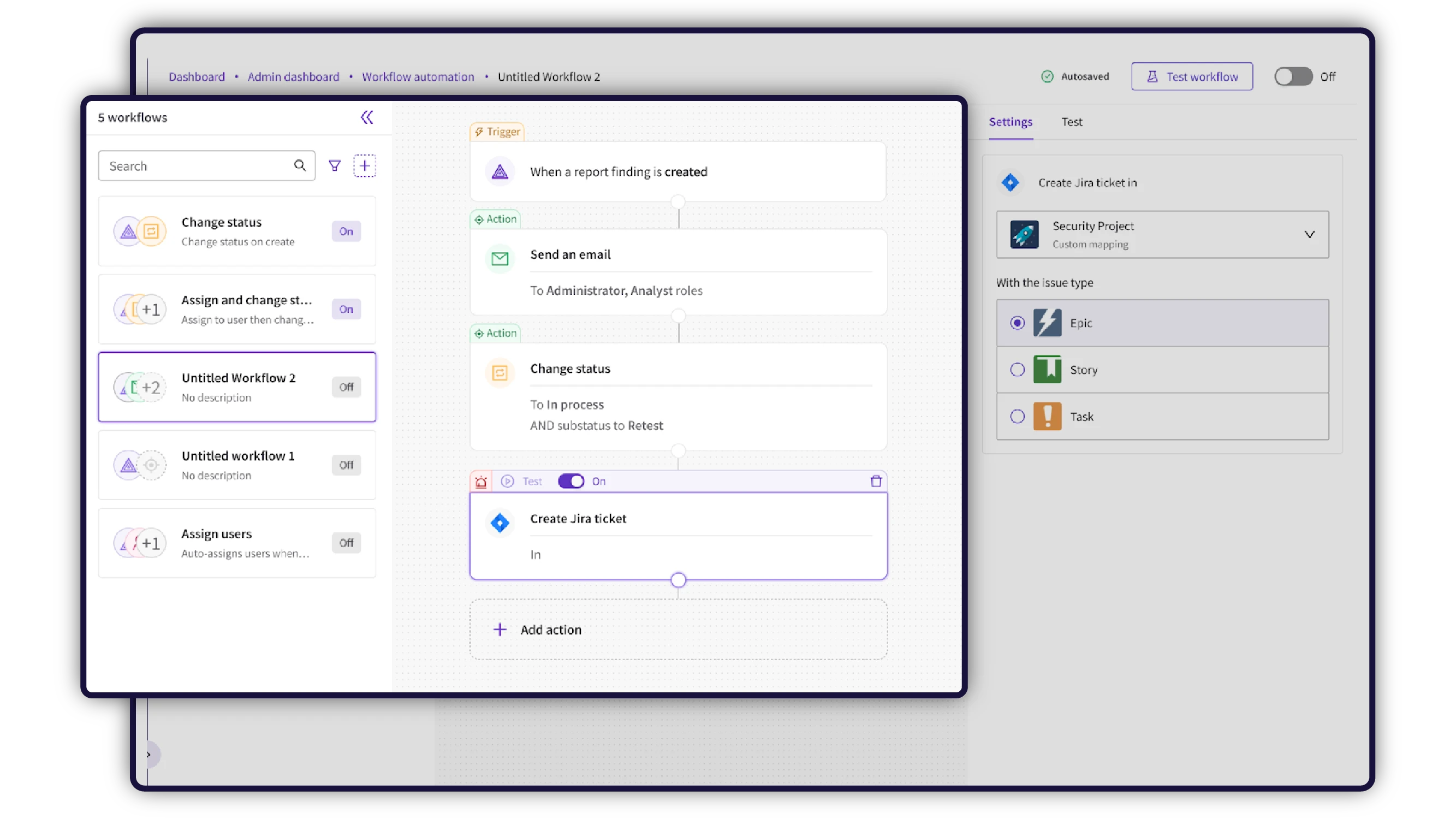
- Automated delivery of findings into remediation tools: Accelerates remediation by auto-routing findings directly into established workflows
- Clear ownership and prioritization: Prevents findings from stalling by establishing accountability and risk-based focus
- Automated retesting and validation workflows to close the loop: End-to-end tracking helps confirm fixes and provide measurable risk reduction
In these programs, reporting is no longer a final deliverable. It is a living process that supports continuous exposure management.
Closing the gap between offensive security and vulnerability management
A longstanding challenge in many organizations is the separation between red teams and vulnerability management functions. When findings are passed via PDFs or manually created tickets, critical context is often lost and collaboration breaks down.
Modern programs prioritize shared systems and integrated workflows. Offensive teams can deliver validated findings directly into remediation platforms, while vulnerability teams track progress, verify fixes, and measure outcomes without leaving their primary tools.
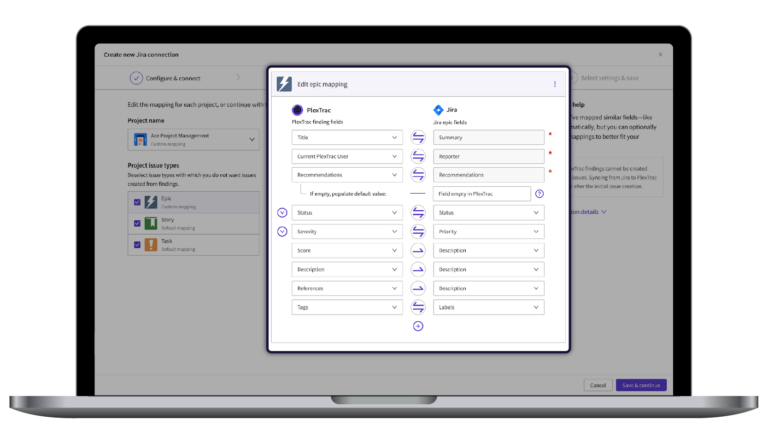
This need has driven the rise of Exposure Assessment Platforms (EAPs), such as PlexTrac. EAPs support the Continuous Threat Exposure Management (CTEM) lifecycle by aggregating findings from multiple sources, prioritizing them based on real risk, and enabling efficient and automated remediation and validation workflows. Their focus is on reducing noise and helping teams address the issues most likely to lead to a breach.
Technology that supports modern pentest delivery
The shift toward continuous, outcome-driven pentesting is enabled by platforms designed to connect, not replace, existing tools. Rather than forcing teams into isolated dashboards, modern solutions emphasize interoperability.
By integrating with systems like Jira, ServiceNow, Azure DevOps, security scanners, and other essential tools, these platforms allow findings to move from discovery to remediation and validation in one unified workflow, regardless of where the finding was sourced. Tools like PlexTrac are increasingly used to centralize security data while keeping workflows automated and aligned with how teams already operate.
What this means for pentesting teams moving forward
Mature pentesting operations are defined not only by the quality of testing, but by the delivery method and follow-through execution. Teams that modernize how results are delivered and operationalized will reduce friction, improve collaboration, and demonstrate measurable impact on organizational risk.
In 2026 and beyond, the effectiveness of a pentest program will be judged not only by the vulnerabilities it uncovers, but by how efficiently those findings lead to remediation and verified risk reduction.
How PlexTrac supports modern pentest programs
PlexTrac is the leading AI-powered platform for pentest reporting and threat exposure management, trusted by Fortune 500 companies and top security providers including Expedia, Mandiant, Deloitte, and KPMG. PlexTrac streamlines and automates each stage of the reporting workflow, enabling you to deliver more impactful results in less time.
Built to help cybersecurity teams continuously manage and reduce threat exposure, PlexTrac centralizes security data, streamlines reporting, prioritizes risk, and automates remediation workflows, empowering teams to drive measurable risk reduction.
You can explore these and other features by requesting a demo on the PlexTrac website.