WinRAR vulnerability still a go-to tool for hackers, Mandiant warns
State-sponsored hackers and financially motivated attackers continue leveraging a critical WinRAR vulnerability (CVE-2025-8088) that’s been fixed over half a year ago.
CVE-2025-8088 is a path traversal vulnerability that can be exploited via maliciously crafted RAR archives.
“The exploit chain often involves concealing the malicious file within the ADS of a decoy file inside the archive. While the user typically views a decoy document (such as a PDF) within the archive, there are also malicious ADS entries, some containing a hidden payload while others are dummy data,” the Mandiant researchers explained.
“When the archive is opened, the ADS content (malicious.lnk) is extracted to the destination specified by the traversal path, automatically executing the payload the next time the user logs in.”
Exploit supplier fuels WinRAR attacks
In July and August 2025, researchers spotted CVE‑2025‑8088 being leveraged by the RomCom (aka Storm-0978) hackers and the Paper Werewolf (aka Goffee) attack group.
BI.ZONE researchers posited that both groups got their exploit from the same vendor: “zeroplayer”, an exploit supplier that advertizes on dark web forums.
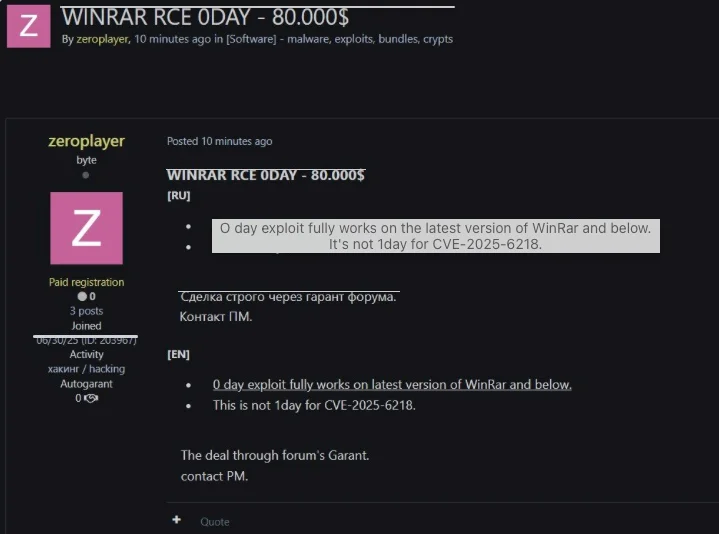
WinRAR zero-day exploit for sale (Source: BI.ZONE)
Since those earliest attacks, other threat actors have been spotted exploiting (or attempting to exploit) CVE-2025-8088:
- Several Russian-nexus APTs, for cyber espionage purposes against Ukrainian targets: Sandworm (aka APT44), Trula (aka Secret Blizzard), and TEMP.Armageddon (aka CARPATHIAN)
- An unspecified China-Nexus threat actor to deliver the POISONIVY (aka Darkmoon) remote access trojan
- Financially motivated groups that targeted entities in Indonesia, organizations in the hospitality and travel sectors in Latin America, and users of banking websites of two Brazilian banks
The malware delivered via these booby-trapped archive files varies from malicious Chrome extensions to backdoors and commodity RATs and information-stealing malware, but the attacks continue to this day.
“By providing ready-to-use capabilities, actors such as zeroplayer reduce the technical complexity and resource demands for threat actors, allowing groups with diverse motivations—from ransomware deployment to state-sponsored intelligence gathering—to leverage a diverse set of capabilities,” Mandiant researchers noted.
Users of the popular archiving utility – and there are several hundred millions of them out there – should download and install WinRAR 7.13, which contains fixes for both CVE‑2025‑8088 and another known exploited flaw (CVE‐2025‐6218).
(WinRAR doesn’t have an automatic update feature. A new version must be downloaded and installed over the existing installation.)

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!
