Criminals create business website to sell RAT disguised as RMM tool
A RAT masquerading as legitimate remote monitoring and management (RMM) software is being sold to cybercriminals as a service, Proofpoint researchers recently discovered.
The fake RMM tool, called TrustConnect, was being marketed via an LLM-created website parked on trustconnectsoftware[.]com, supposedly belonging to “TrustConnect Software PTY LTD”.
“The malware creator uses the domain as the ‘business website’ designed to convince the public (including certificate providers) that the software is a legitimate RMM app, providing fake details like customer statistics and software documentation,” the researchers explained.
“This website is also the portal for criminals to sign up for the service and acts as the command and control (C2) for the malware. Cybercriminals are instructed to sign up for a ‘free trial’, instructed on how to pay in cryptocurrency, and then verify payment in the TrustConnect portal.”
Owning the domain also allowed the threat actor to purchase a legitimate Extended Validation (EV) certificate, which they then used to sign the RAT/fake RMM tool, thus helping it evade signature-based detections.
The operation and delivery campaigns
The threat actor sold access to the tool and C2 portal for $300 per month.
The TrustConnect command and control panel (Source: Proofpoint)
The buyers distributed TrustConnect Agent (and also legitimate RMMs) via email campaigns using various lures: tax-related emails, DocuSign notifications, meeting invitations, events, and more.
TrustConnect creates fake installers that look like real software by using familiar icons, names, and branding while secretly delivering malware. The attackers use common lures seen in cybercrime campaigns, including well-known corporate apps like Zoom, Microsoft Teams, Adobe Reader, and Google Meet, as well as document-style files labeled things like “Proposal,” “Special Events,” or “Social Security Administrative.”
It also offers a generic installer branded simply as “TrustConnect,” likely meant to appear as a legitimate IT management tool.
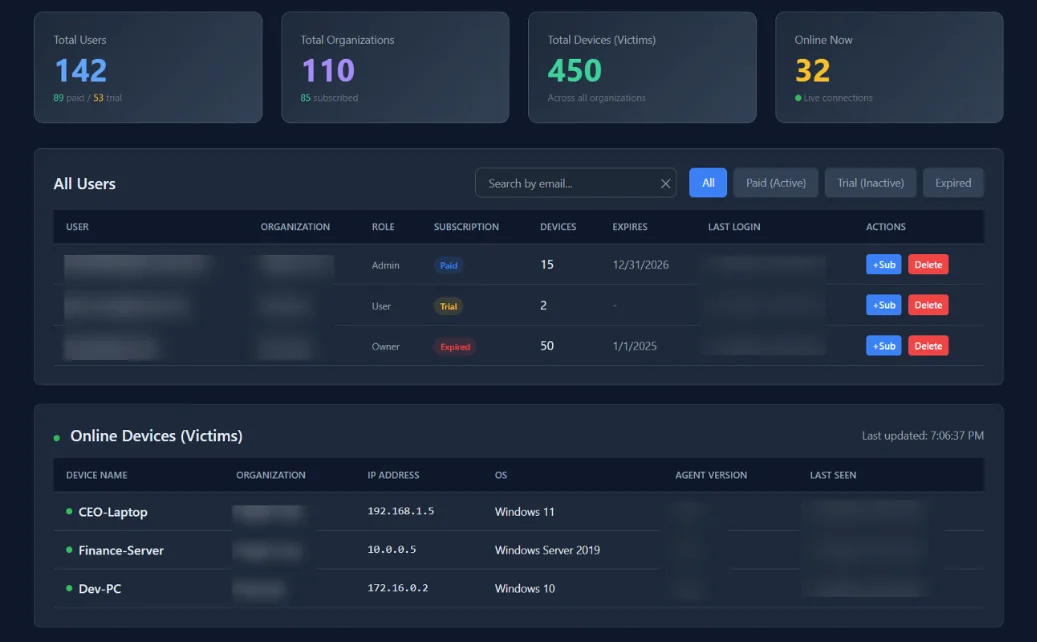
Admin dashboard, with mock data (Source: Proofpoint)
“Proofpoint has observed TrustConnect campaigns leading to the follow-on deployment of a legitimate remote access tool, typically ScreenConnect (…) from at least nine distinct on‑premises (self‑hosted) ScreenConnect servers over a 10‑day period,” the researchers shared.
“All were older versions signed with expired or revoked certificates, suggesting the instances were illegitimately purchased previously or possibly pirated. Proofpoint also observed deployment of Level RMM via an abused account as well as hands‑on-keyboard activity. This activity occurred within minutes of TrustConnect installation, reinforcing the assessment that it is used by multiple threat actors. (We reported it to Level, and the account was disabled by the vendor.)”
Attempted disruption
Proofpoint worked with industry partners to disrupt the TrustConnect operation.
They collaborated with certificate-intelligence specialists to revoke the malware’s Extended Validation code-signing certificate on Feb. 6, 2026, stripping the operators of the ability to make malicious files appear trusted and evade detection. 
However, the certificate revocation was not applied retroactively, which means files signed before the revocation remained valid and could still be distributed by existing criminal customers. 
The company also coordinated action against the malware’s command-and-control environment, which was hosted on a specific server and was taken offline around Feb. 17, an operation that impacted the actor’s infrastructure and disrupted ongoing campaigns.
Unfortunately, the disruption proved temporary: shortly before the report’s publication, the operators had already shifted to parallel infrastructure and begun testing a rebranded, updated version of the malware platform called DocConnect.
“Based on details of the malware creator, capabilities of the malware, and knowledge of the ecosystem, we assess with moderate confidence the threat actor behind TrustConnect was also a prominent user of Redline stealer,” the researchers stated.
They also believe that the TrustConnect and DocConnect websites and agents were likely coded with the assistance of AI agents.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!