Anamarija Pogorelec

Open-source malware zeroes in on developer environments
Open source malware activity during 2025 concentrated on a single objective: executing code inside developer environments, according to Sonatype. The focus reflected a broader …

Hottest cybersecurity open-source tools of the month: January 2026
This month’s roundup features exceptional open-source cybersecurity tools that are gaining attention for strengthening security across various environments. OpenAEV: …

What motivates hackers and what makes them walk away
Most hackers spend more time learning, testing, and comparing notes than breaking into systems. The work often happens alone or in small groups, shaped by curiosity, …

A fake romance turns into an Android spyware infection
ESET researchers have identified an Android spyware campaign that uses romance scam tactics to target individuals in Pakistan. The operation relies on a malicious app …

OPNsense 26.1 brings updates to open-source firewall management
OPNsense, the open-source firewall and network security platform, reached version 26.1, adding a range of updates affecting management, traffic visibility, automation …
n8n adds Chat Hub to centralize AI access inside automation workflows
Teams using automation platforms are starting to treat conversational AI as another operational interface. That change is reflected in a new feature from n8n, which has …
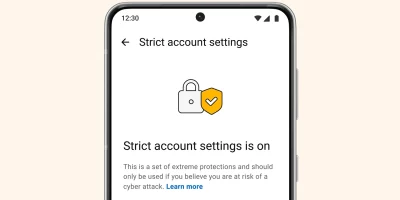
WhatsApp rolls out new security feature to protect users from sophisticated attacks
To add an extra layer of protection to its end-to-end encryption, WhatsApp has begun rolling out a new privacy and security feature called Strict Account Settings. It is …

Grammarly and QuillBot are among widely used Chrome extensions facing serious privacy questions
A new study shows that some of the most widely used AI-powered browser extensions are a privacy risk. They collect lots of data and require a high level of browser access. The …

Audits for AI systems that keep changing
Security and risk teams often rely on documentation and audit artifacts that reflect how an AI system worked months ago. ETSI’s continuous auditing based conformity assessment …

AWS adds IPv6 support to IAM Identity Center through dual-stack endpoints
Amazon Web Services has added IPv6 support to IAM Identity Center through new dual-stack endpoints. The update allows identity services to operate over IPv6 networks while …

AI’s appetite for data is testing enterprise guardrails
Privacy programs are taking on more operational responsibility across the enterprise. A new Cisco global benchmark study shows expanding mandates, rising investment, and …

Cybersecurity jobs available right now: January 27, 2026
CISO micro1 | USA | Remote – No longer accepting applications As a CISO, you will define the enterprise security vision and implement a zero-trust architecture across …