Zeljka Zorz

Attackers compromised ALL SonicWall firewall configuration backup files
The attackers who brute-forced their way into SonicWall’s firewall cloud backup service accessed configuration backup files of all customers who have used the service, …

Researchers uncover ClickFix-themed phishing kit
Palo Alto Networks researchers have discovered and analyzed “IUAM ClickFix Generator”, a phishing kit that allows less skilled attackers to infect unsuspecting …

North Korean hackers stole over $2 billion in cryptocurrency this year
North Korean hackers have stolen more than $2 billion in cryptocurrency in 2025, according to blockchain analytics firm Elliptic, and the year isn’t over yet. Though …

Redis patches critical “RediShell” RCE vulnerability, update ASAP! (CVE-2025-49844)
Redis, the company behind the widely used in-memory data structure store of the same name, has released patches for a critical vulnerability (CVE-2025-49844) that may allow …

Leaked Oracle EBS exploit scripts expected to drive new wave of attacks (CVE-2025-61882)
Resecurity and watchTowr researchers have analyzed the leaked scripts used by attackers to exploit CVE-2025-61882 on internet-facing Oracle ESB instances. Whether the …

Hackers launch data leak site to extort 39 victims, or Salesforce
Scattered Lapsus$ Hunters launched a data leak site over the weekend, aiming to pressure organizations whose Salesforce databases they have plundered into paying to prevent …

Cl0p exploits Oracle E-Business Suite zero-day in data theft, extortion campaign (CVE-2025-61882)
The Cl0p extortion gang exploited multiple Oracle E-Business Suite (EBS) vulnerabilities, including one zero-day flaw (CVE-2025-61882), “to steal large amounts of data …

Hackers claim to have plundered Red Hat’s GitLab repos
The Crimson Collective, an emerging extortion / hacker group, has made a bombshell claim on their Telegram channel: they have gained access to Red Hat’s GitLab and have …

Oracle customers targeted with emails claiming E-Business Suite breach, data theft
Unknown attackers claiming affiliation with the Cl0p extortion gang are hitting business and IT executives at various companies with emails claiming that they have exfiltrated …

North Korea’s IT workers are targeting firms beyond tech, crypto, and the U.S.
North Korea’s clandestine IT Worker (ITW) program, which is long known for targeting U.S. technology firms and crypto firms, has broadened its scope to attempt to infiltrate a …
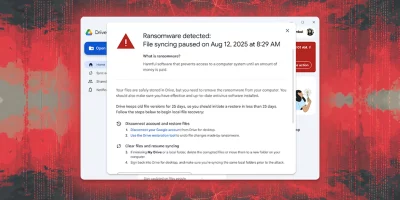
Google Drive for desktop will spot, stop and remedy ransomware damage
Google has rolled out AI-powered ransomware detection and file restoration features in Drive for desktop, Google’s official file syncing and access app for Windows and …

Too many Cisco ASA firewalls still unsecure despite zero-day attack alerts
Despite Cisco and various cybersecurity agencies warning about attackers actively exploting zero-day vulnerabilities (CVE-2025-20333 and CVE-2025-20362) in Cisco Adaptive …