
Motorola turns to GrapheneOS for smartphone security upgrade
Motorola is strengthening smartphone security through a long-term partnership with the GrapheneOS Foundation, a mobile security nonprofit that develops a hardened operating …

Android 17 second beta expands privacy controls for contacts, SMS and local networks
Google’s second beta of Android 17 continues updates to platform behavior and introduces new APIs focused on protecting sensitive data. Protecting contact and local network …

Android app uses Bluetooth signals to detect nearby smart glasses
Smart glasses with built-in cameras are showing up in more public spaces, and a growing number of people want a way to know when one is nearby. An Android app called Nearby …

WhatsApp is adding another lock to your account
Meta has released WhatsApp Beta for Android 2.26.7.8 through the Google Play Beta Program. The update includes references to password-protected accounts, indicating plans to …

Google cleans house, bans 80,000 developer accounts from the Play Store
Google prevented more than 1.75 million policy-violating apps from being published on Google Play and banned over 80,000 developer accounts that attempted to publish harmful …

PromptSpy: First Android malware to use generative AI in its execution flow
ESET researchers have discovered PromptSpy, the first known Android malware to abuse generative AI as part of its execution flow in order to achieve persistence. This marks …

Firmware-level Android backdoor found on tablets from multiple manufacturers
A new Android backdoor embedded directly in device firmware can quietly take control of apps and harvest data, Kaspersky researchers found. The malware, named Keenadu, was …

Android 17 beta brings privacy, security, and performance changes
Google has released the first beta of Android 17, giving developers an early view of changes to core app behavior, platform tooling, performance, media handling, and …

Mobile privacy audits are getting harder
Mobile apps routinely collect and transmit personal data in ways that are difficult for users, developers, and regulators to verify. Permissions can reveal what an app can …

Google disrupts proxy network used by 550+ threat groups
Google has disrupted Ipidea, a massive residential proxy network consisting of user devices that are being used as the last-mile link in cyberattack chains. “In a single …

Google agrees to pay $135 million over Android data harvesting claims
Google agrees to pay $135 million to settle a proposed class action lawsuit brought by Android smartphone users over alleged unauthorized cellular data transmissions. After …
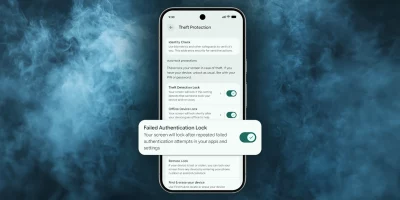
Android just got smarter at stopping snatch-and-run phone thefts
Google announced updates to the Android theft protection features that expand existing safeguards and make stolen devices harder to use. These updates are available on Android …
Featured news
Resources
Don't miss
- Your dependencies are 278 days out of date and your pipelines aren’t protected
- Security debt is becoming a governance issue for CISOs
- BlacksmithAI: Open-source AI-powered penetration testing framework
- When cyber threats start thinking for themselves
- IronCurtain: An open-source, safeguard layer for autonomous AI assistants