
Linux users targeted by crypto thieves via hijacked apps on Snap Store
Cryptocurrency thieves have found a new way to turn trusted software packages for Linux on the Snap Store into crypto-stealing malware, Ubuntu contributor and former Canonical …
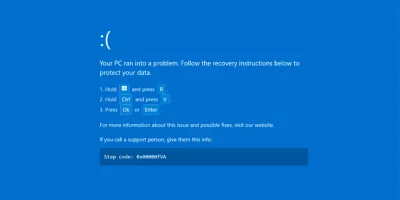
Fake Booking.com emails and BSODs used to infect hospitality staff
Suspected Russian attackers are targeting the hospitality sector with fake Booking.com emails and a fake “Blue Screen of Death” to deliver the DCRat malware. The …

Budding infosec pros and aspiring cyber crooks targeted with fake PoC exploits
Malware peddlers are targeting infosec enthusiasts, budding security professionals, and aspiring hackers with the Webrat malware, masquerading the threat as proof-of-concept …

Group Policy abuse reveals China-aligned espionage group targeting governments
ESET Research has identified a previously undocumented China-aligned advanced persistent threat group that uses Windows Group Policy to deploy malware and move through victim …

MuddyWater cyber campaign adds new backdoors in latest wave of attacks
ESET researchers say an Iran aligned threat group is refining its playbook again, and the latest activity shows how much its tactics have shifted. MuddyWater is a long running …
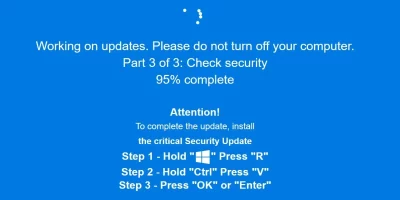
Fake “Windows Update” screen fuels new wave of ClickFix attacks
A convincing (but fake) “Windows Update” screen can be the perfect lure for tricking users into infecting their computers with malware. Add a multi-stage delivery …

MacOS DigitStealer malware poses as DynamicLake, targets Apple Silicon M2/M3 devices
A new infostealer is targeting macOS users by masquerading as the legitimate DynamicLake UI enhancement and productivity utility and possibly Google’s Drive for desktop app. …

Rhadamanthys infostealer operation disrupted by law enforcement
The rumors were true: Operation Endgame, a joint effort between law enforcement and judicial authorities of several European countries, Australia, Canada, the UK and the US, …

Attackers upgrade ClickFix with tricks used by online stores
Attackers have taken the ClickFix technique further, with pages borrowing tricks from online sellers to pressure victims into performing the steps that will lead to a malware …

Google uncovers malware using LLMs to operate and evade detection
PromptLock, the AI-powered proof-of-concept ransomware developed by researchers at NYU Tandon and initially mistaken for an active threat by ESET, is no longer an isolated …

Attackers exploiting WSUS vulnerability drop Skuld infostealer (CVE-2025-59287)
Attackers have been spotted exploiting the recently patched WSUS vulnerability (CVE-2025-59287) to deploy infostealer malware on unpatched Windows servers. An out-of-band …

Researchers expose large-scale YouTube malware distribution network
Check Point researchers have uncovered, mapped and helped set back a stealthy, large-scale malware distribution operation on YouTube they dubbed the “YouTube Ghost …
Featured news
Resources
Don't miss
- Your dependencies are 278 days out of date and your pipelines aren’t protected
- Security debt is becoming a governance issue for CISOs
- BlacksmithAI: Open-source AI-powered penetration testing framework
- When cyber threats start thinking for themselves
- IronCurtain: An open-source, safeguard layer for autonomous AI assistants