
Rayhunter: EFF releases open-source tool to detect cellular spying
The Electronic Frontier Foundation (EFF) has released Rayhunter, a new open-source tool designed to detect cell site simulators (CSS). These devices, also known as IMSI …

Google introduces VaultGemma, a differentially private LLM built for secure data handling
Google has released VaultGemma, a large language model designed to keep sensitive data private during training. The model uses differential privacy techniques to prevent …

AI video surveillance could end privacy as we know it
AI-powered video surveillance brings up big questions about privacy. On one hand, it can make us feel safer, but on the other, it can easily cross the line into intrusion. The …

Product showcase: Clean Links exposes what’s hiding behind a QR code
Clean Links is a handy app that shows you exactly where a link will take you before you click it. It strips out trackers, expands shortened URLs, and helps you avoid scams …

Your heartbeat could reveal your identity, even in anonymized datasets
A new study has found that electrocardiogram (ECG) signals, often shared publicly for medical research, can be linked back to individuals. Researchers were able to re-identify …
When typing becomes tracking: Study reveals widespread silent keystroke interception
You type your email address into a website form but never hit submit. Hours later, a marketing email shows up in your inbox. According to new research, that is not a …
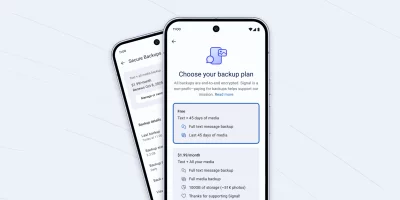
Signal adds secure backup option for chat history
Losing a phone can mean losing years of conversations. Signal is rolling out a new secure backup feature to help users keep their messages safe without giving up privacy. The …

Nearly 500 researchers urge EU to rethink controversial CSAM scanning proposal
Nearly 500 scientists and researchers have signed an open letter warning that the latest version of the EU’s Chat Control Proposal would weaken digital security while failing …

How to reclaim control over your online shopping data
Online shopping is convenient, saves time, and everything is just a click away. But how often do we stop to think about what happens to the data we leave behind, or the risks …

LinkedIn expands company verification, mandates workplace checks for certain roles
LinkedIn is rolling out new verification rules to make it easier to confirm that people and companies are who they claim to be. The company will now require workplace …

Five habits of highly secure development teams
In this Help Net Security video, Brendon Collins, Principal Consultant at Optiv, explores how organizations can embed security and privacy into the software development …

Social media apps that aggressively harvest user data
Both domestic and foreign technology companies collect vast amounts of Americans’ personal data through mobile applications, according to Incogni. Some apps leverage data for …