
QR codes are getting colorful, fancy, and dangerous
QR codes have become a routine part of daily life, showing up on emails, posters, menus, invoices, and login screens. Security-savvy users have learned to treat links with …

CISOs flag gaps in third-party risk management
Third-party cyber risk continues to concern security leaders as vendor ecosystems grow, supply chains stretch, and AI plays a larger role in business operations. A recent …

Cybersecurity spending keeps rising, so why is business impact still hard to explain?
Cybersecurity budgets keep climbing, but many security leaders still struggle to explain what that spending delivers to the business. A new study by Expel examines that …

The NSA lays out the first steps for zero trust adoption
Security pros often say that zero trust sounds straightforward until they try to apply it across real systems, real users, and real data. Many organizations are still sorting …

Webinar: Beyond the Quadrant: An Analyst’s Guide to Evaluating Email Security in 2026
Join former Gartner analyst Ravisha Chugh and Abnormal’s Director of Product Marketing, Lane Billings, on January 20th for an exclusive insider look at how email security …

Anthropic backs Python Software Foundation security work with $1.5 million
Anthropic has signed a two-year partnership with the Python Software Foundation (PSF), committing a total of $1.5 million to support the foundation’s work, with a focus on …

CISO Assistant: Open-source cybersecurity management and GRC
CISO Assistant is an open-source governance, risk, and compliance (GRC) platform designed to help security teams document risks, controls, and framework alignment in a …

Firmware scanning time, cost, and where teams run EMBA
Security teams that deal with connected devices often end up running long firmware scans overnight, checking progress in the morning, and trying to explain to colleagues why a …

How AI image tools can be tricked into making political propaganda
A single image can shift public opinion faster than a long post. Text to image systems can be pushed to create misleading political visuals, even when safety filters are in …

Product showcase: Orbot – Tor VPN for iOS
Orbot for iOS is a free, open-source networking tool that routes supported app traffic through the Tor network. Developed by the Guardian Project, it is intended for users who …
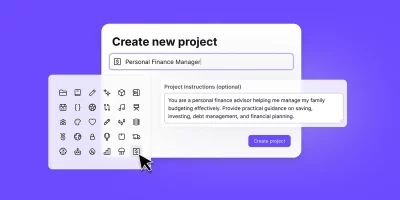
Proton expands Lumo AI assistant with encrypted, project-based workspaces
Lumo is Proton’s AI assistant, built with a focus on privacy and user control. It runs on Proton’s infrastructure and is designed so conversations are not used to train models …

Wine 11 brings major architectural work, synchronization changes, 600+ bug fixes
Wine, originally short for “Wine Is Not an Emulator,” is a compatibility layer that allows Windows applications to run natively on POSIX-compliant operating systems, including …
Featured news
Resources
Don't miss
- State-backed phishing attacks targeting military officials and journalists on Signal
- Poland’s energy control systems were breached through exposed VPN access
- CISA orders US federal agencies to replace unsupported edge devices
- Ransomware attackers are exploiting critical SmarterMail vulnerability (CVE-2026-24423)
- February 2026 Patch Tuesday forecast: Lots of OOB love this month