
International sting dismantles illegal streaming empire serving millions
Actions by authorities from Italy, Romania, Spain, the United Kingdom, Canada, Kosovo and South Korea, supported by Eurojust and Europol, led to the seizure of multiple …

GitHub enables multi-agent AI coding inside repository workflows
GitHub has expanded Agents HQ, enabling AI coding agents such as GitHub Copilot, Claude by Anthropic, and OpenAI Codex to execute development tasks directly within GitHub and …

Police shut down global DDoS operation, arrest 20-year-old
Police officers from Poland’s Central Bureau for Combating Cybercrime (CBZC) have arrested a 20-year-old man suspected of carrying out global DDoS attacks targeting …
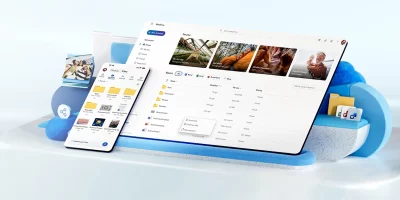
Microsoft brings project-focused AI agents into OneDrive
Teams often rely on shared document collections to track project history, decisions, and operational knowledge. To support this workflow, Microsoft introduced Agents in …

Microsoft launches LiteBox, a security-focused open-source library OS
Microsoft has released LiteBox, a project intended to function as a security-focused library OS that can serve as a secure kernel for protecting a guest kernel using …

Smart glasses are back, privacy issues included
AI smart glasses are the latest addition to fashion, and they include a camera, a microphone, AI, and privacy risks. After Google Glass failed to gain traction more than a …

AI is driving a new kind of phishing at scale
Email remains a primary entry point for attackers, and security teams continue to manage high volumes of malicious messages that change form across campaigns. Attackers …

Cybersecurity planning keeps moving toward whole-of-society models
National governments already run cybersecurity through a mix of ministries, regulators, law enforcement, and private operators that own most critical systems. In that …

Measuring AI use becomes a business requirement
Enterprise teams already run dozens of AI tools across daily work. Usage stretches from code generation and analytics to customer support drafting and internal research. …

Incognito dark web drug market operator gets 30 years in prison
Rui-Siang Lin, a Taiwanese national, was sentenced to 30 years in U.S. federal prison for operating Incognito Market, one of the world’s largest illicit online narcotics …

Major vulnerabilities found in Google Looker, putting self-hosted deployments at risk
Researchers at Tenable have disclosed two vulnerabilities, collectively referred to as “LookOut,” affecting Google Looker. Because the business intelligence platform is …
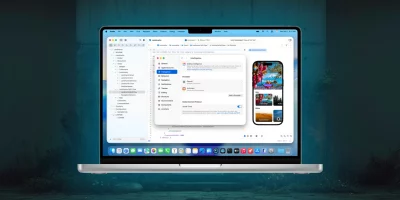
Apple Xcode 26.3 adds coding agent support from OpenAI and Anthropic
Apple released Xcode 26.3 with new agentic coding capabilities designed to let AI systems carry out development tasks inside the IDE. The release supports agents such as …
Featured news
Resources
Don't miss
- State-backed phishing attacks targeting military officials and journalists on Signal
- Poland’s energy control systems were breached through exposed VPN access
- CISA orders US federal agencies to replace unsupported edge devices
- Ransomware attackers are exploiting critical SmarterMail vulnerability (CVE-2026-24423)
- February 2026 Patch Tuesday forecast: Lots of OOB love this month