
Global Threat Map: Open-source real-time situational awareness platform
Global Threat Map is an open-source project offering security teams a live view of reported cyber activity across the globe, pulling together open data feeds into a single …

How Secure by Design helps developers build secure software
Security isn’t just a feature, it’s a foundation. As cyber threats grow more sophisticated and regulations tighten, developers are being asked to do more than just write clean …

Why incident response breaks down when it matters most
In this Help Net Security video, Jon David, Managing Director, NR Labs, discusses why incident response often breaks down during a breach. Drawing on years of experience …

Auto finance fraud is costing dealers up to $20,000 per incident
Auto retailers see fraud as a regular part of selling and financing vehicles, something that shows up often enough to plan around, according to Experian. Income and identity …

Russian hackers are exploiting recently patched Microsoft Office vulnerability (CVE-2026-21509)
Russian state-sponsored hackers Fancy Bear (aka APT 28) are exploiting CVE-2026-21509, a Microsoft Office vulnerability for which Microsoft released an emergency fix last …

Download: Tines Voice of Security 2026 report
Security teams everywhere are adopting AI. Yet manual work persists, workloads are rising, and burnout continues to climb. To understand what’s really changing, Tines surveyed …

Notepad++ supply chain attack: Researchers reveal details, IoCs, targets
Rapid7 researchers have attributed the recent hijacking of the Notepad++ update mechanism to Lotus Blossom (aka Billbug), a Chinese state-sponsored group known for targeting …

Sandisk brings SPRandom to open source for large SSD testing
Enterprise storage environments already run long qualification cycles as solid-state drive capacities rise and validation teams try to mirror production workloads. …
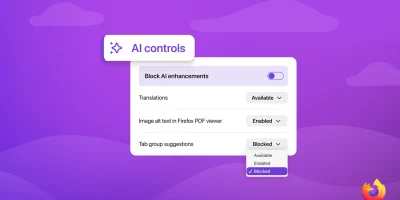
Firefox to let users manage and block AI features
Mozilla will add a set of controls in Firefox that let users manage and block GenAI features in the desktop browser. The controls will be included in Firefox version 148 on …
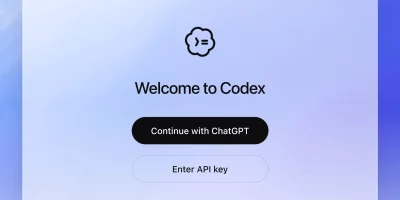
OpenAI releases Codex macOS app for agent-based software development
OpenAI has launched the new Codex app for macOS, a dedicated workspace for managing multiple AI coding agents in parallel. The app is designed to help developers reduce …

Why boards must prioritize non-human identity governance
Boards of Directors (BoDs) do three things exceptionally well when cyber is framed correctly. They set risk appetite, they allocate capital, and they demand evidence that the …

Open-source attacks move through normal development workflows
Software development relies on a steady flow of third-party code, automated updates, and fast release cycles. That environment has made the software supply chain a routine …
Featured news
Resources
Don't miss
- State-backed phishing attacks targeting military officials and journalists on Signal
- Poland’s energy control systems were breached through exposed VPN access
- CISA orders US federal agencies to replace unsupported edge devices
- Ransomware attackers are exploiting critical SmarterMail vulnerability (CVE-2026-24423)
- February 2026 Patch Tuesday forecast: Lots of OOB love this month