Tuesday is the most active day for threats
The most active day for threat-related traffic worldwide is Tuesday, with Monday a close second, according to a report by SonicWALL. This pattern holds true for the U.S., China, India, Mexico, South Africa, Taiwan, Turkey, and several European countries.
The most active time for threat-related traffic in the United States is between the hours of 10:00 a.m. and 11:00 a.m., Pacific Time.

China and Taiwan top the list as the most heavily hit countries for worldwide threat-related traffic. Taiwan, New Zealand and South Africa are the countries most heavily hit with malware.
The Netherlands, China and Taiwan lead the list for the most heavily hit countries with intrusion-related threats and multimedia threats.
Within the GRID, the most popular poisoned Google search terms during year 2010 were related to the Oscar awards. Search terms included: “what time do the Oscars start,” “Oscars 2010 tv schedule,” “academy awards 2010 time,” “Oscar ballot 2010 printable” and “Oscar winners 2010 list.”.
Viruses continue to infect computers and networks worldwide. Top malware threats prevalent during 2010 were Conficker worm, Bredolab Trojans, Zeus Bots, SpyEye Bots, FakeAV Trojans, Oficla Trojans, as well as malwares and Web exploit kits such as Gumblar and Phoenix.
Seasonal trends governed the occurrence of most computer exploits. Over the last three years, SonicWALL’s signature hits indicating viruses, worms, Trojans and other forms of malware revealed these seasonal trends:
- Trojans peak in September and December, corresponding with the proliferation of back-to-school offers and holiday greeting cards
- Worms spike in December, correlating with the winter holidays
- Adware threats peak in September, October and December, correlating to more ads offered up from online advertisers trying to reach a more receptive online audience.
Malware activity in 2010 has already increased with the onset of the holiday season. This year alone, the amount of malware has tripled compared to year 2009. Overall, it is expected to become twice the levels seen for the same period over the previous two years:
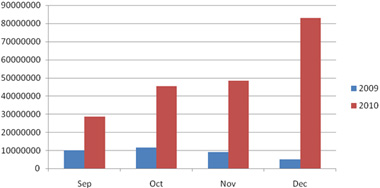
Phishing fraud and website spoofing continue to be serious problems. As online transactions continue to grow, the number of emails soliciting people to go to bogus websites, too. Consumers entering personal data on falsified Web pages risk having their identity stolen, their finances hijacked or their computers downloading unwanted and malicious software.
“These findings give IT administrators insight how to best prepare their networks for the upcoming year,” said Yanovsky. “With increasing proliferation of web security threats, signatures can’t keep up – heuristics, algorithms and behavioral analysis are needed to supplement signatures with proactive analysis. In addition to new social media threats, malware threats and the proliferation of fake AV software telling people that their computers are infected, IT also needs to think through security strategies for attacks focused on the Mac computer and mobile devices in 2011.”