The execution of the RSA hack
More than two weeks have passed since the high profile RSA hack, and the company has finally decided to share some of the details regarding the attack.
The question that is uppermost on most people’s minds – What information did the attacker manage to get their hands on? – still remains unanswered, but at least we now know how he managed to breach the company defenses.
It all started with a malicious email, to which was attached a specially crafted Excel file that contained a zero-day exploit. The exploit took advantage of an Adobe Flash vulnerability (CVE-2011-0609) to install a backdoor that would be used by the attacker to get insight into the inner workings of the firm and tunnel their way into the system.
“The attacker in this case sent two different phishing emails over a two-day period. The two emails were sent to two small groups of employees; you wouldn’t consider these users particularly high profile or high value targets,” explained RSA’s Uri Rivner, Head of New Technologies. “The email subject line read ‘2011 Recruitment Plan.’ The email was crafted well enough to trick one of the employees to retrieve it from their Junk mail folder, and open the attached excel file. It was a spreadsheet titled ‘2011 Recruitment plan.xls’.”
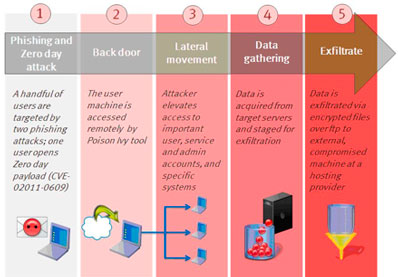
After having back-doored the machine, the attacker installed a variant of the Poison Ivy remote administration tool, which allowed the attacker to shoulder-surf and discover the employee’s role and his or hers level of access.
“When it comes to APTs it is not about how good you are once inside, but that you use a totally new approach for entering the organization,” wrote Rivner. “You don’t bother to just simply hack the organization and its infrastructure; you focus much more of your attention on hacking the employees.”
And while he stressed that Advanced Persistent Threats are a new attack doctrine that is built to circumvent the existing perimeter and endpoint defenses and that it will take a while for the security industry to devise new ways of defending itself and its clients, he pointed out that the attack was detected by the company’s Computer Incident Response Team while it was still in progress.
Comparing APTs to stealth fighters, he explained that APTs do not “defeat” security products, but “find ways to fly below the existing technology.”