Exploit kit targets Android devices, delivers ransomware
Ransomware hitting mobile devices is not nearly as widespread as that which targets computers, but Blue Coat researchers have discovered something even less common: mobile ransomware delivered via exploit kit.
The ransomware in question calls itself Cyber.Police (the researchers have dubbed it Dogspectus), and does not encrypt users’ files, just blocks the infected Android device. It purports to be part of an action by the (nonexistent) “American national security agency” against unspecified illegal actions ostensibly performed by the user:
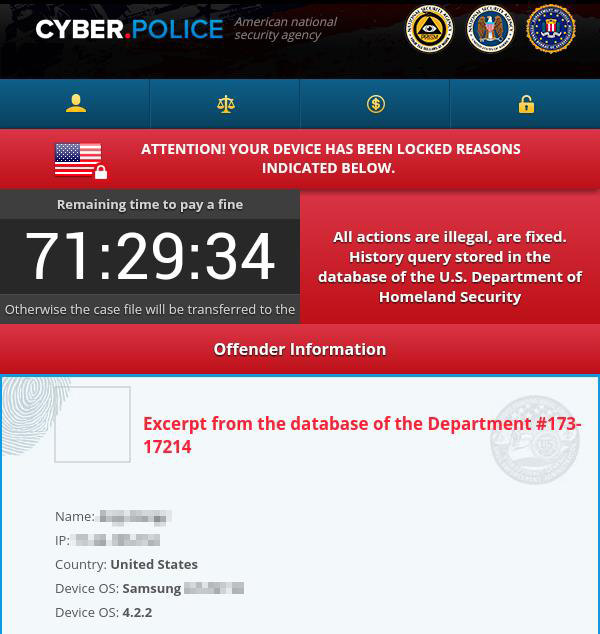
The criminals behind this scheme want the victim to buy two $100 Apple iTunes gift cards and send the cards’ codes to them.
“In this iteration of the malware, we found that we were still able to connect the infected device to a computer and copy the unmodified documents, photos, and other files from both the device’s internal memory and any additional storage card(s) that may be installed,” the researchers found. “The malware survived flashing over the operating system with a newer build of Android, but did not persist after a factory reset, which deletes any applications installed by the device’s user.”
But now onto the most interesting thing about this attack: the researchers’ test Android device was infected with the ransomware when an advertisement containing a malicious JavaScript loaded from a Web page.
Further analysis and consultation with other experts revealed that:
- The malicious JavaScript contained an exploit against libxslt that was leaked during the Hacking Team breach, and that its payload contains the code for the “Towelroot” exploit
- Since February 22, at least 224 unique device models running Android versions between 4.0.3 and 4.4.4 have contacted domains from which the attack originated, and given that some of these devices/OS versions are not vulnerable to the aforementioned Hacking Team exploit, it seems logical that they were infected through different ones.
“This is the first time, to my knowledge; an exploit kit has been able to successfully install malicious apps on a mobile device without any user interaction on the part of the victim,” noted researcher Andrew Brandt, and added that during the attack, the device did not display the normal “application permissions” dialog box that typically precedes the installation of an Android application.
“The commoditized implementation of the Hacking Team and Towelroot exploits to install malware onto Android mobile devices using an automated exploit kit has some serious consequences. The most important of these is that older devices, which have not been updated (nor are likely to be updated) with the latest version of Android, may remain susceptible to this type of attack in perpetuity,” he pointed out.