FlockFlock: File access enforcement for macOS
The more serious you are about information security, the more you realize it’s difficult to be sure a system isn’t compromised. While malware authors don’t target the Mac platform as much as Windows, it doesn’t mean you should be complacent about its security.
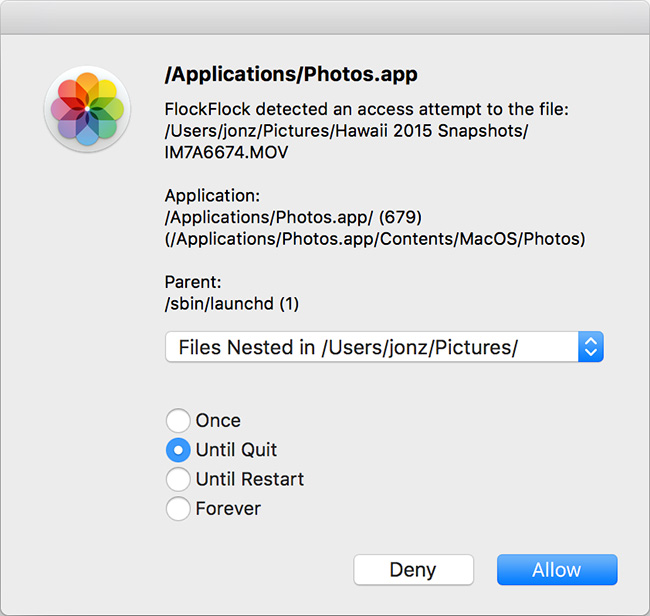
FlockFlock is an open source tool for macOS aimed at protecting your files. This versatile piece of software, created by iOS security expert Jonathan Zdziarski, can ensure that the applications you’re using are respecting your privacy and it can tell you if your system has been compromised. It does all that by preventing unauthorized processes from being able to open, read, or destroy your files without your permission.
FlockFlock is an IOKit based driver, and the source code should help you understand complex concepts such as mach messages, user-space client communication, driver construction, memory and locking, and much more.

“Apple adopted the MAC policy framework from TrustedBSD and have been using it for sandboxing. The MAC (mandatory access control) framework gives the kernel a lot of granularity over what features can be controlled on a system-wide level,” explains Zdziarski.
FlockFlock takes advantage of this, and monitors for any unauthorized file activity. By running at kernel level, FlockFlock is able to protect against a broad range of userland compromises, such as userland spyware, malware, rootkits, trojanized apps, and apps that just don’t respect your privacy.
Development challenges
Apple has gone to great lengths to make many crucial kernel interfaces opaque to the developer, which complicated the development of FlockFlock.
“Since Apple’s the one granting kext signing privileges for your code, you can’t just skirt around them using the usual hacking methods – you have to play by their rules. I’ve written hundreds of lines of extra code to make up for basic interfaces that Apple has intentionally hidden. For example, I can’t access a proc struct directly in order to find out what the executing binary’s path is, and so I had to hook into a handful of other frameworks to receive notifications and try to track the process through multiple spawns. It’s still not perfect, all because Apple’s hidden any APIs (which exist in userland) like proc_pidpath(),” says Zdziarski.
He goes on to explain why Apple did this:
1. They want developers using userland as much as possible.
2. To reduce the overall attack surface by reducing the amount of code running in the kernel.
3. To avoid exposing potentially unsupported interfaces that may change.
The problem is this inherently weakens security of macOS because:
1. Anything running in userland is more easily tampered with by malware, so writing a security tool into userland makes it more vulnerable.
2. By reducing the amount of Apple’s (peer reviewed) code, they’ve caused developers to increase their own attack surface by adding hundreds of lines of code needed to do basic tasks.
Future plans
Some of the primary goals include finishing off the UI and writing a rules editor, says Zdziarski.
“I’d also like to incorporate a ‘simple mode’ for novice users that will act more like Apple’s privacy prompts. For example, instead of giving you all of the granularity FlockFlock gives you now with directories, parent processes, and options, simply popping up a window that says, ‘Application X would like access to your Photos’ or ‘Application X would like access to your Documents’ might be enough (although obviously not as effective) to get novice users to protect themselves,” he concluded.