Telegram-based Katyusha SQL injection scanner sold on hacker forums
Despite regularly achieving one of the top spots on the OWASP Top 10 list of the most critical web application security risks, injection vulnerabilities continue to plague database-driven web sites and get regularly exploited by attackers.
And when we talk about injection attacks, SQL injections are the most prominent, mostly because SQL databases are ubiquitous, and the attackers often succeeding in dumping the contents of the entire database.
“The severity of SQL Injection attacks is limited by the attacker’s skill and imagination, and to a lesser extent, defense in depth countermeasures, such as low privilege connections to the database server and so on,” OWASP notes.
SQL injection flaws are easy to detect and easy to exploit, and automated tools like the Katyusha Scanner make the first step of finding vulnerable websites even easier and less dependent on the attacker’s skill.
Tools for the hacking masses
The tool, named after the iconic Soviet rocket launcher, is a fully automated SQLi vulnerability scanner based on the open source Arachni web app security scanner for penetration testers.
According to Recorded Future researchers, it is offered for sale by a Russian-speaking member of a top-tier hacking forum, and is frequently updated. Judging by the reviews, the author offers good tech support to customers that have paid for the tool ($500 for a professional version, $250 for a “light” one) or have just rented it (at $200 per month).
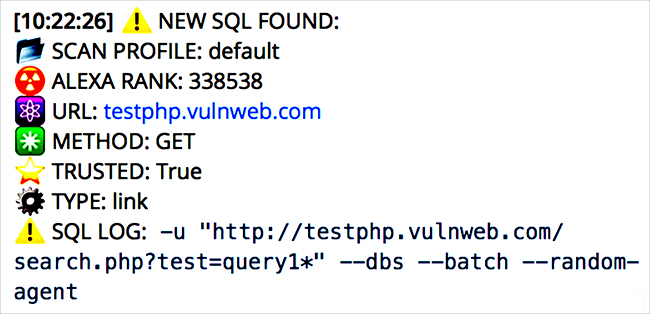
The Katyusha Scanner can be operated via a standard web interface and its operation monitored via the Telegram messenger:

Users can insert a list of websites they want tested for error-based, time-based and blind SQL injection flaws, and it will fire off attacks against several targets simultaneously.
Apart from identifying vulnerabilities, the tool can also search for and export email/password credentials, brute-force login credentials, and automatically dump databases and upload web shells.
Once the scan is completed, Katyusha will display an Alexa web rating for each target (for an immediate visibility into the popularity of the resource), and details about the found vulnerability.
The tool can scan for SQL injection flaws in applications that take advantage of a variety of popular relational databases that use SQL as the language for queries and maintenance (e.g. MySQL, MSSQL, DB2, SaP Max DB, Oracle, MS Access, PostgreSQL, and so on).
“The availability of a highly robust and inexpensive tool such as Katyusha Scanner to online criminals with limited technical skills will only intensify the compromised data problem experienced by various businesses, highlighting the importance of regular infrastructure security audits,” the researchers noted, and advised administrators to take note and take action to protect assets under their control.
“Common defenses against SQL injection attacks include using parameterized statements as opposed to concatenating strings in code, using object relational mapping frameworks to generate SQL statements, proper escaping of special string characters in input parameters, and sanitizing inputs that appear suspicious,” they added.