Sqrrl empowers threat hunters with self-service analytics
Today, analysts must either have advanced data science skills to build hunting algorithms that detect suspicious cyber behaviors or rely on blackbox vendor tools that package rigid algorithms. Sqrrl Enterprise 2.8 introduces the ability for analysts to easily create new hunting analytics without writing any code or having any data science skills. These analyst-defined analytics are referred to as “Risk Triggers.”
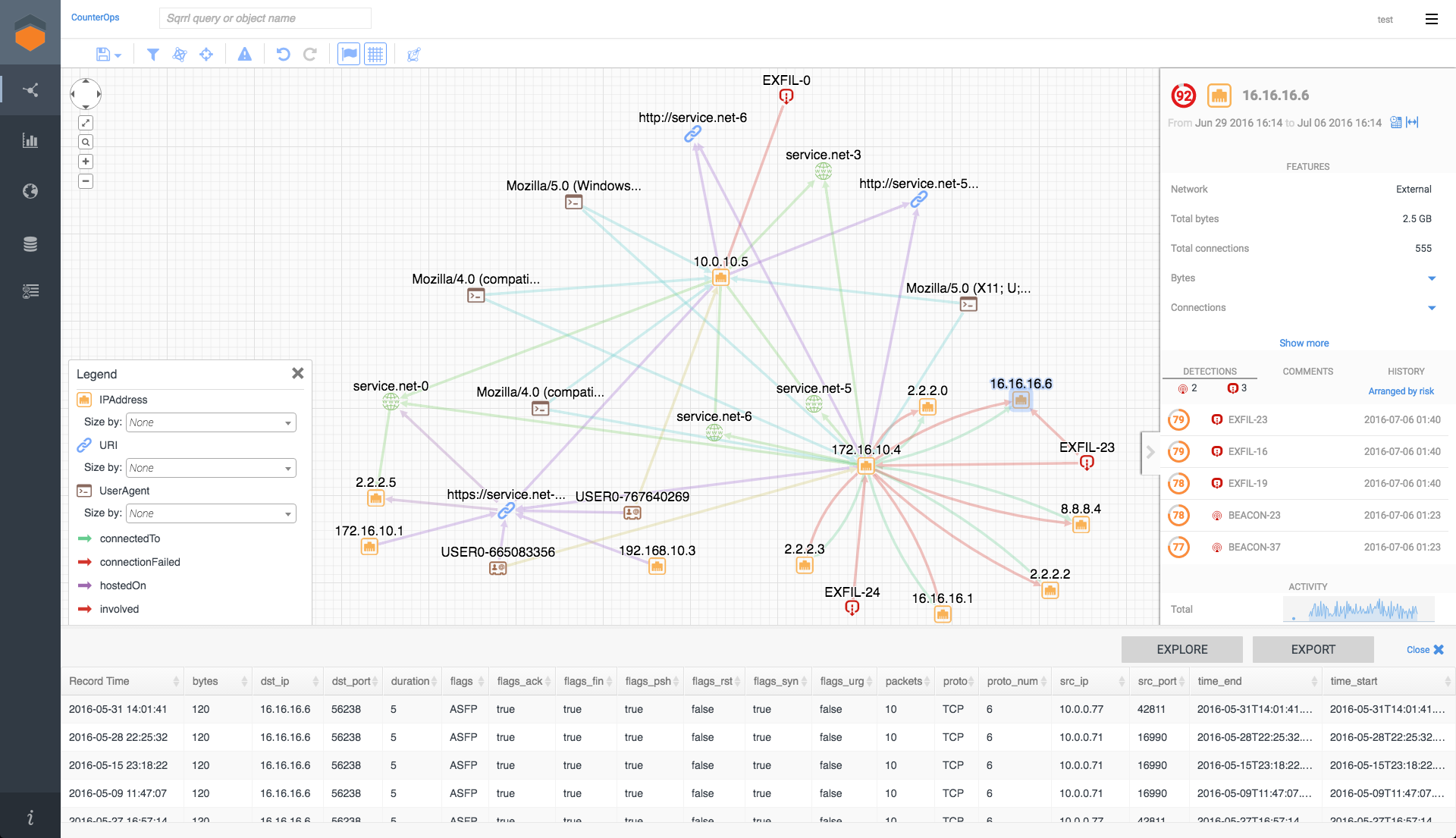
The Sqrrl UI, featuring graph exploration, detailed entity information, and drill down on the underlying raw data
“The best threat hunters accelerate hunts by focusing on the relationships between alerts, threat intelligence, and data points, “ says Eric Ogren, senior security analyst at 451 Research. “It is essential to be able to evaluate risky behavior while hunting threats – a key feature of Risk Triggers. Not only does this accelerate their hunts, it makes it easy for hunters to experiment and get the most value out of their data.” he said.
Sqrrl Enterprise 2.8 also includes an extensible risk framework, risk timelining capability and a number of supporting platform features that simplify Sqrrl’s form of link analysis across key security data sources.
Analyst-defined threat hunting analytics
Sqrrl’s new Risk Trigger framework enables the easy creation of custom-built threat hunting analytics. Risk Triggers use Sqrrl’s graph query syntax to automatically find patterns, and analysts can integrate advanced anomaly detection capabilities into the triggers without having to write any code.
Analysts can create Risk Triggers to do such actions as detect threat intelligence matches, identify abnormal user or asset activity, and uncover suspicious connections between entities.
Extensible risk framework and risk timelining
With Sqrrl’s new extensible risk framework, Sqrrl provides a view of risky activity across the organization. Using Risk Triggers, Sqrrl can calculate risk scores on every user, IP address, host, and domain inside the organization by fusing together Sqrrl’s analytics with external sources of risk such as SIEM alerts, threat intelligence, and vulnerability scans.
Risky activity is now displayed as a timeline on each user, asset, and entity to provide analysts with a view of how risk and security postures are evolving over time.
Custom-defined risk triggers automatically run in the background for future threat hunting analysis, with results appearing on the Entities Identified by Triggers list
Other key features
Streamlined link analysis: The enhanced interface makes it much easier for analysts to pivot through data, build attack narratives more quickly, and enables more junior analysts to take on advanced hunting.
Simplified graph data extraction: Improvements to the backend of Sqrrl’s Security Behavior Graph, enable security architects to more easily extract the most important fields needed for hunting from incoming data feeds and automatically fuse those fields into hunting data models. This enables organizations to integrate new datasets more quickly and spend more time on hunting and less time on data modeling.
Integration of Threat Intelligence feeds: Threat intelligence data across multiple sources can easily be populated into Sqrrl’s Security Behavior Graph, enabling analysts to track the most recent indicator hits and develop risk triggers that translate intel into tailored insights.