IoT botnet bypasses firewalls to get to ZyXEL modems
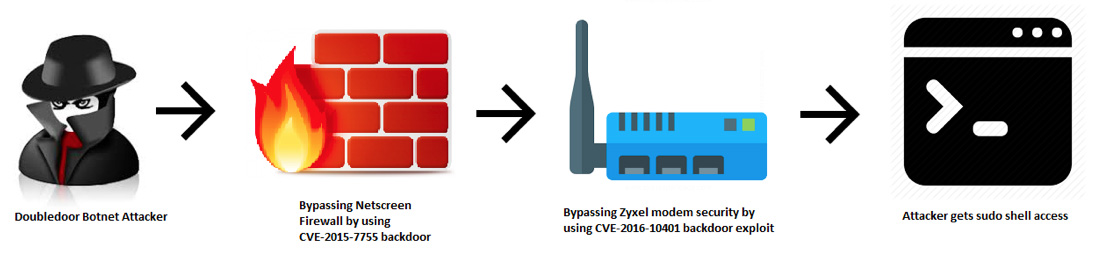
NewSky Security’s honeypots have detected a new IoT botnet in the making. The botnet was named DoubleDoor, as it leverages two distinct backdoors to get to the target: ZyXEL PK5001Z modems.
The DoubleDoor attacks
What’s interesting about this particular botnet is that it’s ready to pass an extra layer of security to get to the modem: Juniper Networks’ NetScreen hardware firewall devices.
To pull off the attack, it employs exploits for two vulnerabilities:
-
CVE-2015–7755, which affects the firewall’s ScreenOS software, allows attackers to access telnet and SSH daemons of the firewalls by simply using any random username in combination with a specific hardcoded password. DoubleDoor uses netscreen for the username:

The vulnerability was discovered by Juniper in December 2015 and was suspected to be the work of state-sponsored intruder. The flaw has since been patched.
- CVE-2016–10401, a backdoor for ZyXEL PK5001Z devices.
Once they’ve gotten past the firewall, the attackers performed a password-based attack to get a basic privilege account like admin:CenturyL1nk. Then they use CVE-2016–10401 to escalate their privilege lever and get a superuser account (and complete control of the device).
This particular exploit has previously been used by the infamous Mirai botnet.
Another interesting thing about DoubleDoor is that it uses randomized strings for invoking the shell to check whether the target IoT device has been successfully taken over.
“Many attackers use a variety of strings here to serve this purpose. Many use the botnet name itself (like MIRAI, ASUNA, MASUTA, SATORI) or their own pseudonym like daddyl33t,” NewSky Security’s researchers noted.
DoubleDoor eschews that approach, and uses a randomized, 8-character string in every attack so that this reconnaissance activity is not easily classified.
A botnet in the making
This particular set up (NetScreen firewall + Zyxel modem) is more likely to be found in corporate environments than private homes, which is possibly why the attackers are looking for these specific targets.
“Getting control of corporate environment routers can be more valuable for an attacker as it can lead to targeted IoT attacks,” the researchers noted.
The DoubleDoor botnet attacks seem to be in its nascent phase, as we observed the attacks only for a period from 18th January 2018 until 27th January 2018. Despite the code being interesting, the count of devices in this specific DoubleDoor attack is expected to be low as the hack will succeed only if the victim has a specific unpatched version of Juniper ScreenOS firewall which protects unpatched Zyxel modems.”
UPDATE (February 17, 2018):
Ruben Landeros Jr., Director of Information Technology at Zyxel, told us that CVE-2016–10401 has been corrected through a solution that they provided to their customers (CenturyLink) in December 2017, and the latter deployed it shortly after.