Telegrab: Russian malware hijacks Telegram sessions
Researchers have discovered and analyzed an unusual piece of malware that, among other things, seeks to collect cache and key files from end-to-end encrypted instant messaging service Telegram.
The malware’s capabilities
Cisco Talos researchers Vitor Ventura and Azim Khodjibaev dubbed the malware Telegrab.
They analyzed two versions of it. The first one, discovered on April 4, 2018, only stole browser credentials, cookies, and all text files it can find on the system. The second one, spotted less than a week later, is also capable of collecting Telegram’s desktop cache and key files and login information for the Steam website.
To steal Telegram cache and key files, the malware is not taking advantage of software flaws. The malware is capable of targeting only the desktop version of the popular messenger because it does not support Secret Chats and does not have the auto-logout feature active by default.
This means that the attacker can use those stolen files to access the victim’s Telegram session (if the session is open), contacts and previous chats.
Telegrab is distributed via a variety of downloaders, and it checks if the victim’s IP address is part of a list that includes Chinese and Russian IP addresses, along with those of anonymity services in other countries. If it is, it will exit.
It also doesn’t have a persistence mechanism, so it won’t work after a system reboot.
The stolen data and files are exfiltrated to one of five pCloud accounts (pCloud is a Switzerland-based cloud storage solution). They are not encrypted, so technically anyone who has the credentials to those accounts or gets their hands on them can access this information.
“The malware samples analysed are not particularly sophisticated but they are efficient,” the researchers noted.
“Notably the Telegram session hijacking is the most interesting feature of this malware, even with limitations this attack does allow session hijacking and with it the victim’s contacts and previous chats are compromised.”
They also pointed out that the malware should be considered a wake up call to encrypted messaging systems users. “Features which are not clearly explained and bad defaults can put in jeopardy their privacy,” they pointed out.
About Telegrab’s creator
The researchers are pretty confident that the creator of the malware is a native Russian speaker that goes online by “Racoon Hacker” or “Eyenot”.
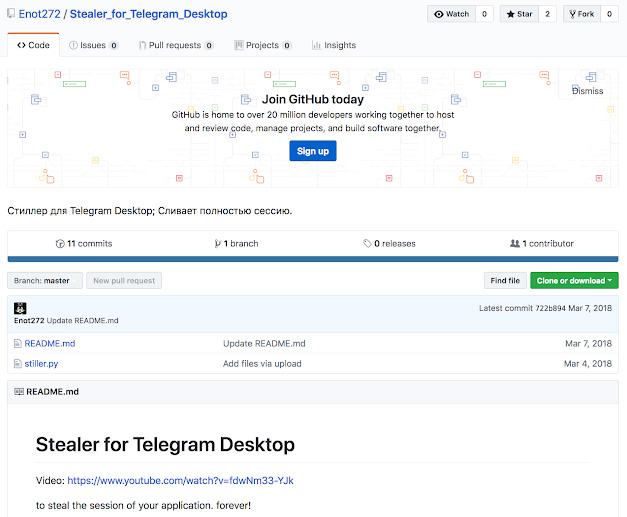
This individual posted online a number of posts and videos that relates to other account hijackers or development of payload loaders, shows how to steal Telegram sessions, etc. Information gleaned from these videos point to Racoon Hacker/Eyenot, who is also very active on Russian hacking forums and has a GitHub account.