AttackSurfaceMapper automates the reconnaissance process
AttackSurfaceMapper, a new open source OSINT tool created by Andreas Georgiou and Jacob Wilkin, security consultants at Trustwave SpiderLabs, automates the process of collecting data that can help pentesters find a way into targets’ systems and networks.

About AttackSurfaceMapper
Reconnaissance is an important first step of a penetration testing engagement, but manual reconnaissance is a drag and wastes time that’s better spent on the actual attack.
“AttackSurfaceMapper drastically improves pentesting and red team operations across the security community by automating the time-consuming reconnaissance phase during engagements. It greatly softens the burden by executing all the repetitive processes and generating a list of files that can be then imported in other tools to perform further enumeration, scanning and exploitation,” Georgiou told Help Net Security.
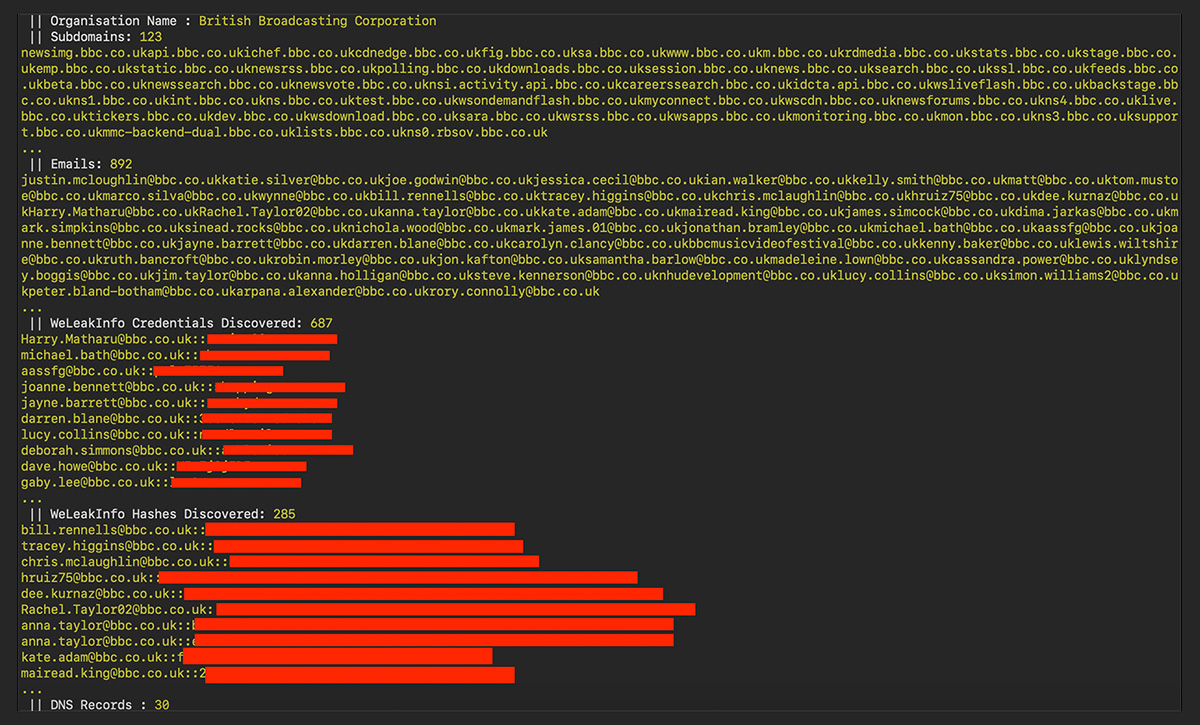
Using is it easy as plugging in the target domain and letting it run. The tool will:
- Find IPs from associated ASNs and IPv4 prefixes
- Passively discover Subdomains and/or brute force subdomains
- Perform port scanning
- Perform hostname discovery
- Perform passive and active DNS record capturing
- Collect WHOIS records
- Take screenshots of web portals
- Query a mix of public and private APIs, including Shodan Engine, WeleakInfo and VirusTotal
- Scrap employee names and email addresses from LinkedIn
- Check for credentials in public data breaches
- Download interesting files (e.g., PDF and XML)
- Find AWS buckets.
The results are presented on the terminal and can be exported in HTML, CSV and TXT form.
“Two of the most powerful features of ASM supports are the ‘Expand’ and ‘Stealth’ modes. When the ‘Expand’ mode is enabled the tool attempts to aggressively identify additional IP address ranges and subdomains related to the target. On the other hand, the “Stealth” functionality, as the name suggests, does not generate any traffic to the target allowing the tester to collect data about the target without triggering any alerts,” Georgiou explained.
AttackSurfaceMapper is a Python-based modular tool and is (theoretically) compatible with all major operating systems.
“The tool is modular in the sense that block of code can be imported by including additional features and data sources in the future. Anyone can write a module and plug it in following the data structure and output format,” Georgiou noted.
“However, it’s not modular in the same as other frameworks are (e.g., Metasploit). Rather than requiring the user to manually load and run specific modules, it’s designed to work fully automatic.”
He also says that, while the process is automatic, it can last quite some time.
“AttackSurfaceMapper can sometimes take several hours to run on multiple targets when expand mode is enabled or if multiple targets are specified. Once expand mode is enabled, ASM might include subdomains or IP addresses that are related but not owned by the target company,” he explained.
Georgiou and Wilkin are demonstrating the tool at the Black Hat USA 2019 Arsenal and at DEFCON (the Recon Village).