Product showcase: Awake Security Network Traffic Analysis Platform
Security experts profess that enterprise organizations must assume their network is already compromised. Cyber-attacks use network communications for malware distribution, command and control, and data exfiltration. With the right tools, security professionals should be able to uncover malicious activity and take prompt action to mitigate it.
Network traffic analysis (NTA) tools were designed to help security personnel to detect attackers that had managed to evade traditional defenses, especially those that are already inside the perimeter. As with many new technologies NTA suffered from teething problems, most notably a very high volume of alerts for “anomalous” behavior or “IOCs” that didn’t actually represent an attackers’ presence.
Furthermore, attackers today use a complex set of tactics, techniques, and procedures (TTPs) that are hard to detect because they involve abusing insider privileges, “living off the land” and avoiding malware. These TTPs will often not register as anomalies or exhibit the indicators of compromise that early NTA tools look for.
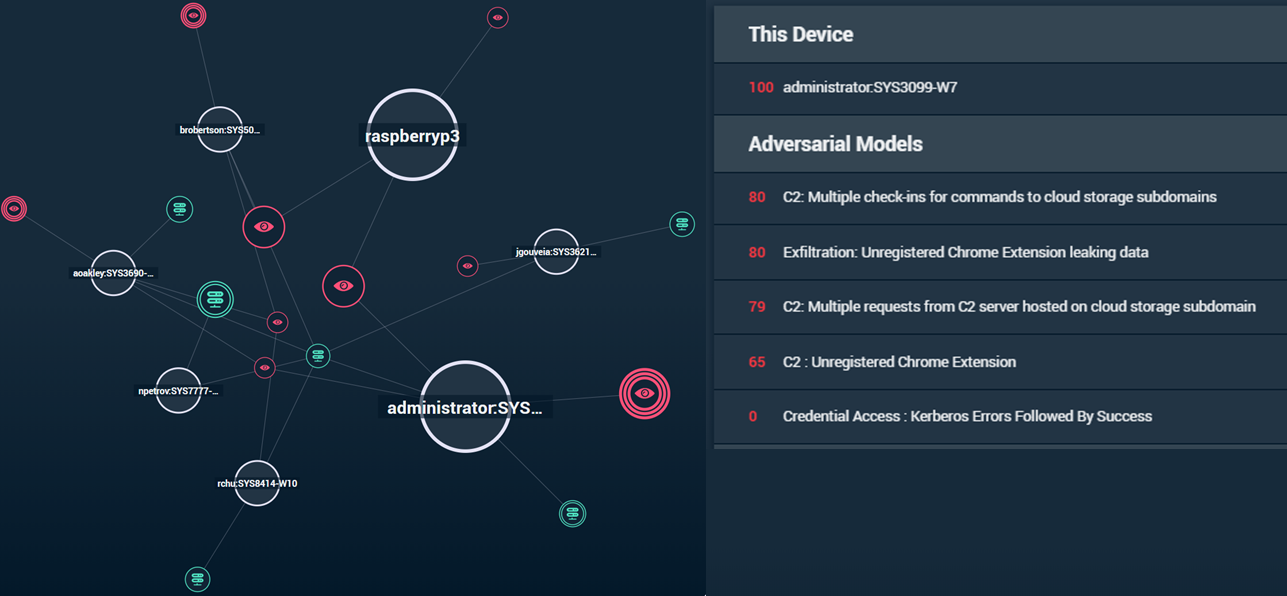
As a security company built by security practitioners, Awake Security has been at the forefront of advanced network traffic analysis—visibility, detection and response for the new network. The platform delivers a full understanding of what business assets you are protecting. Awake Security’s EntityIQ identifies each unique entity on the network including devices, users and applications, many of which are normally invisible to the security team like IoT devices, contractors and third parties and transient mobile systems.

Correlating the entire attack surface with an accurate understanding of an attacker’s tactics and techniques is the key to rapid high fidelity and low noise detection of compromised assets.
The company’s latest platform release includes a new capability that models an attacker’s tactics, techniques and procedures to ensure that detections represent a true indication of the presence of an adversary and malicious intent. This capability, known as Adversarial Modeling, represents a major advancement in the application of artificial intelligence to security.
Adversarial modeling involves multi-dimensional analysis that spans factors including time, entities and protocols. Awake is the only solution that is able to deliver on this capability and thus see and stop attackers, especially those that are living-off-the-land as opposed to using malware.
Adversarial modeling enables full visibility of malicious behavior across the kill chain. Each step in the adversary’s playbook is clearly identified as the attack progresses allowing the security team to quickly and accurately determine the validity, scope and potential impact of the incident.
Evaluating network traffic analysis solutions
The emergence of a new security technology is always accompanied by the challenge of separating hype from reality. To help buyer with this problem, Awake Security worked with The Tolly Group a premier independent test lab and provider of third-party validation services to produce the industry’s first NTA effectiveness test.
Three key trends shaped the details of the test to ensure it addressed the most important problems security teams are experiencing.
- According to a 2018 Threat Report by FireEye, 90% of attacks they observed did not contain malware, but used other tactics like social engineering, credential theft and spear phishing to avoid detection by traditional security controls. The Tolly Group test therefore used no malware and was focused on these newer types of attacks that traditional security controls are blind to.
- Another recent survey from EMA found that 79% of security teams indicated that they are being overwhelmed by the number of security alerts they receive. Based on this research the test was designed to measure the “signal to noise” ratio of the product to determine the ratio of actionable alerts to extraneous or “noisy” alerts.
- And finally, a Ponemon Cost of Malware Containment study estimates the average enterprise spends $1.2m per year validating the accuracy of their security alerts. With the ongoing shortage of security talent, and the increasing amount of data that is processed, ensuring that security teams can efficiently validate alerts was determined to be a key component of the test.
Based on these trends several attack scenarios were tested in a real-life customer environment. These included threats to and from IoT devices, data exfiltration and theft using popular cloud service providers as opposed to known bad domains, living-off-the-land threats that used common system administration tools and, credential theft and misuse of existing privileges.
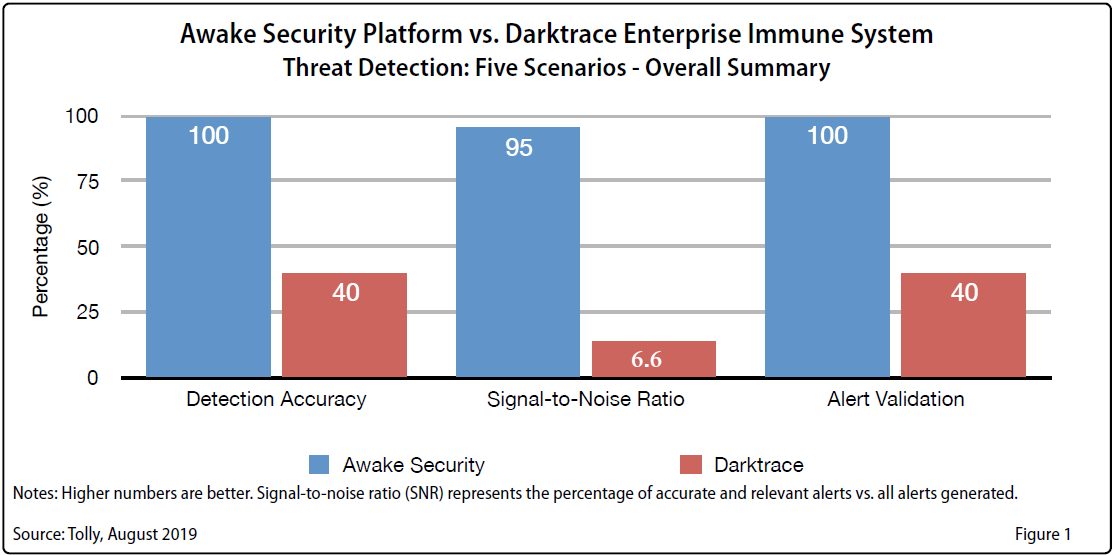
The advanced analytics which forms the cornerstone of any NTA solution require monitoring “real world” traffic. To account for this, the testing was performed in a real customer environment that was evaluating The Awake Security Platform to replace the incumbent Darktrace Enterprise Immune System. In addition, an automated system was also included to faithfully reproduce malicious intent behaviors that are frequently observed in the wild.
The results of this independent test confirmed that the Awake Security Platform was able to detect and validate 100% of the advanced attacks performed in the test. Furthermore, Awake exhibited a 95% “signal to noise” ratio reflecting the ability of adversarial modeling to vastly decrease the number of “noisy” or false positive alerts that have been frustrating security teams using first generation NTA products.