Know your enemy: Mapping adversary infrastructure quickly and accurately
Group-IB is a known quantity in the information security arena: in the sixteen years since its inception, the company – now headquartered in Singapore – has detected and detailed many high-profile threats, performed over a thousand successful investigations across the globe and gained widespread recognition for helping private and public entities and law enforcement worldwide track down and prosecute cybercriminals.
To be able to do that, it has been steadily building an international infrastructure for threat detection, hunting and investigating cybercrime around the world. This infrastructure includes, among other things:
- The largest computer forensics laboratory in Eastern Europe
- An early warning system for proactive cyber defense based on their own threat intelligence, attribution and incident response practices
- A certified emergency response service (CERT-GIB), which is member of the Forum of Incident Response and Security Teams (FIRST) and Trusted Introducer
- Databases containing extensive threat and threat actor information
The company was, at the beginning, mostly a provider of digital forensics and cyber investigation services. In time, though, they realized that the solutions available to organizations were not keeping pace with the ever-morphing threat landscape, so they decided to work on and offer their own.
It all started with the creation of Group-IB Threat Intelligence (TI), an attack attribution and prediction system and service that’s based on data collected from a wide variety of sources (investigations, network sensors, honeypots, OSINT, card shops, and much more), automated information extraction and correlation technologies, and is supported by expert analysts, incident responders and investigators around the world.
It was followed by:
- Group-IB Threat Detection System (TDS) – A threat-actor-centric (instead of malware-centric) detection and proactive threat hunting solution
- Secure Bank – A fraud and attack prevention solution for the financial services industry, which detects threats like account takeovers, credit fraud, malicious web injections, banking trojans, remote access software, social engineering, etc. (keeps more than 100 million banking customers secure by monitoring 16 million online banking sessions every day)
- Secure Portal – A fraud and attack prevention solution for ecommerce websites and online services (prevents account takeovers, identifies fake accounts and blocks bots, fraudulent activities, fraudulent ticket sales, and so on)
- Brand Protection – A service designed to detect and eliminate threats to one’s brand on the Internet (brand abuse, Internet fraud, copyright infringement, counterfeiting)
- Anti-Piracy – intelligence-driven protection of content online
Most of these solutions are powered by Group-IB TI. More recently, though, they gained another thing in common: an integrated Graph Network Analysis system for cybercrime investigations, threat attribution, and detection of phishing and fraud.
Graph Network Analysis
Many threat intelligence solutions have graph-making capabilities and the company has considered a number of graph network analysis providers before finally deciding to develop their own tool for mapping adversary infrastructure, Group-IB CTO and Head of Threat Intelligence Dmitry Volkov told Help Net Security.
None of the considered solutions gathered and used the wide variety of data and historic data Group-IB experts deem crucial for creating a complete picture for better visibility. None of them had the automated graph creation option and were able to reliably identify and exclude irrelevant results. Finally, none allowed operators to specify the ownership timeframe of the entered suspicious domain, IP address, email or SSL certificate fingerprint.
“Domain name and IP addresses change ownership – today they are used by a threat actor, tomorrow by a legitimate company or a random individual, so the timeframe within which the threat actor owned the suspicious domain name or IP address is very important information for the creation of a relevant and accurate graph,” Volkov explained.
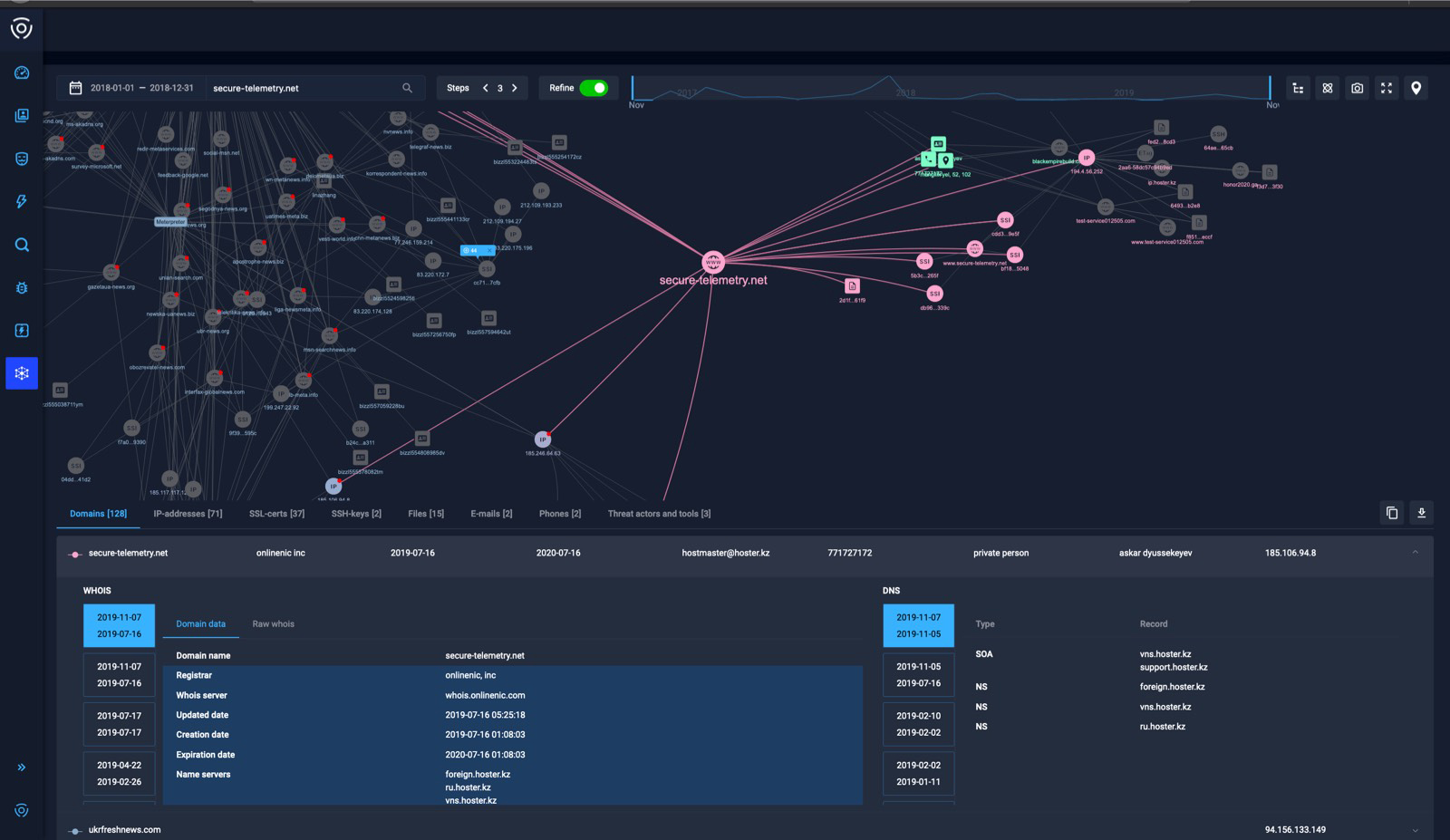
The interface of the graph network analysis tool
The user decides how wide they want to cast the net by specifying the number of steps the tool should take when identifying direct links between elements, but the tool’s automated mode builds the graph of the links to the searched element. And, if they switch on the “refine” option, it will automatically remove from the resulting graph all the elements it deems irrelevant.
The graph network analysis tool attributing the search element to a specific threat actor
Analysts and investigators who don’t trust the tool to create a graph that contains all the crucial elements can always turn “refine” off and specify one step to build the graph themselves and then remove irrelevant elements from it.
Though, Volkov pointed out, after performing numerous manual checks and consistently seeing that the tool did a great job when allowed to do it automatically, their own experts have come to trust and prefer that option.
Improving graph accuracy
“The initial goal was just to create a useful tool for our internal analysts, and we didn’t plan to incorporate it in our products. But some of our clients saw how we were using it to do our research in-house and wanted to be able to do the same, so we decided to share it,” Volkov shared.
The company’s developers and experts have been working on the Graph Network Analysis tool for the past few years. The first version was good, but very slow. In time, they managed to improve both the speed and the effectiveness by experimenting with different types of data and different approaches to data enrichment, processing and correlation.
There are still two versions of the tool: a standalone one that’s used by Group-IB’s experts and one that’s incorporated in the company’s products. New features are first added and tested on the former, then incorporated in the latter if they prove useful.
Group-IB is constantly working on enriching the tool with data and designing new algorithms using machine learning to improve the graph’s accuracy.
“All of Group-IB’s products are being constantly fine-tuned thanks to the permanent monitoring of the cyberspace for new threats and our incident response operations and cyber investigations,” Volkov pointed out. “And we’re always analyzing existing solutions on the market, pinpointing their weak spots and shortcomings, thinking of ways to eliminate them and striving to provide the best technologies to our customers.”
The tool’s capabilities
Mapping adversary infrastructure and (hopefully) identifying the threat actor has many advantages for the targeted organization and its customers, but also for other organizations, their customers and, in general, the wider populace.
“The main goal of network graph analysis is to track down projects that cybercriminals carried out in the past — legal and illegal projects that bear similarities, links in their infrastructure, and connections to the infrastructure involved in the incident being investigated,” Volkov explained.
If the users are very lucky and a cybercriminal’s legal project is detected, discovering their real identity becomes simple. If only illegal projects are detected, that goal becomes more difficult to achieve.
But even if the identity of the attacker remains elusive, discovering details about their previous attacks can help pinpoint their preferred tactics, techniques, procedures, tools and malware, and that information can be handy for disrupting ongoing attacks or even preventing those that are yet to be launched (e.g., by identifying attacker infrastructure at the preparation stage).
The tool can be leveraged by SOC/CERT analysts, threat hunters, threat intelligence analysts and digital forensic specialists, and it’s great for improving the speed of incident response, fast cybercrime investigations, proactive phishing and global threat hunting, and pinpointing malicious servers hidden behind proxy services.
It’s also used for IoC enrichment and event correlation (i.e., discovering when certain attacks are linked and are likely different stages of a single multiphase attack).
Group-IB Graph Network Analysis was designed based on indicators of compromise discovered and collected by the company’s cybercrime investigators, incident responders and malware analysts in the last 16 years.
To this have been added or made available through data-sharing agreements and subscriptions many other data sets containing:
- Domain registration data
- DNS records (domain records, files, profiles, tags)
- Service banners (domains, redirections, error codes)
- Service fingerprints on IP addresses (which services are running and which ports are open)
- Hidden registration data (IDs, hosting providers)
- Historic registration data and that related to hosting transfers
- SSL certificate registration data.
They have also made an effort to come up with new methods of extracting data that is not available using ordinary means. “We cannot reveal details for obvious reasons, but in some cases, mistakes made by hackers during domain registration or server configuration help us discover their emails, pseudonyms, or backend addresses,” Volkov said.
An advantage for all threat hunters
The tool queries both the company’s internal databases and external sources of information (e.g., WHOIS, public sandboxes, etc.) and the whole network graph creation happens in mere seconds.
And everybody wins in the scenario where the tool is used by Group-IB’s clients.
“By giving visibility to our clients, we reduce our analysts’ load and get interesting feedback from our clients. When they do the analyses themselves, they may achieve results that are more interesting and relevant to them, and when they share those results with us, we have a better understanding about the threats that target organizations in their industry, sector or geographic region,” Volkov concluded.
“This allows us to tune our research capabilities and detection engines to improve our whole ecosystem and, on a global scale, it improves our detection, prevention and hunting processes for every client.”