How to avoid a costly enterprise ransomware infection
In most cases of human-operated ransomware attacks against enterprises, the hackers don’t trigger the malware immediately: according to FireEye researchers, in most (75%) of cases, at least three days passed between the first evidence of malicious activity and ransomware deployment.

What are the attackers waiting for? One of the reasons for the delay is the wish to spread the ransomware to many systems before running it. But they also like to wait for the weekend or at least the night, when there’s few or no employees – IT, IT security or others – to notice something is wrong and to react promptly to minimize the damage.
Ransomware targeting businesses
When ransomware first appeared as a new cyber threat, the targets were mostly individuals. It didn’t take long, though, for cybercriminals to realize that much larger sums can be extorted from businesses.
There are a number of cybercriminal groups and campaigns that focus on business organizations and they wield a variety of ransomware: Samas (aka SamSam), Ryuk, Bitpaymer, REvil, LockerGoga, Doppelpaymer and so on.
The ransomware is just the last piece of the puzzle, though – before it, the groups use other malware and techniques to breach company networks, perform lateral movement and keep their presence hidden until the time is right to inflict as much damage as possible.
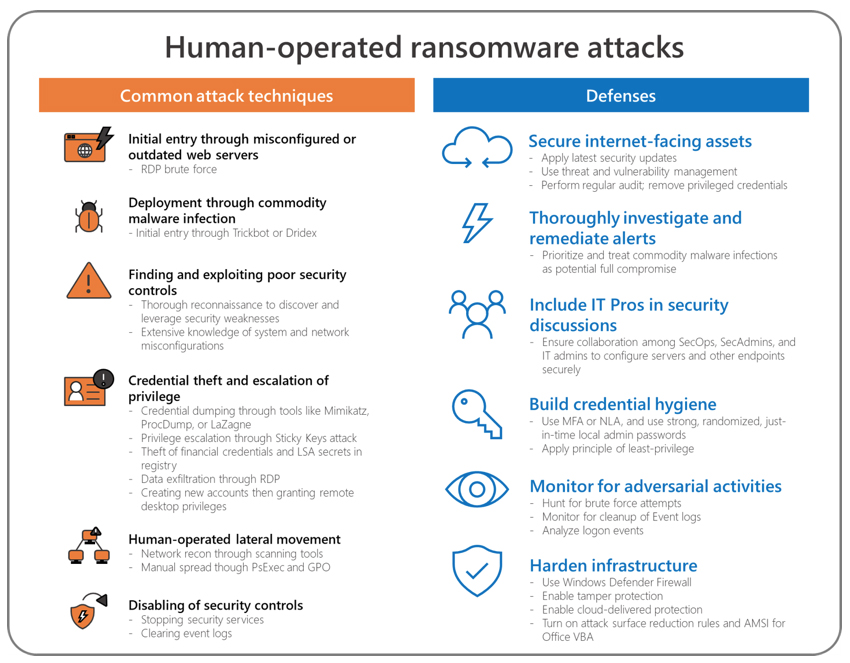
Helpful advice
Microsoft has recently published an in-depth analysis of the various groups’ modus operandi and offered advice on defenses that can help organizations fight this menace.
As both security companies have noted, the attackers usually gain a foothold in the target network by brute forcing RDP or other remote access solutions, or by delivering well-known malware droppers via email or drive-by-download attacks.
Both companies have also pointed out that, in most cases, defenders have a few days or even weeks to spot the intrusion before all hell breaks loose.
“Human-operated attacks involve a fairly lengthy and complex attack chain before the ransomware payload is deployed,” the Microsoft Threat Protection Intelligence Team explained.
“The earlier steps involve activities like commodity malware infections and credential theft that Microsoft Defender ATP detects and raises alerts on. If these alerts are immediately prioritized, security operations teams can better mitigate attacks and prevent the ransomware payload. Commodity malware infections like Emotet, Dridex, and Trickbot should be remediated and treated as a potential full compromise of the system, including any credentials present on it.”
FireEye researchers have offered the following mitigation recommendations:

As you may have noticed, among them are also actions that should help businesses respond better to IT emergencies outside of the usual working hours.