Magecart Group 8 skimmed card info from 570+ online shops
Your payment card information got stolen but you don’t know how, when and where? Maybe you shopped on one of the 570 webshops compromised by the Keeper Magecart group (aka Magecart Group 8) since April 1, 2017.

Magecart Group 8’s modus operandi and targets
The list of the online shops hit by the criminals has been released by researchers from Gemini Advisory, who managed to compile it after gaining access to the group’s dedicated attack server that hosts both the malicious payload and the exfiltrated data stolen from victim sites.
“Analysis revealed that the Keeper group includes an interconnected network of 64 attacker domains used to deliver malicious JS payloads and 73 exfiltration domains used to receive stolen payment cards data from victim domains.
Their research also revealed that:
- Over 85% of the victim sites operated on the Magento CMS, 5% WordPress, and 4% Shopify
- The group tried to disguise its malicious attacker domains as legitimate services (e.g., the attacker domain closetlondon[.]org attempted to imitate closetlondon.com) and tried to imitate popular website plugins and payment gateways
- The group occasionally used public and custom obfuscation methods to make the injected information-stealing JavaScript less noticeable and detectable
- The majority of victim e-commerce sites was hosted in the U.S., followed by the U.K., the Netherlands, France, India, etc.
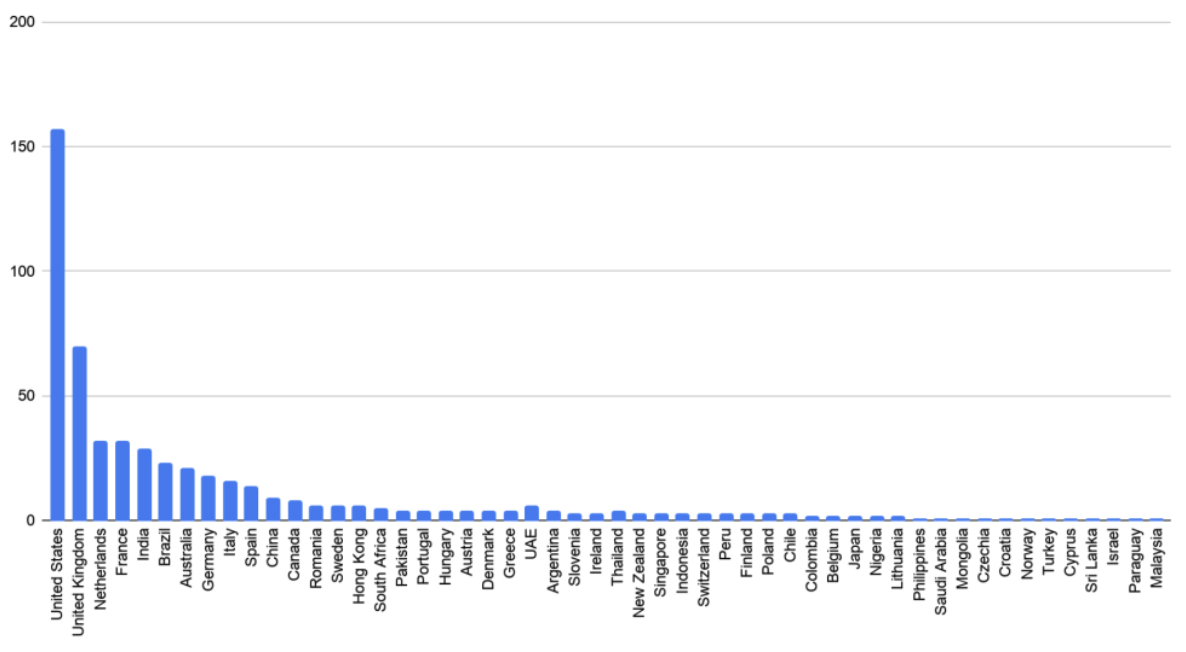
“The 570 victim e-commerce sites were made up of small to medium-sized merchants and were scattered across 55 different countries,” the researchers shared.
“Victims with the top Alexa Global Ranking received anywhere from 500,000 to over one million visitors each month and were responsible for selling electronics, clothing, jewelry, custom promotional products, and liquor.”
The attackers likely targeted small and medium-sized retailers because they are less likely to have a dedicated IT security team, to implement CMS and plugin patches promptly, and to have security measures in place and attack detection capabilities.
The profitability of Magecart attacks
The researchers estimated that the group may have generated over $7 million USD from selling compromised payment cards between 2017 and today.
“With revenue likely exceeding $7 million and increased cybercriminal interest in CNP [Card Not Present] data during the COVID-19 quarantine measures across the world, this group’s market niche appears to be secure and profitable,” they noted, and said that they expect the group to continue launching increasingly sophisticated attacks against online merchants across the world.
It is unknown if the group is state-sponsored or not. While we may think of Magecart groups as “mere” cyber criminals, Sansec researchers recently tied one of them to a North Korean APT group.
For the end users – i.e., the online shoppers – it’s all the same and, unfortunately, there is little they can do to protect themselves against the threat of getting their payment card info skimmed.
Avoiding smaller sites/shops might be a good idea, and so is using browser plugins that prevent JavaScript loading from untrusted sites, but there is no 100% guarantee.