Vulnerable TCP/IP stack is used by almost 200 device vendors
Researchers have discovered 14 new vulnerabilities affecting the proprietary NicheStack (aka InterNiche) TCP/IP stack, used in OT devices such as the extremely popular Siemens S7 PLCs.
“Other major OT device vendors, such as Emerson, Honeywell, Mitsubishi Electric, Rockwell Automation, and Schneider Electric, were mentioned as customers of InterNiche, the original developers of the stack. Due to this popularity in OT, the most affected industry vertical is Manufacturing,” Forescout noted.
The INFRA:HALT vulnerabilities in NicheStack
For the last two years, researchers from several companies took it upon themselves to probe the security of diverse TCP/IP stacks used in IoT, OT and embedded devices/systems, and to document their findings.
The NicheStack TCP/IP stack has been developed by InterNiche Technologies in 1996. Since its advent it has been distributed in several “flavors” by various OEMs and served as the basis for other TCP/IP stacks.
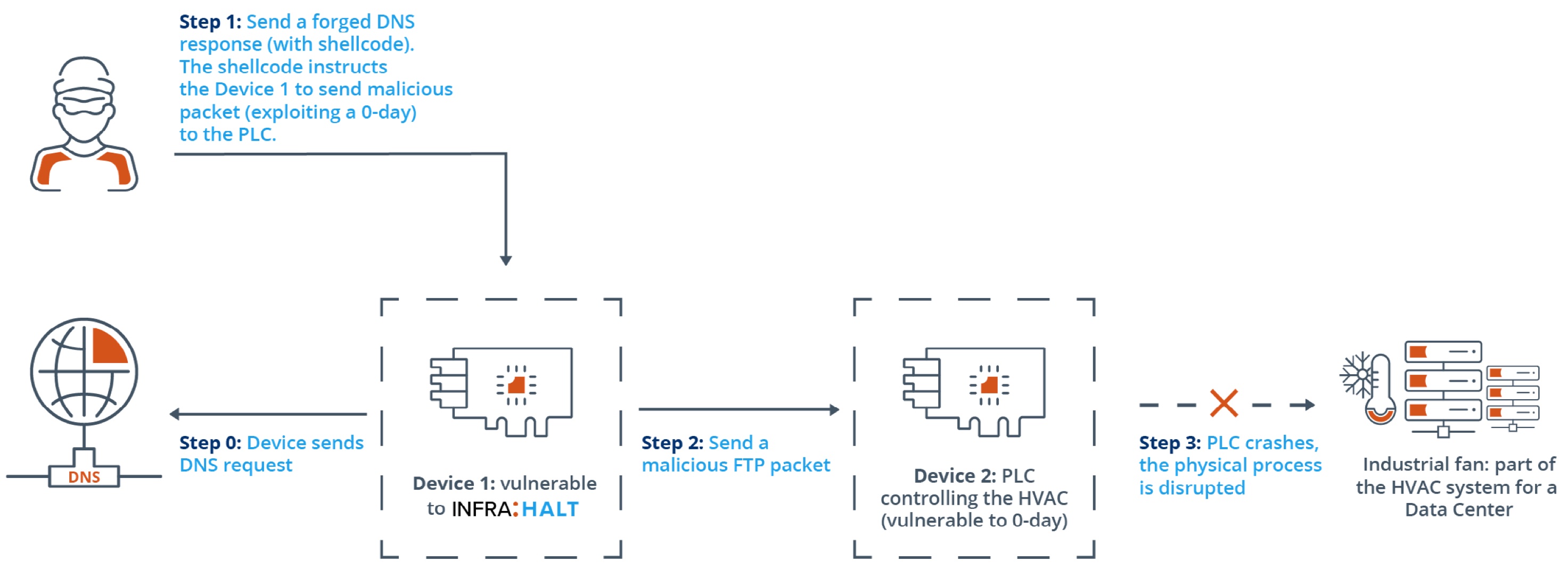
The 14 vulnerabilities found by Forescout and JFrog Security researchers in NicheStack have been collectively dubbed INFRA:HALT, and allow for remote code execution, denial of service, information leak, TCP spoofing, and DNS cache poisoning.
“If these vulnerabilities are exploited, bad actors can take control of building automation devices used to control lighting, power, security and fire systems, and programmable logic controllers (PLCs) used to run assembly lines, machines and robotic devices. This can significantly disrupt industrial operations and provide access to IoT devices,” the researchers explained.
“Once accessed, the stack becomes a vulnerable entry point to spread infectious malware across IT networks.”
Remediation and mitigation
InterNiche Technologies was acquired by HCC Embedded in 2016, and it is them who the researchers contacted with their discovery.
It took the better part of a year, but the company released patches for the affected versions of NicheStack (i.e., all versions before 4.3). The patches are available upon request and device vendors using the stack should provide their own updates to customers, the researchers noted.
Just how many devices out there are using one of the vulnerable stack versions is unknown but, according to an old InterNiche website, the stack is used by almost 200 device vendors, including most of the top industrial automation companies in the world.
Forescout offers an open-source script enterprise administrators can use to detect devices running NicheStack (and other vulnerable TCP/IP stacks).
Aside from implementing the patches, admins are urged to use network segmentation to mitigate the risk from vulnerable devices, and to monitor all network traffic for malicious packets that try to exploit known vulnerabilities or 0-days.
They also offered advice for improving the security of the devices/systems device vendors create and ship.