Review: Group-IB Threat Intelligence & Attribution (TI&A)
Organizations and enterprises that care about business continuity should have an established security program that needs to be reviewed on a regular basis. One of the hardest parts of creating a security strategy is deciding how to allocate resources – personnel and investments in security controls – in an efficient way. To do that we must know what security risks our organization is exposed to.
Estimating risk and needs in a future scenario is hard. It typically comes down to an expert’s biased ballpark estimation of potential conflicts and what damage these conflicts may cause to the organization.
Who is attacking our organization and those like ours? What tactics, techniques, and procedures (TTPs) do these threat actors use? How can we allocate these resources effectively to better defend ourselves? Changing the paradigm from an expert’s estimation of potential threat sources to a more data driven approach is not easy. Threat intelligence has long been touted as a solution to a lot of security problems, but it’s often difficult to accurately measure its value and effects because it also requires trained personnel who can make use of the information.
Nevertheless, high quality and comprehensive threat intelligence can help organizations in a lot of ways. It does not take experts out of the equation, but quality tools and threat intelligence information can help organizations plan and invest in defense mechanisms more effectively. One example of this synergy is using threat data related to similar company profiles to learn what threat events and sources we can expect and what damage they can cause. Organizations with a mature security posture that are not a target for opportunistic attackers can also use this data to more accurately assess their risk level based on the probability of them getting attacked and the impact attacks can cause.
The product reviewed here is Group-IB’s solution offering customer-tailored data on threats and attackers: Threat Intelligence & Attribution. TI&A aims to provide actionable threat data and make it usable to organizations and their analysts. The extensive functionality of the system helps customize it to the threat landscape not only relevant to a particular industry, but also to a specific company in a certain country.
Every specialist who uses TI&A now has access to the largest collection of dark web data, an advanced hacker group profiling model, and a fully automated graph analysis tool that helps correlate data and attribute threats to specific criminal groups in seconds. For this review, we had access to an instance of the Group-IB Threat Intelligence & Attribution system.
We tried to assess the novelty of threat intelligence data offered by the product when compared with TI provided by open sources. We wanted to discover whether information that is not available on the internet can be obtained from TI&A, and we analyzed how the threat data is presented and delivered to security analysts.
Group-IB Threat Intelligence & Attribution
Group-IB Threat Intelligence & Attribution is divided into six main parts (modules):
- Threats & Actors
- Compromised & Leaks
- Malware
- Attacks
- Suspicious IP
- Graph
The modules have intuitive names, but they also contain a lot more additional data and information that can be useful in specific use-cases, e.g., when analyzing a potential incident or learning about the context of a new attack.
Let’s see what they offer and how they can be used in the defensive security context.
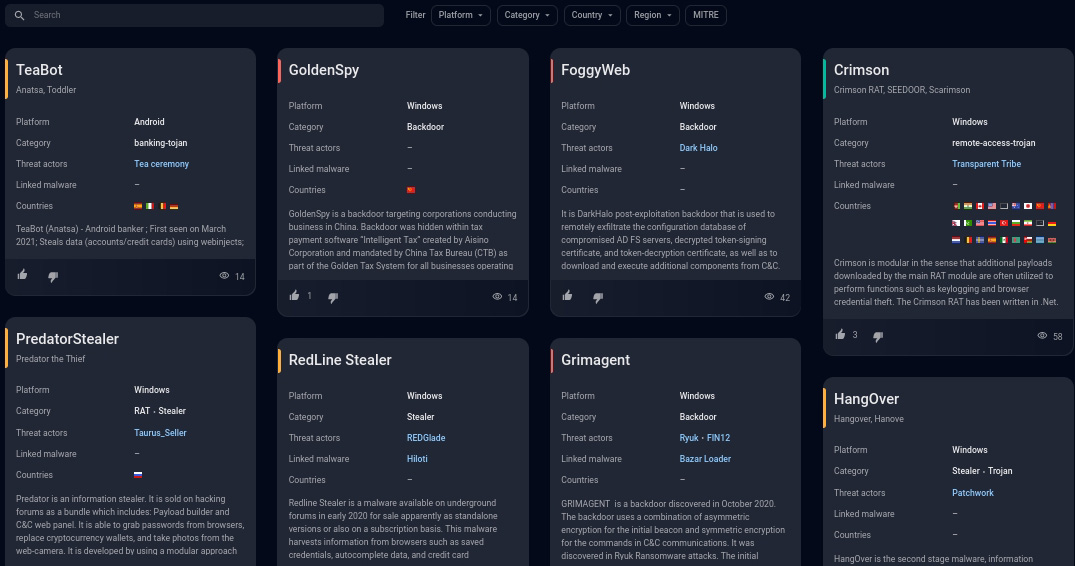
Figure 1 – Group-IB Threat Intelligence & Attribution welcome screen
Threats & Actors
Cyber criminals and Nation-state actors
Two main sections of the Threats & Actors module are Cyber criminals and Nation-state actors. The two categories show similar malware attacker “cards”, but the Cyber Criminals section includes opportunistic attackers and malware groups that usually attack victims for financial gain, and the Nation-state actors section contains threat groups that are tied to governments or are of an unknown origin, and usually perform advanced and stealthy attacks against specific, targeted victims.
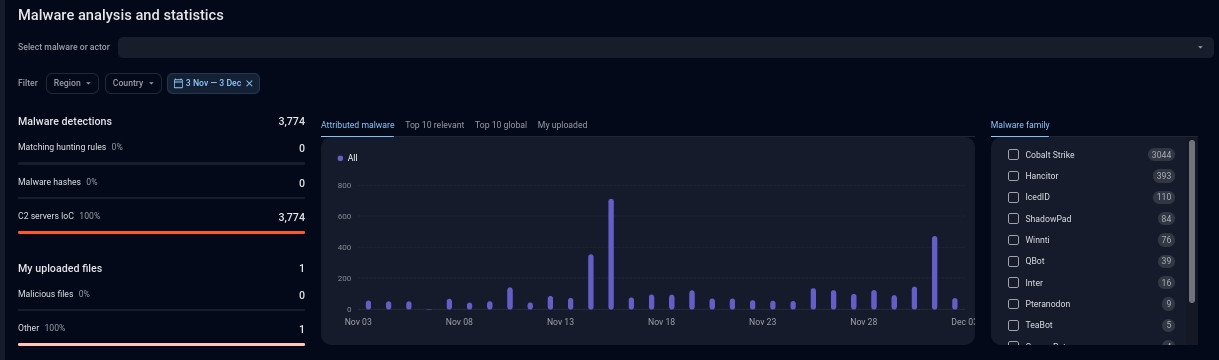
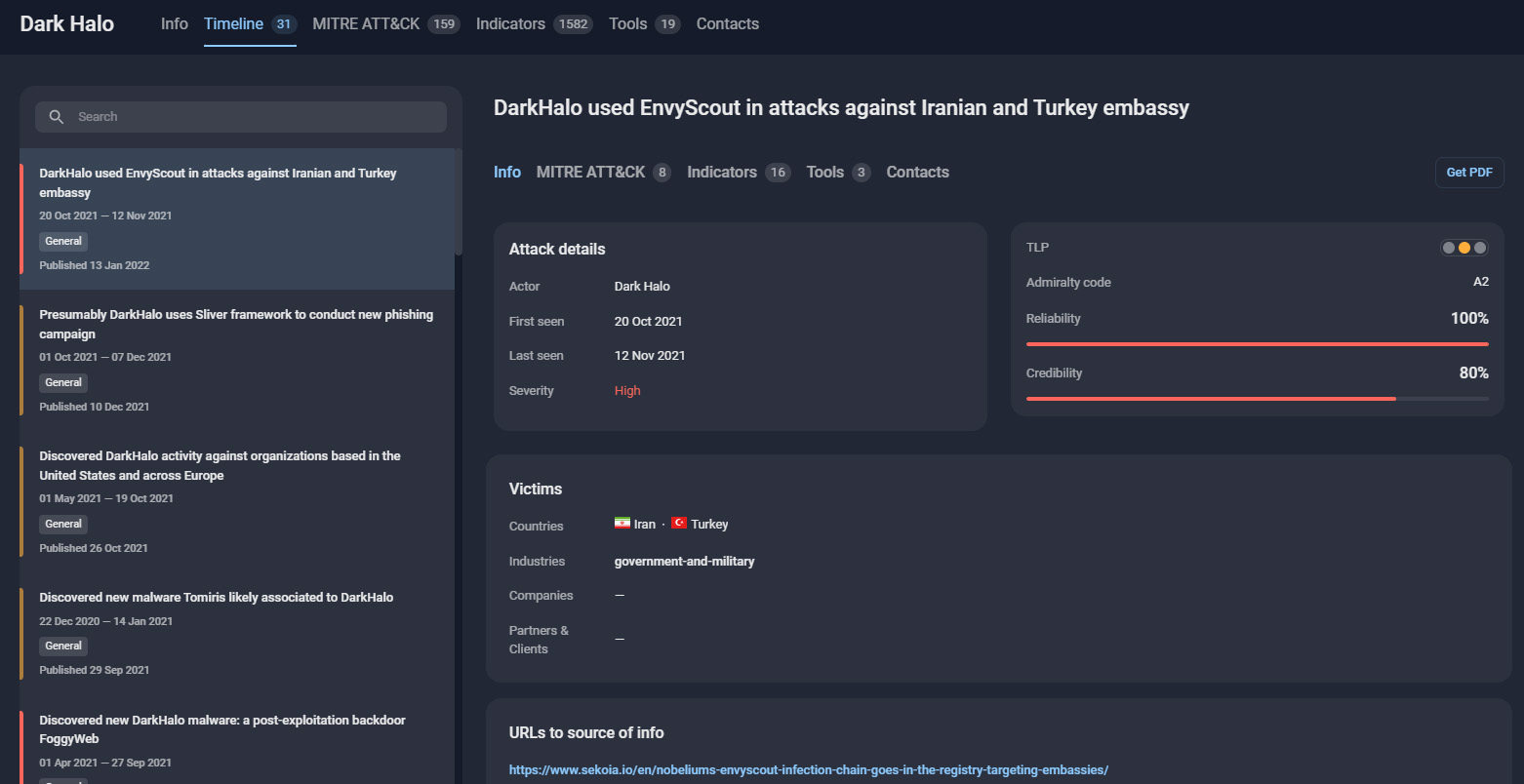
We were interested in what we can learn from TI&A about last year’s SolarWinds supply chain attack. A quick search in the Nation-state actors section for the term SolarWinds showed that the attack is attributed to the group called Dark Halo (aka UNC2452, SolarStorm, StellarParticle, Nobelium, etc.) (Figure 2).
Figure 2 – Overview of the threat actor Dark Halo, found by using “SolarWinds” as keyword
Here we can find Dark Halo’s latest activity (i.e., attacks that can be attributed to them). All threat actor cards contain information about tools, tactics, and procedures (TTPs) used in previous campaigns, mapped to the MITRE ATT@CK matrix (Figure 3).
Figure 3 – Dark Halo’s latest activity and their TTPs mapped to the MITRE ATT@CK matrix
The malware specimens shown in the Details pane can be drilled down and explored further. Doing this will lead you to the Malware module, where you can read about the technical details of malware capabilities. This section includes more than just indicators of compromise – there are also write-ups by Group-IB experts and other security analysts on the malware’s functionality, network signatures (Snort compatible rules) for IoCs, and Yara rules that can come in handy for tightening your security controls in case that threat actor decides to target your organization.
Every threat actor card comes with indicators of compromise like domains, IP addresses and file hashes that can be explored and used for further search. You can export IoC data from TI&A and use them in other tools or integrate them directly together for machine-to-machine intelligence sharing and process automation. Threat actors’ details show the tools and malware families used alongside with vulnerabilities exploited in previous attacks. You can also find email contacts, accounts and partners that are available from analyzed attack campaigns (like emails, social media, or forums).
The information on threat actors is usually summarized based on all analyzed data that Group-IB has available, but you can also see specific data per actor activity. Every threat data source is characterized by three scores (reliability, credibility, admirability) that give us a trust metric for the data that we are previewing or using. Some information can be sensitive, TI&A uses the Traffic Light Protocol (TLP) that based on four colors (white, green, amber, and red) gives you the confidentiality level of the information and the policy for disclosure. For example, information classified with TLP White is for unlimited disclosure and the most restrictive is TLP Red, which tells us that the information is only for participants, and it should be not disclosed to external parties or within your organization.
All threat actor data can be searched by these fields:
- IP address
- Domain
- File hash
- Country and region targeted
- Sector targeted
- MITRE ATT@CK TTPs
- CVE
In the example shown in Figure 4 you can see an advanced search query through which we aimed to find threat actors focused on encryption of business data and targeting the EU banking sector.
Figure 4 – Threat actors that encrypt data and target the banking sector in the EU
Dark web
The Dark web section works like a search engine for the hidden part of the web. You can search for the threat you are interested in on closed forums and other dark web locations where black hats and criminals gather to discuss attacks, leaks, or tools. One the biggest advantages is the customized hunting rules so that customers can add actors to their threat landscape. Alternatively, they can create customized hunting rules based on keywords or regular expressions to identify data specifically relevant to them, then track the actors and use the graph tool to perform attribution.
The search query enables you to filter dark web activity by user if the topic of interest is discussed by specific individuals or groups. A useful feature is the TI&A linkage of user accounts and traces to give better summaries of attacker activity. Group-IB’s dark web database includes all popular forums used by malicious groups and contains over 15 years of records, making it one of the largest in the industry. The section makes use of natural language processing to translate the text from any language, a useful feature when investigating foreign groups.
Figure 5 – Searching through dark web sources
Personal Threat Landscape
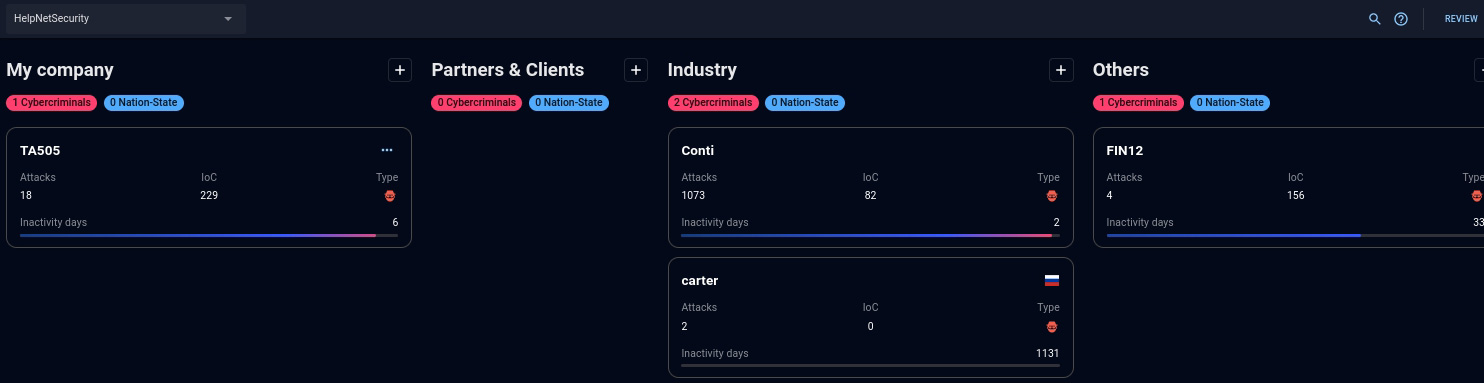
Threat Landscape is a customizable dashboard for your organization where, based on your research, you can choose threat actors to follow, as well as track tools or recent attacks. In other words, this is a practical shortcut for further analysis and call for action for your security program.
The “My company” section allows you to track the groups that are a direct threat to your organization. Partners & Clients allows organizations to monitor for potential disruption due to collateral damage, this is useful for manufacturing organizations that may rely on suppliers and distributors to remain operational. The Industry section monitors for groups that have experience attacking organizations like your own, cybercriminals often reuse TTPs against similar targets.
Figure 6 – The Threat Landscape dashboard
Group-IB analysts’ reports
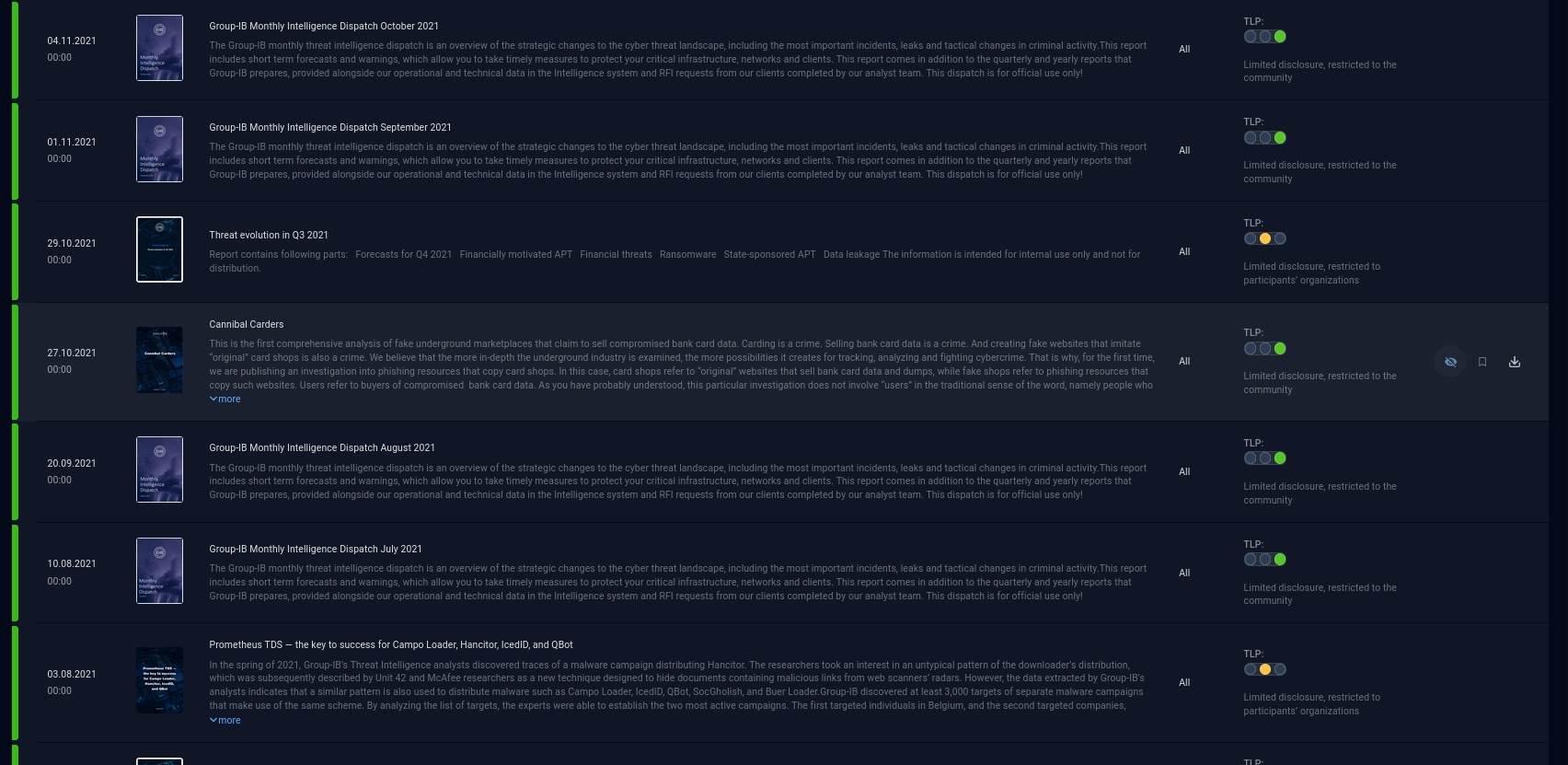
This section is a library of threat intelligence reports. Most of them are only available for Group-IB Threat Intelligence & Attribution customers due to a restricted sharing policy, like the fourth volume of its Hi-Tech Crime Trends 2021/2022 report “Cyberwarfare: state-sponsored operations in cyberspace.” The reports differ on several points: topic, depth, and publishing frequency.
Group-IB’s Monthly Intelligence Dispatch is a regular monthly publication that contains threats that were significant in the past month. This publication covers trends and relevant malware activity that was detected by Group-IB or other security organizations. Its purpose is to give a general overview of what has been happening but also to connect previous research activities with new information and further enrich data.
Threat Evolution is published on a quarterly basis and the content is very detailed. It contains all domains that the TI&A covers, with analyses, comments and insights provided by Group-IB experts. Most of the content is related (but not limited to) new malware, leaks, and attack vectors. Threat Evolution inspects and forecasts trends for financial threats, ransomware, state sponsored attacks and mobile malware.
Special edition reports are related to specific malware, campaigns, or actors. These are in-depth analyses of specific events and contain the whole story with technical details, timelines, detailed kill chains and usually uncover a major part of attacker infrastructure based on Group-IB data and Graph capabilities.
Figure 7 – Available reports in our TI&A instance
Compromised & Leaks
This module gives you complete access to structured information that Group-IB has collected from their activities (e.g., sinkholing botnets, disrupting attackers’ infrastructure in collaboration with law enforcement agencies).
It enables you to detect compromised accounts that are not available on standard open sources like Pastebin or forum posts. This information can help you when analyzing incidents and can also allow victimized companies to disable these accounts at an early stage of the infection process. This data can be useful for financial institutions such as bank card issuers and other services that are used for transfer or storage of funds (e.g., crypto marketplaces), but also to law enforcement agencies because they contain information about attackers’ infrastructure.
This module is divided in several sections, depending on the type of data collected: Accounts, Bank and masked cards, IMEI, Mules, Public leaks, Git leaks, and Breached databases.
Accounts – Contains compromised accounts. These accounts can be detected in various ways: from open and closed source breaches, by analyzing phishing kit configurations, by monitoring and disrupting malware operations, etc. This data can be used to prevent further compromises and preventively hunt for threats because you also get additional information if the compromise was related to a specific malware.
Bank cards and masked cards – Contains leaked bank card numbers that have been collected via infected websites, skimming equipment or compromised POS terminals. Group-IB detects these bank card numbers by monitoring closed sources, analyzing information stealers, and sinkholing malware traffic. With this information available, organizations can prevent fraud, notify the users that their card has been compromised, and thoroughly investigate the cause of compromise.
IMEI – Mobile malware is usually used to steal money or sensitive data from mobile phones. You can search for IMEIs of your organization’s mobile phones to pinpoint devices compromised by malware and stop the attack early in the kill chain. You can inspect all details about the mobile device (device model, mobile operator and locations, phone number) but also uncover the malware infrastructure that the phone has been part of. These data can be paired with your mobile device management system or SIEM. Financial institutions can use these data to enrich their anti-fraud systems.
Figure 8 – IMEIs of compromised mobile phones
Mules – Uncovers attacker payment infrastructure by extracting threat actor’s end-of-the-chain accounts used for cashing out money. This data can be used to augment financial institutions’ anti-fraud systems. Money mules use bank accounts, bank cards, e-wallets, and mobile phones.
Group-IB can successfully detect automatic transfer of funds from victims to mules by analyzing malware configurations or by exchanging data with law enforcement agencies.
Public leaks – Monitors public information exchange sites (e.g., Pastebin) for data related to your organization such as employee names, domains, IP addresses, BINs, internal names, etc. This list can be configured. After you detect an unwanted content share, you can easily forward it to your security team for impact analysis. In this section, you can detect leaks early, but also other misuses or potential threats or attacks that target your infrastructure.
Git leaks – Continuously monitors for sensitive data exposure related to your organization on GitHub and similar sites. You can also detect repositories mentioning your domains or IP addresses.
Breached databases – You can search for your email or your organization’s domain in existing leaks and breached databases, to discover accounts affected in public breaches. You can also find the original location where the dumps were published and search the threat actors that are behind the leak. This information can help you prevent the malicious reuse of employees’ passwords exposed during massive breaches. It can also be used to prevent successful password spraying, credential stuffing, or other brute force attempts that make use of compromised passwords.
Malware
The malware module contains descriptions of malware alongside relevant indicators and generated signatures (Yara and network intrusion detection rules), but also functionalities summarized in the MITRE ATT@CK matrix.
Malware profiles is a collection of popular malware profiles that can be filtered by category, platform, country or region targeted, and MITRE ATT@CK techniques. The malware profiles include IDS signatures (Snort format) and Yara rules that enable hunting for these specimens in internal networks. In addition, you can extract lists of indicators like IP addresses, domains, or file hashes that the malware is using or view them in the Graph section (clicking on the details enables you to transfer an indicator directly to the Graph view).
Every malware profile has an in-depth description of what it does, which techniques it uses, and the damage it can cause on compromised systems. The attack techniques are visible also in the ATT@CK matrix in a summarized view.
Figure 9 – Excerpt from Malware profiles
Malware detonation is a dynamic sandbox where you can execute a malware sample or URL, see how the specimen behaves in an isolated environment, and conclude (based on the final report) if it’s, in fact, malicious. We described Polygon functionalities in a previous review of Group-IB’s Threat Hunting Framework, and it seems that the Malware detonation feature uses a similar technology. The supported systems for dynamic analyses are Windows XP, Windows 7, and Windows 10. The supported formats range from classic portable executable files and Office documents to DLL, EML, HTML, PowerShell and Python scripts, VBS, WSH, etc.
Figure 10 – Short description of the Autoit backdoor used in the MONSOON campaign
Targeted trojans – A detailed analysis of interesting trojans, their settings and configuration parameters. Malware can contain unique keywords, IP addresses, or other relevant information to your organization so this feature enables you to find trojans that specifically target your organization. This is, for example, useful for banks or financial institutions where trojans target both users and infrastructure.
Phishing kits – Tracks newly registered domains and related certificates that show signs of phishing activities. Phishing kits usually target a specific brand or service (e.g., Google, Dropbox, Netflix, etc.) and target users that use these services to steal access information that can be later reused or sold on the dark web (and then reused). This feature scans for phishing content, analyzes and extracts information from phishing kits to detect misuses of an organization’s brand and to quickly block malicious activities.
This information can be integrated with Group-IB Fraud Hunting Platform, while Group-IB Computer Emergency Response Team (CERT-GIB) which is a member of the Forum of Incident Response and Security Teams (FIRST) and an accredited member of Trusted Introducer, can assist you in blocking phishing resources in different zones, meaning that threat actors can be slowed down and will not be able to access data they have stolen. Phishing kits are detected by scanning the internet for domain registrations and newly registered TLS certificates, but the data is also collected with distributed spam traps collecting new phishing and spam emails.
Vulnerabilities – Contains a feed of newly issued vulnerabilities with the related CVE (Common Vulnerabilities and Exposures) number, CVSS v3 score and vector, description and affected software. Some vulnerabilities also show exploits that are available online and threat actors selling or sharing exploits of the found vulnerability.
Figure 11 – Npm vulnerability (CVE-2021-43616)
Figure 12 – Example of exploit available online for a Microsoft Windows EoP vulnerability (CVE-2018-8453)
Attacks
The Attacks module is divided into three sections (by type of attack): Phishing, DDoS, and Deface.
Phishing contains an aggregated list of detected phishing attacks targeting a specific brand.
DDoS contains a list of denial-of-service activities filtered by the victim IP address. It shows the attackers’ C&C and type of attack used (NTP or DNS amplification, WordPress pingback, etc.). The sources of information on attacks vary: some attacks are found by scraping the internet but some are found via deployed sensors, sinkholed botnets, and intercepted from disrupted malware infrastructures.
Deface is a list of defaced domains on the internet. It also contains the original defaced content of the web site that is useful to track various attack groups.
Suspicious IP
Suspicious IP addresses are divided in three sections: TOR exit nodes, Socks proxies and Open proxies. In this section you can follow addresses that are not malicious but can be exploited as a proxy or jump hosts for performing attacks. You can search through the available IPs and monitor their availability through time.
Graph
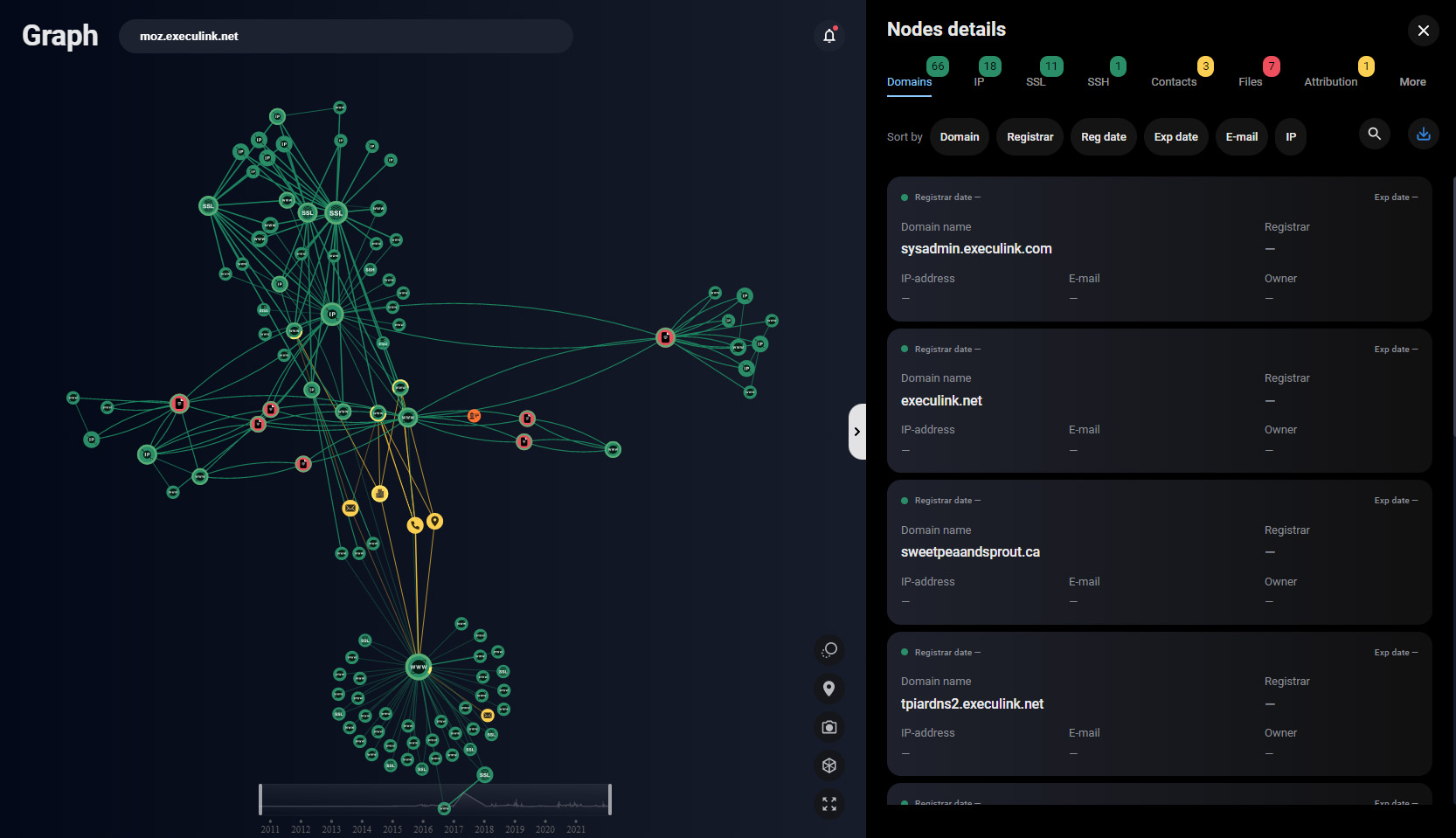
To echo a great thought of John Lambert: “Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win.” Group-IB’s patented Graph, which is also present in other Group-IB products like the Threat Hunting Framework and Digital Risk Protection, is a major advantage that defenders have for analyzing attackers’ infrastructure and finding connections to build a strategic defensive posture based on the historical records that the system holds.
But why is this saying true? Search engines’ output results are basically lists and easy to overlook, and do not give enough context when analyzing the causal and consequential links between the evolving attacks. To efficiently hypothesize and research, analysts need context about facts (in our case, indicators of compromise). Group-IB Graph enables you to find data about attackers and their infrastructure in a few minutes, and rewind through the timeline to see what happened when.
Figure 13 – Group-IB Graph showing context around a network indicator used by the group TA505
Analyst support
Threat Intelligence & Attribution includes direct access to Group-IB’s analyst teams. Users can request assistance for a wide range of cybersecurity queries via email or from within the solution’s interface. Using the interface, the user is guided through the process to create a request ticket, which is automatically triaged to the correct team. Group-IB has several groups of analysts that work in different fields of cybersecurity: a takedown request will be directed to the inhouse CERT team (CERT-GIB), whereas a request for information about a ransomware campaign will be sent to the Cybercrime Investigation Team. Group-IB has strict SLAs governing the response time for each type of request, providing the user with timely assistance.
Figure 14 – Group-IB analyst support request interface
Once a request is raised the ticket is available in a dashboard, allowing the user to easily track the progress of every ticket. The tickets can be made visible to other Group-IB Threat Intelligence & Attribution users within your organization, allowing multiple users to work on and follow up on requests. Lastly, the tickets are updated dynamically, allowing users to directly communicate with the analyst supporting them in real-time.
Conclusion
Organizations and CISOs that take security seriously need in-depth knowledge about potential attackers and emerging security trends in their industry. Being able to profile threat actors and cyber criminals and know their techniques, tools, and methods can become a competitive advantage of blue teams in the never-ending fight with attackers.
Group-IB Threat Intelligence & Attribution is a solution that provides all the needed operational and tactical information (alongside with Group-IB’s support) to start planning your risks in a more data- and adversary-centric approach. The system aims to provide its users with more than just information on potential threats and lead them further to identifying the adversaries who pose these threats. Having TI&A on board, corporate cybersecurity teams can promptly detect and track down a threat to a specific cybercriminal, as well as detect the instances of the sales of databases relating to the company, compromised user accounts, as well as company data trafficked by insiders.
This solution is probably not “plug and play” and it will require additional effort by your security team when it comes to tracking and interpreting information that can be found in it, however Group-IB does have extensive API, STIX and TAXII documentation and an integration team there. An advantage is that besides threat intelligence data, you also have at your disposal a malware detonation platform that can come handy if you don’t want to manage your own.
The threat intelligence data contains the usual: malware hashes and samples, IP addresses and domains. But TI&A also contains the unusual: mobile phone IMEIs, compromised bank card numbers, decrypted malware configurations, and leaked databases. This unexpected information, which is usually derived from joint malware / infrastructure disruption efforts by Group-IB and law enforcement agencies, is the best part of the TI&A. This data will be useful to financial institutions but also other organizations that offer services that attackers can use (e.g., telecoms), and can be further enriched using the Graph Analysis.
Although tracking attacker and threat trends is useful, exact attribution of novel attackers can be hard due to attackers’ efforts to outsmart analysts by using cloaking techniques that can imitate other attacker groups. TI&A uses a Big Data approach that is useful for following popular trends and data to enhance existing security mechanisms in organization via data enrichment of SIEM, anti-fraud systems or malware prevention systems. Still, Group-IB manages to collect and process a lot of data by algorithms and humans to deliver attribution data with reliability and credibility scores.
The monthly and quarterly reports available in TI&A will be interesting and informative for higher management, as they provide a glimpse of potential threats that their organization can encounter. In conclusion, if you need a threat intelligence provider, Group-IB will offer you a wide range of products, but also information that can speed your risk assessment and threat intelligence programs.