Review: Hornetsecurity 365 Total Protection Enterprise Backup
Hornetsecurity 365 Total Protection Enterprise Backup is a cloud-based data protection and security solution that provides protection against spam, malware, and other advanced threats, combined with backup and recovery features.
The solution is specifically designed for and fully integrated with Microsoft 365, offering email and data protection to customers. Its main objective is to create a simple, secure, and hassle-free environment.
Installation
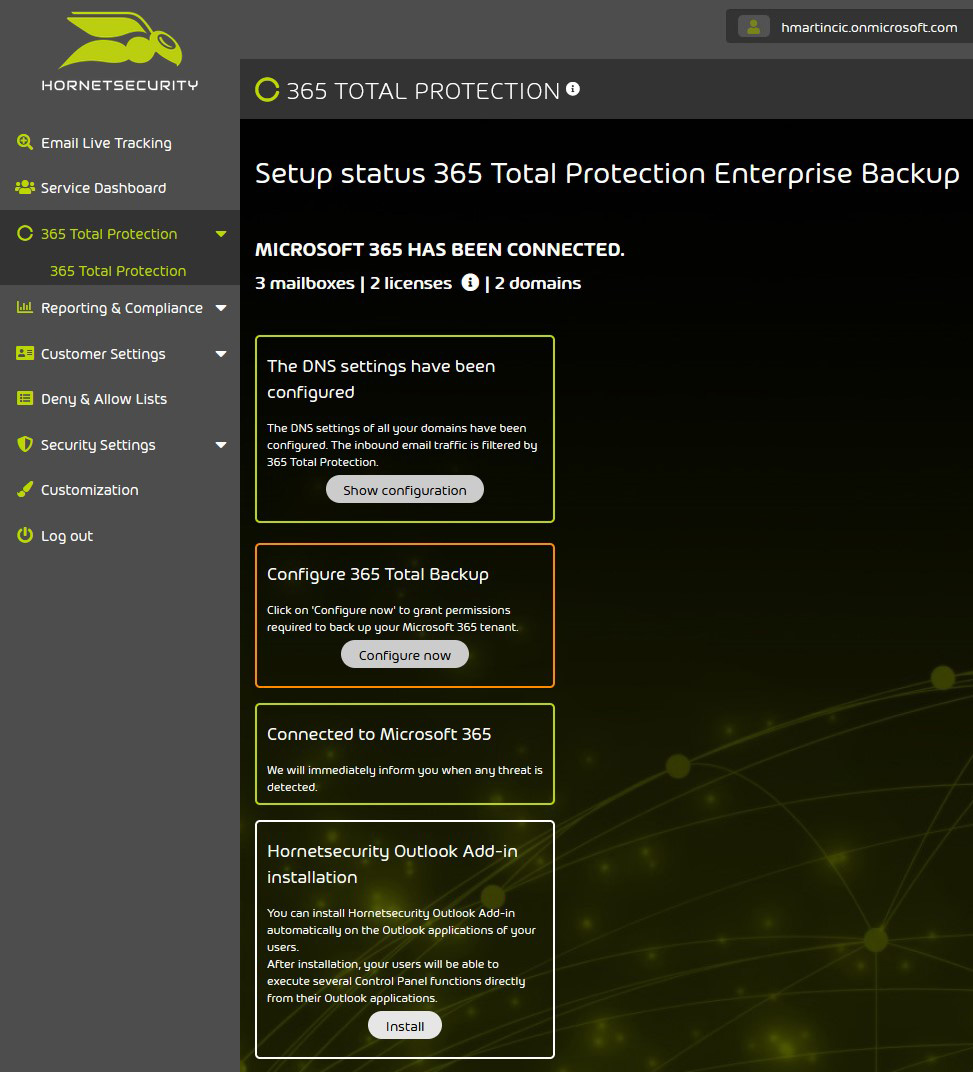
It all starts with the onboarding wizard, where you, as the IT admin, must enter the primary domain for your tenants and your global admin credentials to access the Microsoft tenants. The only “manual” part of the process is the transfer of the DNS record. The solution is activated once you finish onboarding and switch the appropriate MX records over to Hornetsecurity.
Figure 1 – Permissions required for the solution to work
Figure 2 – Options after finishing the installation
Hornetsecurity Outlook Add-in
After finishing the initial setup, you can install the Hornetsecurity Outlook Add-in on your users’ Outlook applications. The add-in can be used as a quick tool for classifying information related to “Allow” and “Deny” lists, by reporting messages to the Control Panel directly. Additionally, it allows administrators to review “Allow” and “Deny” list entries created by each (user) account. Unfortunately, the archive interface (i.e., logging in to the Control Panel) from within Outlook is only available on Windows Outlook clients – it is not supported on Mac or the Outlook web interface.
Figure 3 – Users get notified of the add-in installation
Figure 4 – Add-in options for a quarantine report delivered to a user
Security settings
This is where all email protection modules are listed and additional services are activated. I will summarize the options that can be fine-tuned.
Though I found the default settings suitable, Spam and Malware Protection – the solution’s main service – can be customized. As admin, you may want to look up the available options under “User rights” and give access to (or limit) the options available to your users via the Outlook add-in.
Figures 5 and 6 – Spam and Malware Protection options
Hornetsecurity recommends activating Advanced Threat Protection because it will add multiple elements to help combat the more sophisticated attacks coming via email:
- Real-Time Alert sends notifications to the personnel in charge if emails that were received by users of the domain later turn out to be dangerous.
- URL Rewriting will create “click protection” for any links within emails, by replacing them with custom links that will redirect users through the solution’s Web Filter. Any email that went through this process is clean. If it has a link that is weaponized later and the user clicks on it, a rescan of the link is initiated and the user is still protected by the Web Filter.
- Targeted Fraud Forensics Filter blocks targeted (personalized) malicious emails without malware or links.
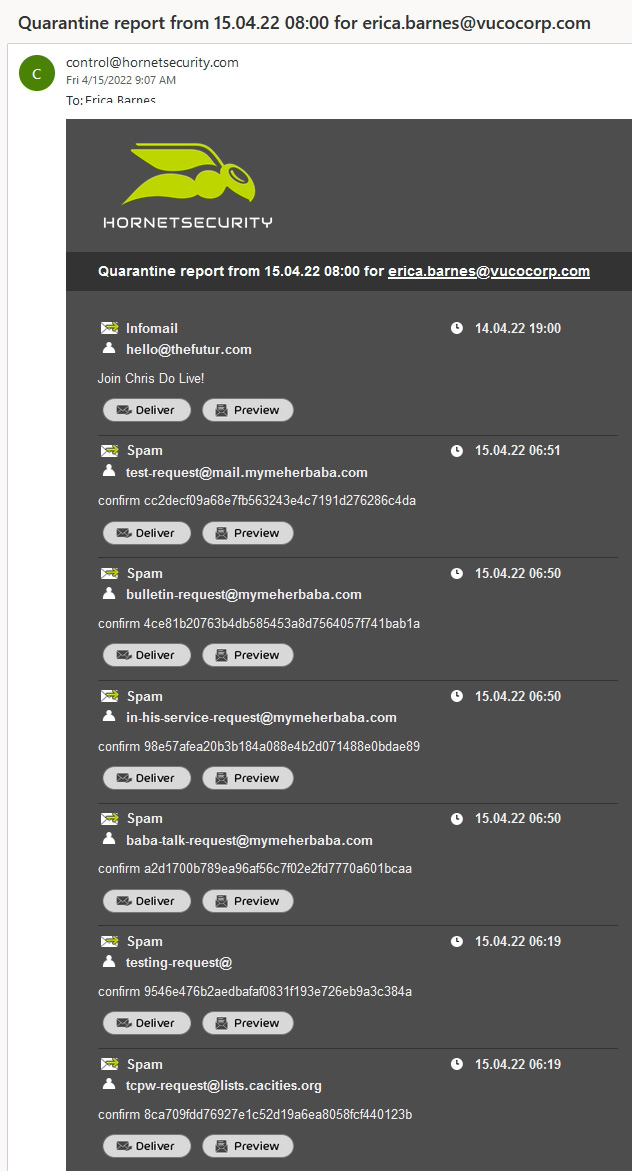
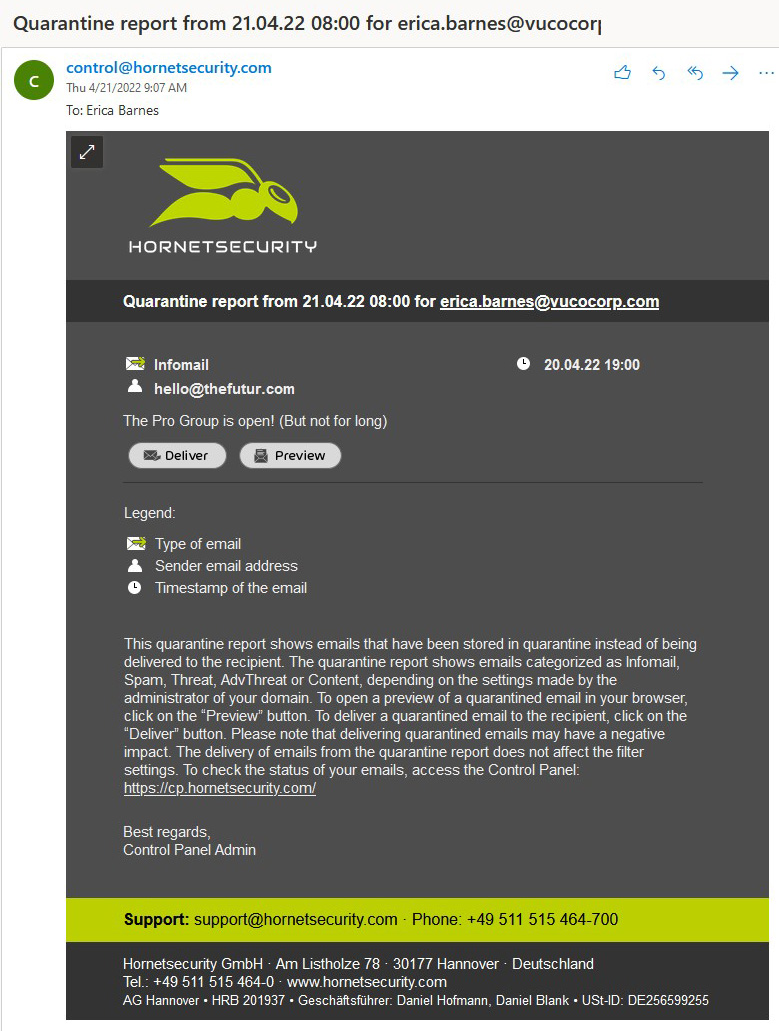
Another option you might want to switch on is the Quarantine Report, which can be activated for an entire customer or for specific users.
When Quarantine Report is configured for the customer’s domain, one of these two options can be selected: either the users will receive and can access the quarantine reports intended for them, or a quarantine report that contains quarantined emails of the whole domain will be sent to an email address specified by the administrator.
After quarantine criteria is configured by the admin, quarantine reports will be created for potentially malicious emails that have been stored in quarantine instead of being delivered to the recipient.
Depending on the settings made by admin, the quarantine report can show emails categorized as Infomail, Spam, Threat, AdvThreat or Content. Users can “release” some categories of emails to themselves without logging in to the Control Panel. Emails classified as Spam and Infomail can be “released” by the users to their own mailbox, while those falling into the Threat, AdvThreat or Content categories cannot, because additional admin review is needed for further action.
Figure 7 – IT admins’ choices for the Quarantine Report option
Figure 8 – A general quarantine report delivered to a user
Figure 9 – A specific quarantine report delivered to a user
The Signature and Disclaimer feature enables the admin to set up email signatures and disclaimers across the domain for all users. Different signatures and disclaimers can be set up for various inter-organizational groups (e.g., different departments, regional offices, and so on).
New signature/disclaimer entries can be created via the embedded HTML editor and data can be pulled from Azure AD. Admins can also embed banners, links, images, social media icons, etc. Once a signature/ disclaimer entry is created, admins can preview how it’s going to look like before applying it to domains, users or a specific group.
Figure 10 – A preview of a custom signature and disclaimer
Several methods for Email Encryption are offered:
- TLS (Transport Layer Security) – Encrypts emails between the outgoing and incoming mail server (always activated)
- EmiG (E-Mail made in Germany) – A form of TLS encryption with requirements for the TÜV-certified communication partners, their server security and the certificates used for encryption
- S/MIME – A standard for encrypting and signing MIME emails. The certificate authority (CA) assures the validity of the email address and sender’s name
- PGP (Pretty Good Privacy) – An asymmetric encryption standard using public and private keys
- Websafe – Allows users to send encrypted emails to recipients who do not support any other supported encryption methods
Figure 11 – Email Encryption options
Hornetsecurity says that, in their experience, customers mainly use the TLS and Websafe options.
When using Websafe, the emails are sent to a portal (and stored there for 3 months). The recipients receive an email with credentials to access the portal. Registration is completed after the recipients enter a PIN (delivered via phone), a password and the answer to a security question. Once created, the account is valid for all future emails received through the Websafe portal.
Depending on your preferred email setup, additional Email Authentication methods (SPF, DKIM, DMARC) can be enabled:
Figure 12: Email Authentication options
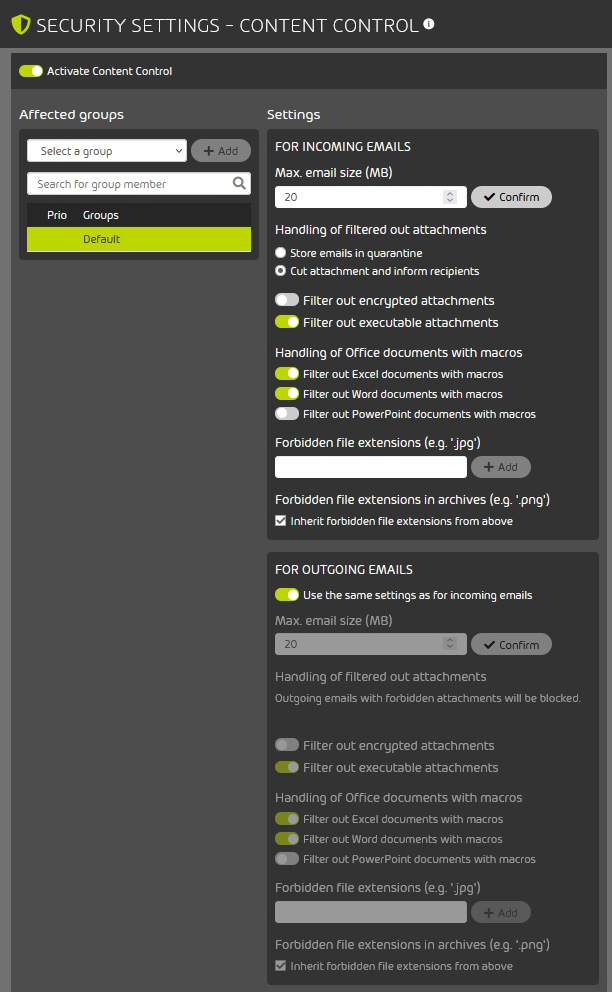
The Security Settings also include options for Content Control for incoming and outgoing emails. Admins can set email size limits, filter out executable or encrypted attachments, Office documents with macros, etc.
Figure 13 – Content Control options
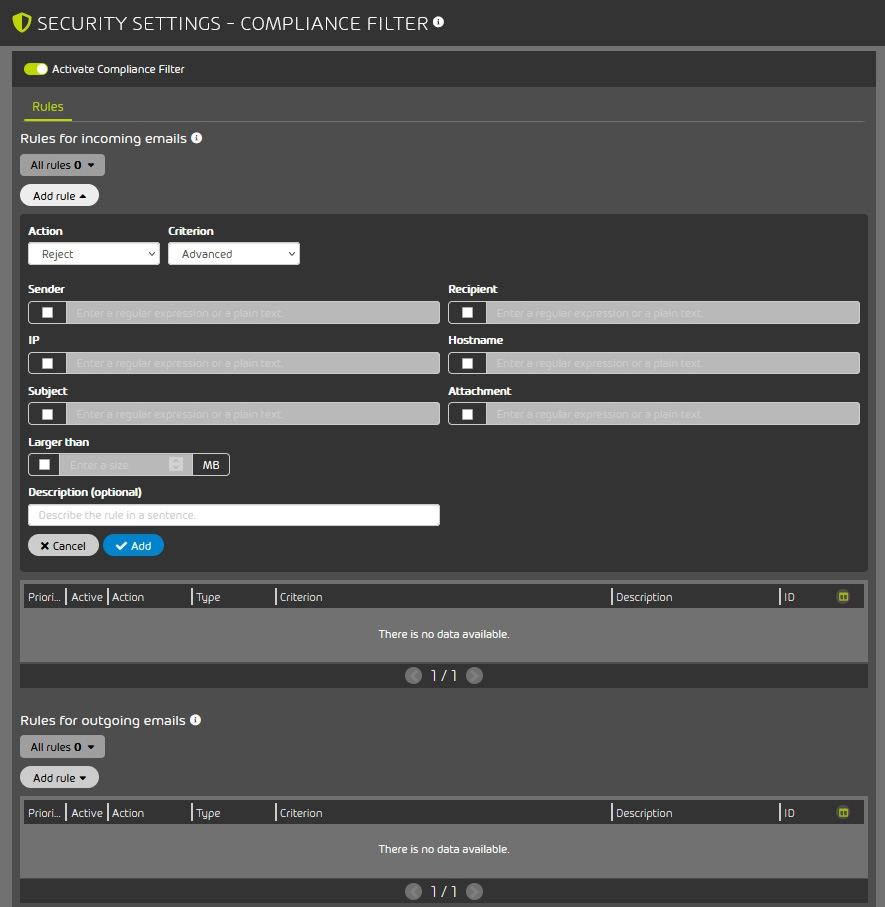
Additional filtering rules can be created via the Compliance Filter to classify incoming emails as Clean, Spam or Threat. Admins can also make it so that specific emails are rejected, redirected through a different server, or forwarded to other recipients.
Figure 14 – Compliance Filter options
Archiving: After the service is activated, from that point on all received and sent emails on the connected domain are archived for 10 years. The option can be deactivated for individual domains, groups and/or users. By adding an exception, the archiving period can also be changed, or archiving entirely deactivated.
Continuity Service allows users to continue to receive and send emails even if the email server fails. This could come in handy during disaster recovery.
Figure 15 – Continuity Service options
Reporting and compliance
In this tab, admins can view and generate Email Statistics according to specified criteria, see a report of attempted attacks during a specified time frame via Threat Live Report, and track user activities in the Control Panel via Auditing 2.0.
Figure 16 – Threat Live Report
365 Total Backup
This solution provides backup and recovery for Microsoft 365 mailboxes, OneDrive accounts, SharePoint document libraries, Teams chats, and Windows-based endpoints. Storage is provided and maintained by Hornetsecurity and is unlimited in size with a “forever” retention period (i.e., until deleted by the user). Due to the possible sensitive nature of the backed-up data, Hornetsecurity offers full GDPR compliance, with an additional layer of security: the data stored on the company’s servers is encrypted using AES-256 encryption.
The following data is backed up:
- Mailbox: Emails, calendar entries, contact addresses
- OneDrive: All files stored in the user’s OneDrive for Business account
- Teams Chats: Teams chats for users and groups within your organization, including any files that are shared during the conversations
- SharePoint: Files and communication in SharePoint document libraries, along with access permissions
The Data Restore function supports the following scenarios:
- Data can be restored to the original mailbox/OneDrive account/SharePoint site
- Data can be restored to a different mailbox/OneDrive account/SharePoint site within the same or in a different organization belonging to the same customer
- Data can be restored to a ZIP archive, which can then be downloaded
- Data can be restored as a PST file (this option is available only for mailboxes)
- Microsoft 365 Teams chats can be restored to a new team within Microsoft Teams or restored to HTML files, which can then be downloaded
- By using Granular Restore, the admin can select specific elements inside a specific backup snapshot to be restored or downloaded (a download link to the password-protected restored content will be sent via email).
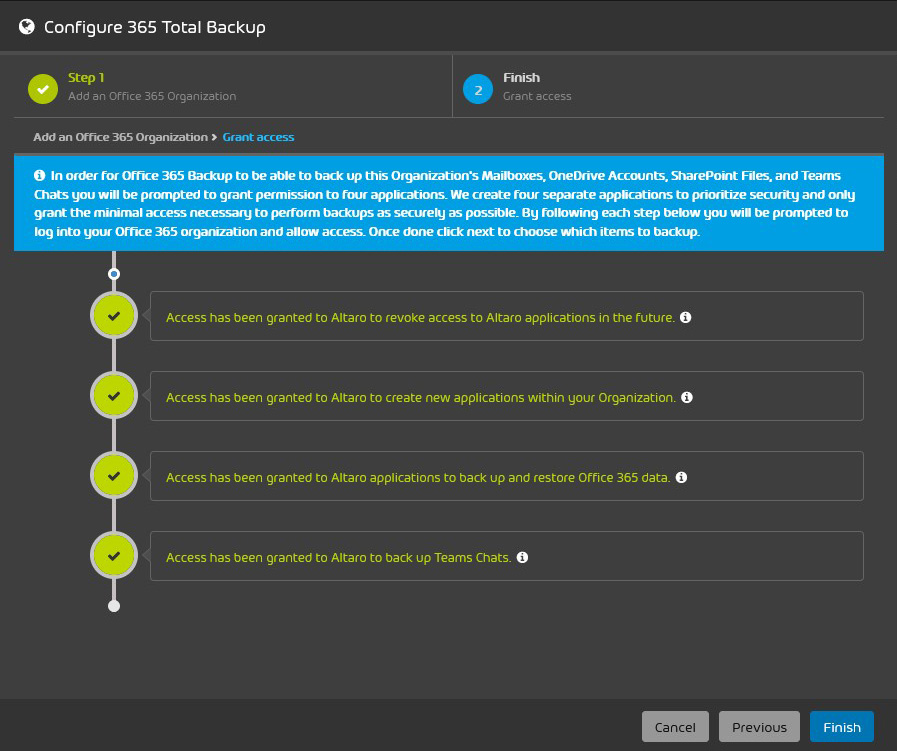
In my test, the activation of 365 Total Backup went without a hitch. The information you must provide is minimal and you must grant access and permissions to Altaro Office 365 Backup (Hornetsecurity acquired Altaro, a company that specialises in backup and recovery software, in 2021).
Figure 17 – The information required for configuring 365 Total Backup
Figure 18 – Granting permissions to Altaro applications
After being presented with a user-friendly dashboard, the discovery of new users and mailboxes, groups and SharePoint document libraries starts automatically. It can also be triggered via a button later.
Figure 19 – The 365 Total Backup dashboard
Figure 20 – Users and backups
Restore actions are done through wizards or Granular Restore, enabling admins to restore a whole account or a single file from a backup snapshot.
Figure 21 – Granular Restore
Figure 22 – The options for restoring mailboxes
During my testing, I haven’t had any issues while backing up or restoring mailbox and OneDrive data – it all went smoothly and quickly. Of course, the recovery speed depends on the size of the dataset that needs to be restored. The download of the data needed for backup integrity verification went as fast as my ISP allowed.
One last thing to mention is that Hornetsecurity 365 Total Protection Enterprise Backup includes support for (Windows) endpoint backup.
The Endpoint Backup Manager must be installed on a Windows server. This EBM server doesn’t have to be on the same network as the workstations, but a connection between them is required.
After installing the EBM, it can be linked to the Cloud Management Console, from which the admin can setup backup policies and deploy the endpoint agents to the workstations. The EBM is used to configure and coordinate the backups and set the storage configuration. The storage needs to be Azure Cloud Storage, provisioned and managed by an MSP or the customer company. This is different from 365 Total Backup, for which Hornetsecurity provides and manages the storage.
Verdict
In my opinion, Hornetsecurity 365 Total Protection offers a level of email, OneDrive and SharePoint protection that should be enough for most Microsoft 365 users.
During my testing of the email protection features I have encountered no false positives. Emails were correctly categorized and user categorization from the email client or quarantine report worked flawlessly. I loved the user-friendly interface and appreciated how simple it is to handle the solution.
Customers should assess for themselves whether they need some of the additional mail services such as Email Encryption or Continuity Service.
The Enterprise Backup side of the solution covers all enterprise backup needs for the most common user-generated type of data inside a Microsoft 365 environment. It delivers a simple solution that can be set up in under 15 minutes (if you already defined organizational backup policies).
If you are running a Microsoft 365 environment and you care about email protection and backup, I can recommend this solution. It provides a centralized backup solution, adds extra security layers over Microsoft 365 services, and offers value for both users and IT administrators.