Product showcase: The Stellar Cyber Open XDR platform
As enterprises find themselves dealing with ever-increasing threats and the boundaries of their organization disappearing, security teams are more challenged than ever to deliver consistent security outcomes across the environment. Stellar Cyber aims to help lean enterprise security teams meet this challenge day in and day out.
Stellar Cyber addresses the needs of lean enterprise security teams by providing the capabilities typically found in NG-SIEM, NDR, and SOAR products in a single platform, with a single license for all capabilities, included. This consolidated approach enables customers to eliminate security stack complexity and ramp new security analysts faster.
Stellar Cyber services enterprise customers in all major industries, with customers across Europe, Asia, Australia, Japan, South Korea, and Africa, providing security for over 3 million assets. In addition, stellar Cyber claims after deployment, users see up to 20x faster mean time to respond (MTTR), a bold claim.
Below is a short walkthrough of a few typical use cases to show the value of our solution.
Before we begin
Before digging into the platform, here are a few things you should know about Stellar Cyber:
- Bring your own EDR: Stellar Cyber could be classified as an Open XDR as it ingests all types of data to identify incidents; however, it is not an extension of an EDR product. Conversely, Stellar Cyber offers pre-built integrations to any major EDR vendors meaning you can use whatever EDR you with Stellar Cyber, no rip and replace required.
- Automation is key: Automation is one of our key value propositions. We all know the industry is moving fast in its adoption of automation. Still, it’s important to note that we are not aiming to reduce your security staff since most of our customers are running lean security teams. So we have implemented intelligent automation across the entire platform.
Responding to an Incident from the Home page
From the Stellar Cyber home screen, you can see top incidents and riskiest assets and the Open XDR Kill Chain. Stellar Cyber developed the Open XDR Kill Chain to accommodate new attacks only visible within the Open XDR platform. By clicking on any segment of the kill chain, you can access the threats associated with that portion of the attack chain. So, for example, when I click “Initial Attempts,” I get access to this screen.
Here I can see alerts with the stage “Initial Attempts” set by Stellar Cyber automatically. Further, I see more information about the alert when I click “View” on any of the alerts. So, initially, users can view summary graphs or click “more info” to read about the incident, dig into the details, and review the raw data behind this incident and the JSON, which I can conveniently copy to a clipboard if necessary.
While the presentation of the data in Stellar Cyber is easy to understand and logical, the product’s true power is on full display when I click on the “Actions” button. As you can see below, I can take my response actions right from this screen, such as “add a filter, trigger an email, or take external action. Clicking on external action, I get another picklist. When I click on Endpoint, I get a long list of options from contain host to shutdown host.
When clicking on an action, like contain host, a configuration dialog displays where I can select the connector to use, the target of the action, and any other options required to initiate the action chosen. So, in summary, security analysts, especially junior ones, will find this workflow very useful in that they can a) easily dig into the details of an incident from the home screen and b) review even more details by going deeper into the data, and c) take a remediation action from this screen without writing any scripts or tinkering with a code.
The enterprise onboarding new analysts can use this view initially to familiarize them with the platform handling low-priority incidents so other analysts can work on the more critical incidents.
There is much more to learn about this Stellar Cyber platform, so let’s look at another path to investigating incidents.
Exploring Incidents
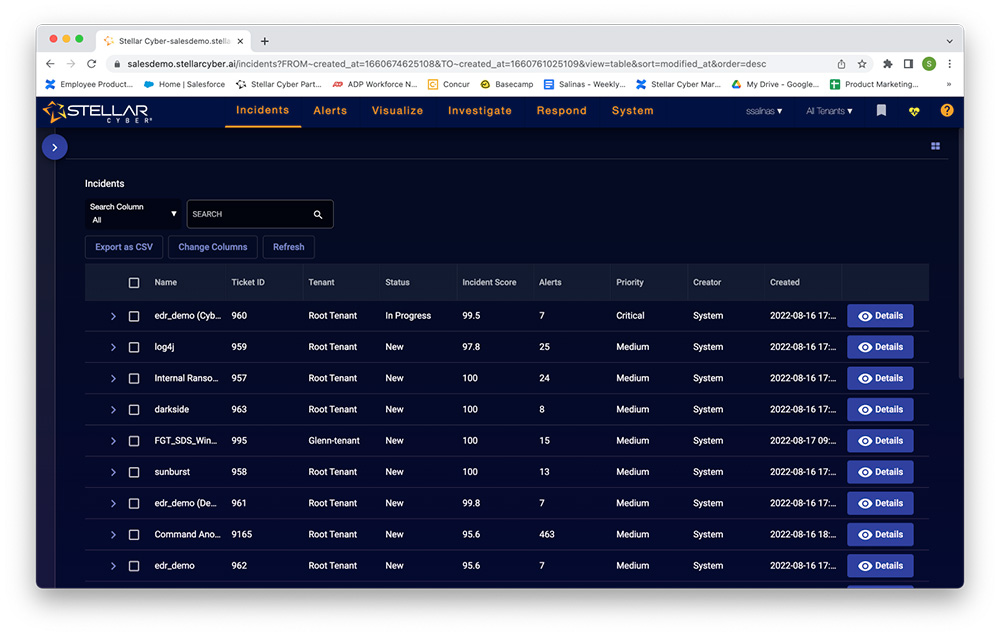
Instead of clicking on the Open XDR Kill Chain, I will click on the menu item “Incidents” and get this screen in return.
When I clicked on the carrot in the blue circle, it expanded a filtering list that enabled me to hone in on a specific type of incident. I go directly to the details button to see what I can find in this detail view.
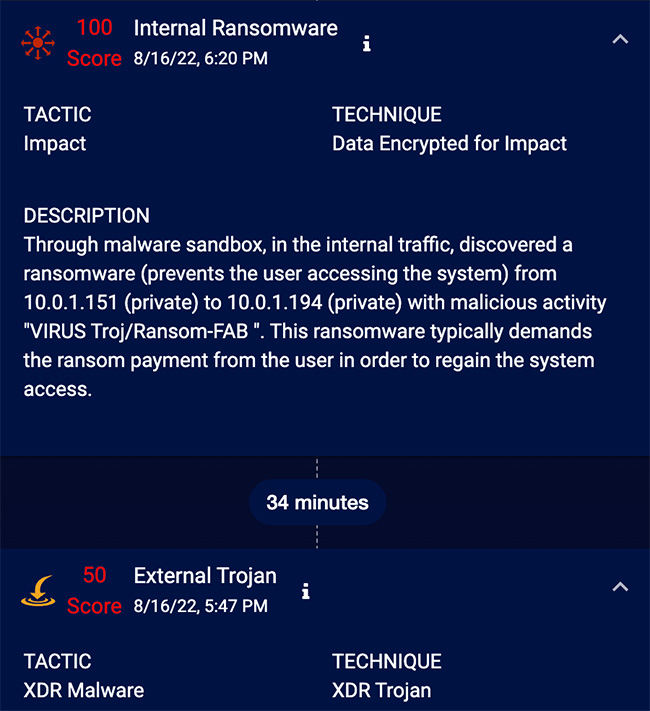
Now I can see how this incident occurred and propagated across multiple assets. Further, I can automatically see the files, processes, users, and services associated with the incident. There are different ways to view this data as well. For example, I could switch to the timeline view to get a readable history of this incident, like below:
When I click on the small “i,” I get to a familiar screen.
So, analysts who are used to working from a list of alerts may like to start their investigations from the incidents page. For the enterprise, this view is also beneficial as it automatically shows all alerts associated with this incident in a single view. Of course, you can limit this view by analysts, region, etc.
Stellar Cyber offers enterprises a way to streamline their security operations without writing special scripts or doing anything out of the ordinary. However, before closing out this walkthrough of Stellar Cyber, let’s look at one other feature, Threat Hunting.
Threat Hunting in Stellar Cyber
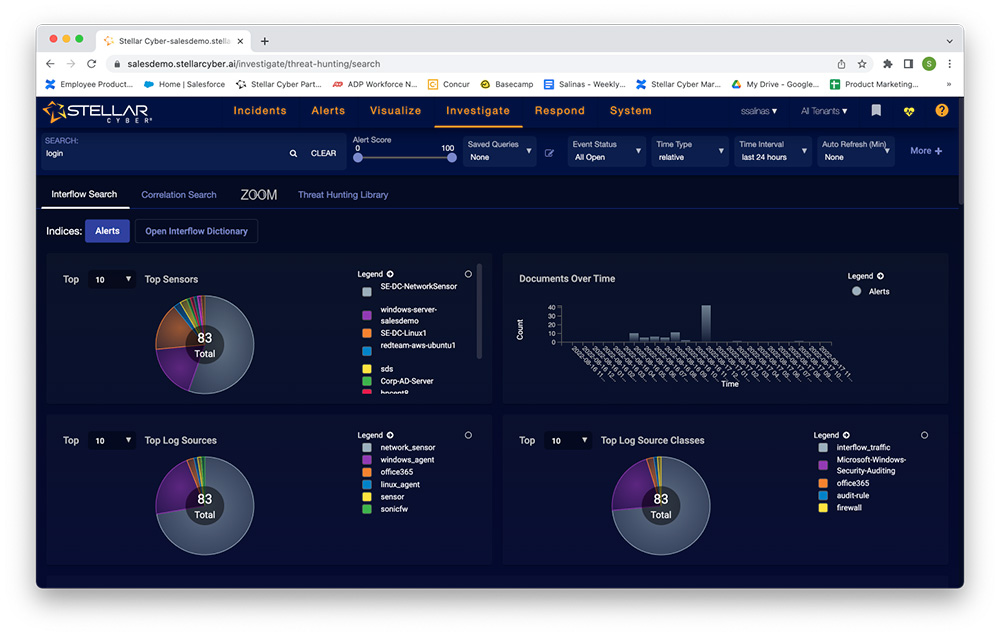
When I click on “Threat Hunting” from the menu, I see this screen.
From here, I can see some summary statistics and initiate a new threat hunt by typing a term into the search dialog box on the top right of the screen. For example, if I type “login,” the stats change dynamically. Scrolling down the screen, I also see a list of alerts that have been filtered based on my search term. I can also initiate a “correlation search” under the search dialog box. When I click that, my screen changes to this.
I can load a saved query or add a new query. Clicking the add query, I see this query builder. This builder allows me to search Stellar Cyber data for threats that went unnoticed. In addition, I can access the threat hunting library to access previously saved queries.
You can also create response actions that execute automatically if your query returns any matches.
So, in summary, Stellar Cyber offers a simple threat hunting platform that doesn’t require you to build your own ELK stack or be a power scripter. For enterprises, you now have a way to add a threat hunting element to your security team without adding a hard-to-find threat hunter to the team.
Conclusion
The Stellar Cyber Open XDR platform enables the lean enterprise security team to transform their operations without significantly changing their existing security stack. By deploying Stellar Cyber Open XDR, security analysts can stop chasing alerts and start stopping attackers in their tracks.
To learn more visit www.stellarcyber.ai.