Advantech’s industrial serial device servers open to attack
Three vulnerabilities in Advantech’s EKI series of serial device servers could be exploited to execute arbitrary commands on the OS level.
Source: CyberDanube
The vulnerabilities
Serial device servers are networking devices that “network-enable” serial devices (e.g., printer, climate control system, etc.) in an industrial automation environment.
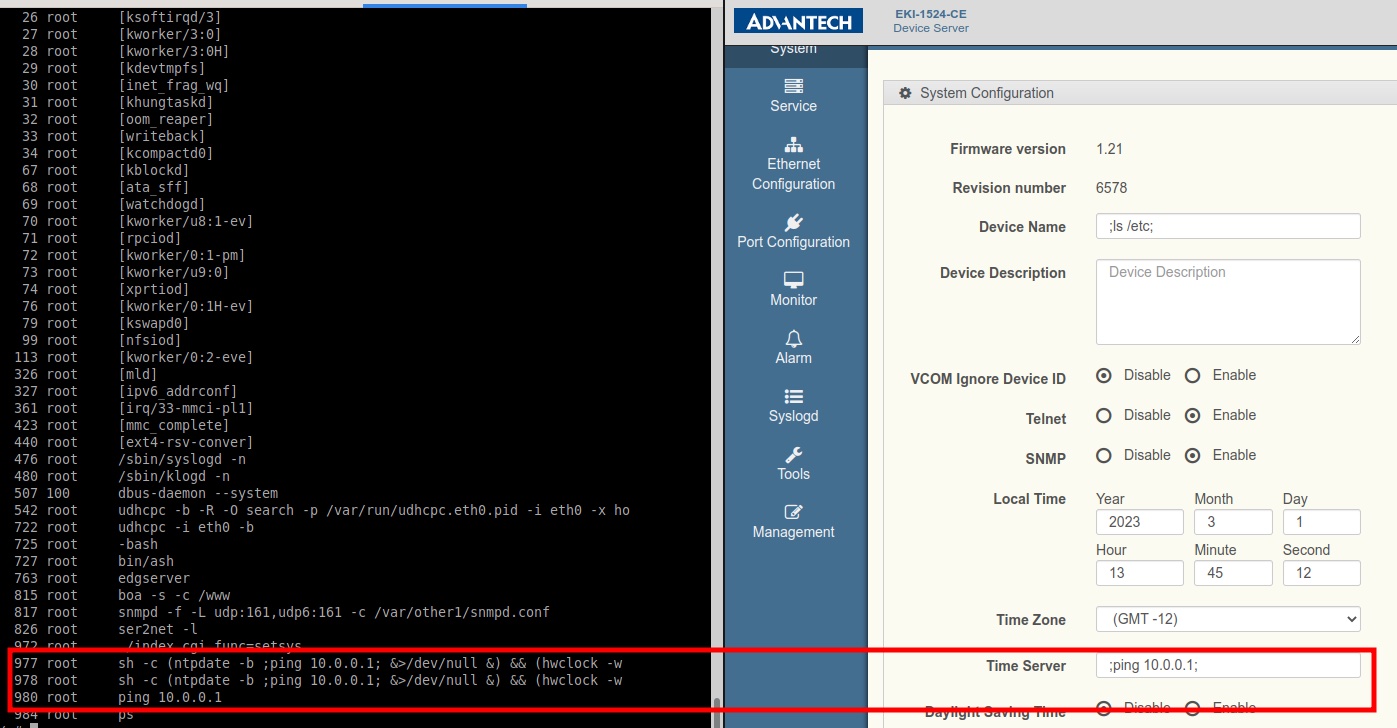
CyberDanube researchers Thomas Weber and Sebastian Dietz have analyzed the firmware of Advantech’s EKI-1521-CE, EKI-1522-CE, and EKI-1524-CE series of serial device servers, and unearthed two command injection and one buffer overflow vulnerabilities, all of which can be triggered via POST request.
“The two command injection vulnerabilities are triggered in a similar way. First, an attacker sets the name of the NTP server in the interface and intercepts the HTTP message before it can be sent to the device. Second, an attacker modifies the message by replacing the desired name by a system command, enclosed by “;” characters. Last, the attacker sends the message to the device, whose Operating System (OS) executes the command with root permissions. The same attack can also be done via the device name, but it requires an additional reboot to trigger the final command execution,” the researchers told Help Net Security.
“The buffer overflow vulnerability can be exploited by simply removing the length check from the NTP server input field and fill it with an overlong string (as shown in the PoC). This can lead to command execution.”
All three vulnerabilities require authentication before exploitation, which is not a problem if default settings are used, but gets harder if admins have changed the password.
“These devices are usually not internet-facing, as they are usually part of OT networks,” the researchers pointed out. “However, if previously hijacked in the internal network, they can be abused as a gateway to the network.”
Fixes, PoCs available
Advantech has confirmed the existence of the vulnerabilities in v1.21 and earlier of the devices’ firmware. Customers are advised to upgrade to the latest version available to plug those security holes.
The researchers have released PoC exploits for the flaws.
“Our PoCs for the command injection vulnerabilities just trigger a ping command, or a screen listing (on the device’s serial port). Our PoC for the buffer overflow just triggers the memory leak itself, but has no dedicated effect. It only creates a zombie sub-process,” they explained.