Requests via Facebook Messenger lead to hijacked business accounts
Hijackers of Facebook business accounts are relying on fake business inquiries and threats of page/account suspension to trick targets into downloading password-stealing malware.
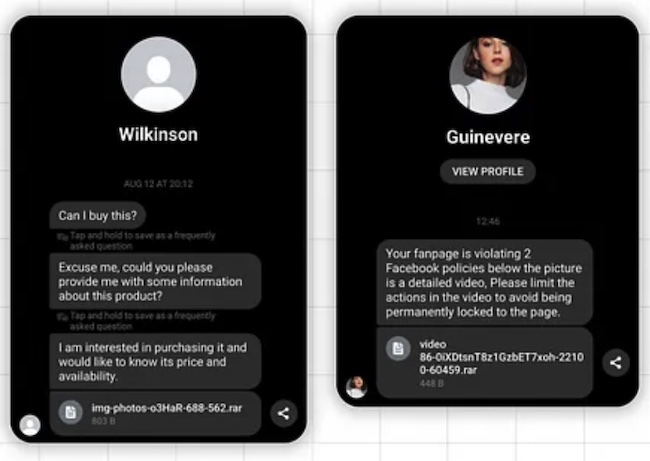
Examples of phishing messages. (Source: Guardio Labs)
The campaign
Hijacked Facebook business accounts a great way to reach a broad audience with ads and more scams.
“Additionally, individuals who own Facebook business accounts are likely to have other highly valuable accounts on other platforms such as banking, e-commerce, ad platforms, and much more — all available to grab directly from their browser’s cookies and password files,” says Guardio Labs researcher Oleg Zaytsev.
In this specific campaing, the crooks are contacting business account owners via Facebook Messenger. They ask them more information about a specific product or to remove a photo or a video from their Facebook page – and ostensibly send the photo or video in question.
Only, the file is a RAR or ZIP archive that, once executed, starts a multi-stage process that finally delivers a powerful Python-based stealer, which sends the stolen cookies and login credentials to a Telegram channel operated by the criminals.
“One last bonus in this case is that the script actually deletes all cookies after stealing them. This locks the victim out of her/his accounts, giving the scammers time to hijack their session and replace the password — so the victims won’t be able to revoke the stolen session or change the password themselves,” Zaytsev explained.
The malware was also initially able to pass undetected by most antivirus and endpoint security solutions.
A high success rate
There is a thriving underground economy related to selling hijacked social media business accounts and it seems that Vietnam-based threat actors are among the most active participants.
“The threat actors hold an army of bots and fake Facebook accounts as well as a listing of millions of business accounts, pages, and managers — sending away over +100k phishing messages a week to Facebook users around the world,” Zaytsev noted.
Guardio Labs estimated that 1 out of 250 account owners targeted in this campaign have downloaded the malicious file and that 1 out of 70 of those got infected with the malware.