ProSpy and ToSpy: New spyware families impersonating secure messaging apps
ESET researchers have found two Android spyware campaigns aimed at people looking for secure messaging apps such as Signal and ToTok. The attackers spread the spyware through fake websites and social engineering.
Researchers identified two previously unknown spyware families. Android/Spy.ProSpy poses as upgrades or add-ons for the Signal app and the discontinued ToTok app, while Android/Spy.ToSpy pretends to be the ToTok app itself. The ToSpy campaign is still active, supported by command-and-control servers that remain online.
ProSpy execution flow (Source: ESET)
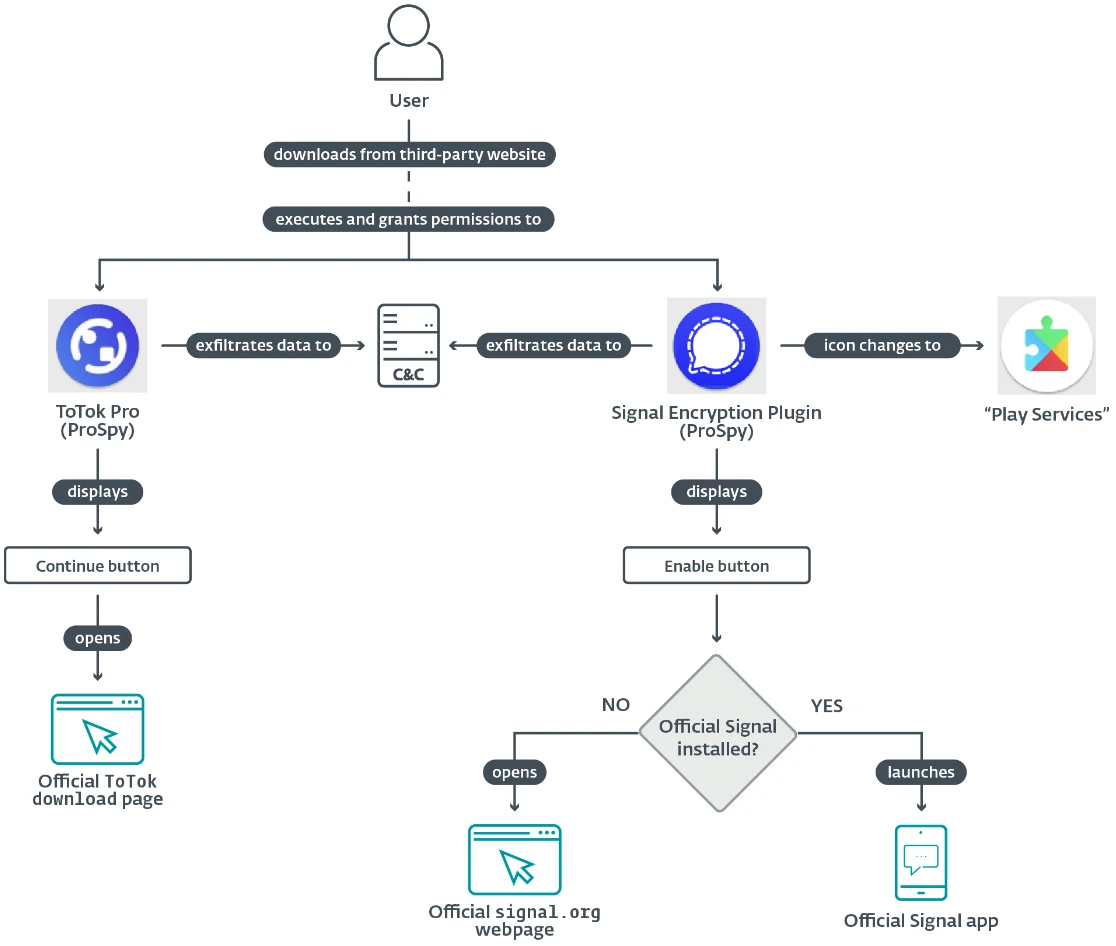
“Neither app containing the spyware was available in official app stores; both required manual installation from third-party websites posing as legitimate services,” explains ESET researcher Lukáš Štefanko, who made the discovery. “Notably, one of the websites distributing the ToSpy malware family mimicked the Samsung Galaxy Store, luring users into manually downloading and installing a malicious version of the ToTok app. Once installed, both spyware families maintain persistence and continually exfiltrate sensitive data and files from compromised Android devices. Confirmed detections in the UAE and the use of phishing and fake app stores suggest regionally focused operations with strategic delivery mechanisms.”
Distribution through fake websites
The ProSpy campaign was discovered in June 2025, and evidence suggests it has been active since 2024. The spyware is distributed through three fake websites that mimic the Signal and ToTok platforms. These sites offer malicious APKs presented as a Signal Encryption Plugin and ToTok Pro. One of the domains ends with ae.net, which may indicate the campaign is aimed at people in the United Arab Emirates (UAE).
During the investigation, the researchers found five more malicious APKs built on the same spyware codebase. They posed as an updated version of the ToTok messaging app called ToTok Pro. ToTok was a free messaging and calling app developed in the United Arab Emirates. It was removed from Google Play and Apple’s App Store in December 2019 over surveillance concerns. Since most of its users are in the UAE, it is likely that ToTok Pro is aimed at people in that region, who may be more willing to download apps from unofficial sources.
How the spyware works
When launched, both spyware apps ask for access to contacts, SMS messages, and files stored on the device. If the user grants these permissions, ProSpy begins sending data in the background. The Signal Encryption Plugin collects device details, stored SMS messages, and contacts, and also exfiltrates other files such as chat backups, audio, video, and images.
In June 2025, ESET telemetry detected another previously unknown Android spyware family. The activity came from a device located in the UAE, and they named the malware Android/Spy.ToSpy. Further investigation uncovered four fake distribution websites pretending to be the ToTok app. Because of ToTok’s popularity in the region and the impersonation tactics, it is likely that the main targets are users in the UAE and nearby areas. The spyware runs silently in the background, collecting and sending contacts, device information, chat backups, images, documents, audio, video, and other files. ESET believes the ToSpy campaign likely began in mid-2022.
“Users should remain vigilant when downloading apps from unofficial sources and avoid enabling installation from unknown origins, as well as when installing apps or add-ons outside of official app stores, especially those claiming to enhance trusted services,” advises Štefanko.